Reflected XSS into HTML context with nothing encoded Lab solved.
In this blog, we will solve one of the labs which is vulnerable to the reflected XSS. First, we will see the functionality of the lab, then find the vulnerable of it. So, let’s get stared with the lab.
Introduction
So, as from the title we can easily know that the lab is Reflected XSS, so let’s understand that what is reflected XSS.
What is Reflected XSS?
A Reflected Cross-Site Scripting (XSS) vulnerability is a type of security flaw commonly found in web applications that allows an attacker to inject malicious scripts into web pages viewed by other users. This occurs when a web application includes unvalidated or unescaped user input in its output, making it possible for an attacker to execute arbitrary code in the context of another user’s browser. The term “reflected” refers to the fact that the injected script is reflected off a web server, rather than being stored persistently.
Brief detail of Reflected XSS Attack
Reflected XSS vulnerabilities arise from insufficient input validation and output encoding by web applications. When a user inputs data into a web form or URL parameter, the application may incorporate that input into the subsequent HTML page without properly validating or sanitizing it.
If an attacker can manipulate this input to inject malicious scripts, the web application may inadvertently execute those scripts when rendering the page for other users.
The most common scenario for a Reflected XSS attack involves an attacker crafting a malicious link or sending a manipulated URL to a victim. When the victim clicks on the link or accesses the URL, the malicious payload is included in the request parameters.
The web application processes these parameters without proper validation, reflecting the injected script back in the response. The victim’s browser then executes the script, allowing the attacker to steal sensitive information, session tokens, or perform actions on behalf of the victim.
Now, we have gone through Reflected XSS, let’s get started with Lab.
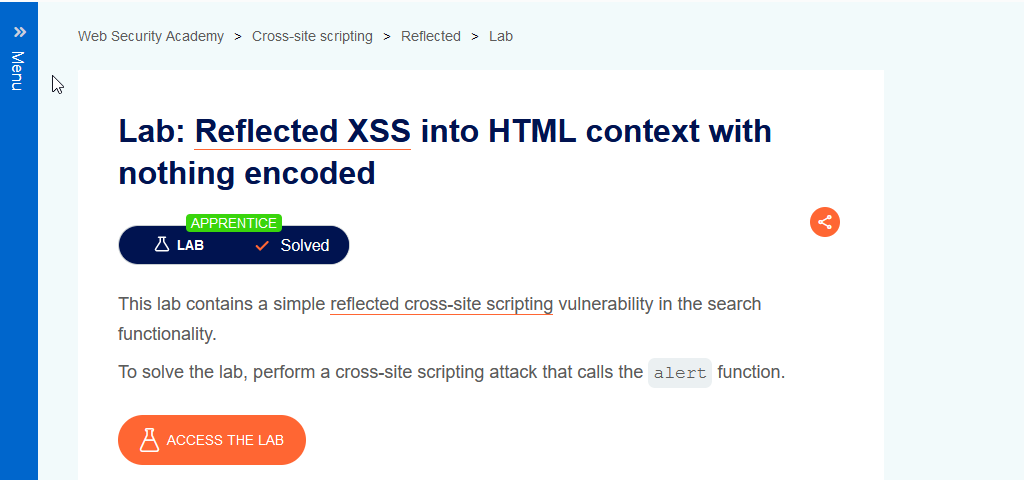
Click on the link, to access the lab, Reflected XSS into HTML context with nothing encoded.
To start the lab, click on the “Access the Lab button”.
Now, you will see the lab. And check all the functionality of the web application.
Step 1: Let’s check the search functionality of the application. Insert the value “hello” in the input field and click on the Submit button.
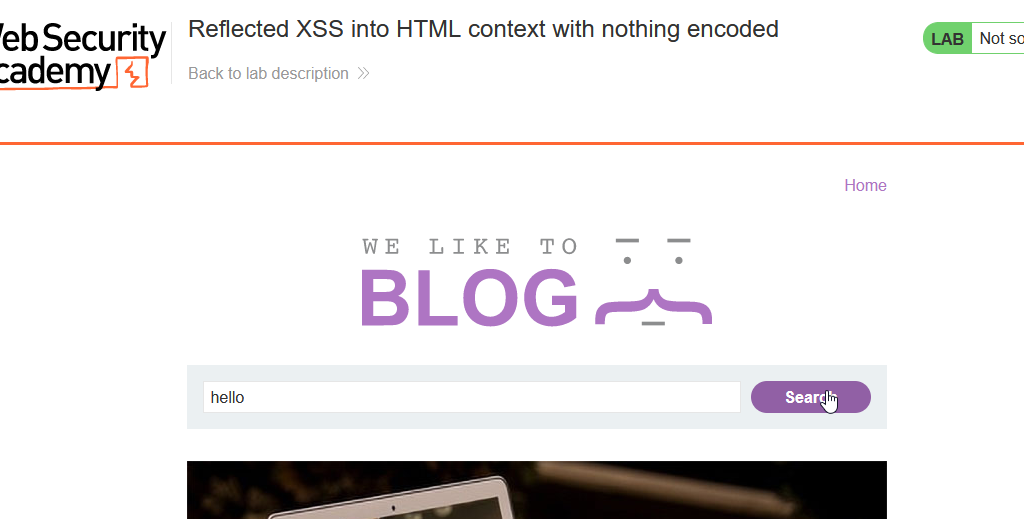
Step 2: Check the URL of the web application, and it’s show like that.

Step 3: So, here we can check that URL is vulnerable or not. So, insert <script> alert(1) </script> in the input field and click on the search button.
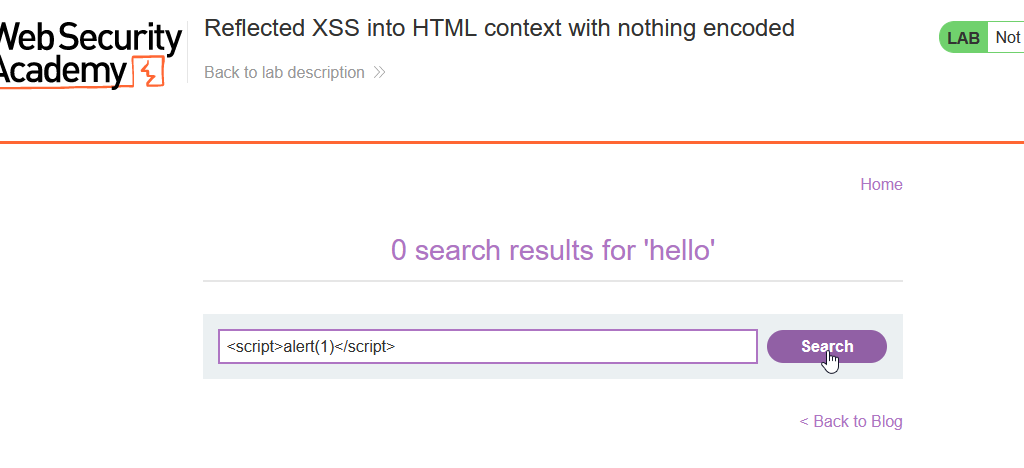
Step 4: As result, you will see the alert pop-up in the webpage, it means that this input filed is vulnerable to XSS Attack.
Step 5: Now, check the URL of malicious injected payload. It looks like mentioned in the below image.

Here, you can see that this is also reflected in the URL.
Congrats, you have solved the lab successfully. If u follow the above step properly.
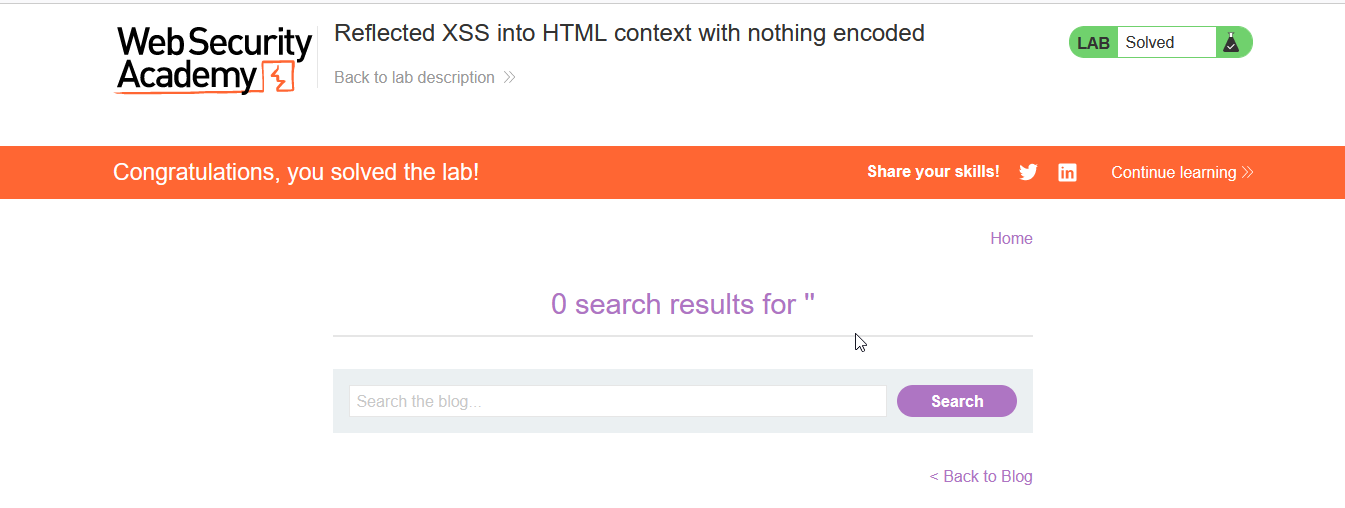
Now, its shown that the lab is vulnerable to reflected XSS. So how, can affect the victim.
So, just copy the URL of the injected payload and share with the victim user.
Impact of Reflected XSS Attack
The impact of a reflected XSS attack is wide-ranging and can include:
Data Theft: One of the primary risks of reflected XSS attacks is the theft of sensitive user data. Attackers can craft malicious scripts to capture login credentials, session tokens, or any other information entered by users on the compromised web page.
Session Hijacking: By stealing session tokens through XSS, attackers can impersonate legitimate users, gaining unauthorized access to their accounts. This can lead to unauthorized actions, manipulation of user data, or even complete account takeover.
Credential Harvesting: If an attacker can inject a script that prompts users for their credentials on a fake login form, unsuspecting users might inadvertently provide their username and password, falling victim to phishing attacks.
Malicious Actions on Behalf of the User: Attackers can use XSS to perform actions on behalf of authenticated users without their consent. For example, they might change account settings, make purchases, or perform actions that could harm the user or the application.
Injection of Malicious Content: XSS attacks can be used to inject malicious content into web pages, potentially distributing malware to users who visit the compromised site. This can lead to further exploitation of vulnerabilities on the user’s system.
Defacement of Web Pages: Attackers may inject scripts to modify the appearance of web pages, defacing the site and potentially causing reputational damage to the organization hosting the application.
Mitigation of Reflected XSS Attack
Here are key mitigation strategies:
Input Validation:
- Validate and sanitize all user inputs on the server side to ensure they adhere to expected formats and do not contain malicious code.
- Use positive validation (whitelisting) rather than negative validation (blacklisting) to explicitly define allowed input patterns.
Output Encoding:
- Encode user-generated content before rendering it in HTML output. This helps neutralize any potentially malicious script tags or special characters.
- Utilize context-specific encoding functions, such as HTML entities encoding (
htmlspecialcharsin PHP), to prevent script execution.
Content Security Policy (CSP):
- Implement a strict Content Security Policy to define which sources of content (scripts, styles, images, etc.) are allowed to be loaded on a web page.
- Specify the ‘script-src’ directive to whitelist trusted sources for scripts, preventing the execution of unauthorized scripts.
HTTP-only Cookies:
- Set the ‘HttpOnly’ attribute on session cookies to prevent them from being accessed by JavaScript. This reduces the risk of session hijacking through XSS.
Web Application Firewalls (WAF):
- Employ a Web Application Firewall that can detect and block malicious requests, including those attempting to exploit XSS vulnerabilities.
- Configure the WAF to filter and sanitize user inputs, providing an additional layer of defense.


0 Comment