In this blog, we will solve one of the labs which is vulnerable to the Stored XSS. First, we will see the functionality of the lab, then find the vulnerable of it. So, let’s get stared with the lab.
Table of Contents
- Introduction
- What is Stored XSS Attack?
- Brief detail of Stored XSS Attack
- Impact of Stored XSS Attack
- Mitigation for Stored XSS Attack
Introduction
So, as from the title we can easily know that the lab is Stored XSS, so let’s understand that what is Stored XSS Attack?
What is Stored XSS Attack?
A Stored Cross-Site Scripting (XSS) vulnerability is a serious security flaw in web applications that allows attackers to inject malicious scripts into a website’s database, which are later served to users when they access specific pages.
Unlike Reflected XSS, where the payload is reflected immediately in the user’s browser, Stored XSS involves the persistent storage of malicious scripts on the server, posing a greater threat as the injected code affects all users who access the compromised content.
Brief detail of Stored XSS Attack
Stored XSS exploits the improper handling of user input by web applications. Typically, user inputs, such as comments, forum posts, or messages, are stored in a database without adequate validation or sanitization. If an attacker manages to inject malicious scripts into these inputs, the scripts become part of the stored content.
When other users view the affected content, the injected scripts are served from the server, executing in the context of the victim’s browser.
Now, we have gone through Stored XSS Attack, let’s get start with the Lab.
Click on the link, to access the lab Stored XSS into HTML context with nothing encoded.
To start the lab, click on the “Access the Lab button”.
Now, you will see the lab. And check all the functionality of the web application.
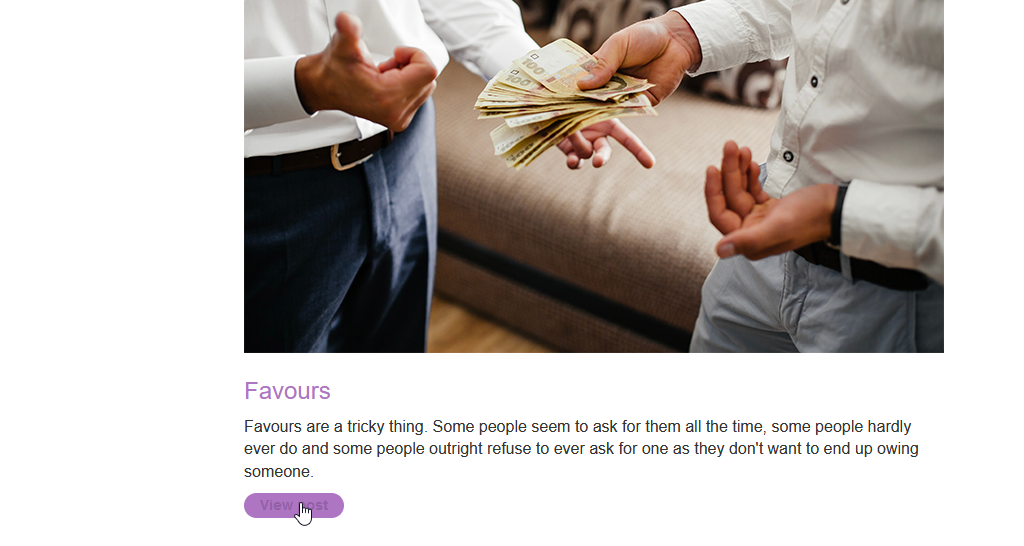
Step 1: So, here on the home page there is no search button. Let’s view one of the posts. Click on the View Post Button.
Step 2: There is comment section of the post. Try the malicious payload in the input field.
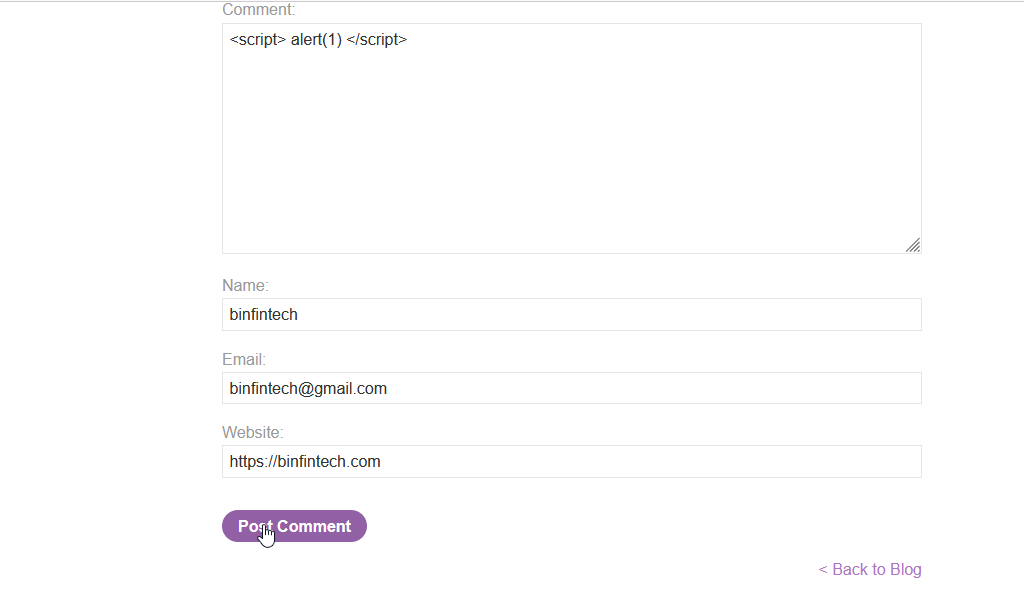
So, above mentioned image, I had injected malicious code into the input field.
Congrats, you have solved the lab successfully. If u follow the above step properly.
So, this how the injected payload work.
The process of a Stored XSS attack can be illustrated through a comment form on a blog:
1. Input of Malicious Script:
- An attacker posts a comment containing a payload like
<script> alert(1) </script>.
2. Inadequate Input Validation:
- The web application fails to properly validate or sanitize the comment input and stores it directly in the database.
3. Script Stored in Database:
- The malicious script is now stored in the database as part of the comment content.
4. Serving the Malicious Script:
- When other users visit the page with the compromised comment, the stored script is retrieved from the database and served to their browsers.
5. Script Execution:
- The victim’s browser executes the script in the context of the website, leading to the execution of arbitrary code, potentially stealing sensitive information or performing unauthorized actions.
Impact of Stored XSS Attack
The impact of a Stored XSS attack is broad and can result in significant harm to both individuals and organizations. Here are some of the key impacts:
Data Theft and Exfiltration:
- Attackers can use Stored XSS to steal sensitive user information, such as login credentials, personal details, and other private data stored within the application’s database.
Session Hijacking:
- By capturing session tokens through injected scripts, attackers can hijack user sessions, gaining unauthorized access to user accounts. This can lead to account takeover, enabling attackers to perform actions on behalf of the victim.
Financial Loss:
- Stored XSS can be leveraged for financial gain, with attackers exploiting compromised accounts to make unauthorized transactions, purchases, or withdrawals.
Identity Theft:
- Stolen personal information obtained through a Stored XSS attack can be used for identity theft, leading to a range of fraudulent activities.
Reputation Damage:
- The discovery of a Stored XSS vulnerability and subsequent exploitation can harm the reputation of the affected organization. Users may lose trust in the security of the application, impacting customer loyalty and brand perception.
Malicious Content Injection:
- Attackers can inject and store malicious content on web pages, leading to the distribution of malware to users who access the compromised pages. This can further compromise the security of user systems.
Mitigation for Stored XSS Attack
Here are key mitigation strategies:
Input Validation and Sanitization:
- Implement strict input validation on the server side to ensure that user inputs conform to expected formats and patterns.
- Use whitelisting techniques to validate and allow only specific types of input. Reject any input that does not adhere to the expected criteria.
Output Encoding:
- Apply proper output encoding to all user-generated content before rendering it in HTML responses. This prevents the execution of stored scripts by neutralizing special characters and script tags.
Content Security Policy (CSP):
- Deploy a robust Content Security Policy to define which sources of content, including scripts, are allowed to execute on a web page. Specify the ‘script-src’ directive to whitelist trusted sources for scripts and prevent the execution of unauthorized scripts.
Secure Session Management:
- Implement secure session management practices, including the use of secure, random session identifiers and regular rotation of session tokens. This reduces the risk of session hijacking.
Web Application Firewalls (WAF):
- Utilize a Web Application Firewall to filter and block malicious requests. WAFs can provide an additional layer of protection by detecting and mitigating XSS attacks in real-time.



