Introduction
So, this lab is totally based on Authentication. Let’s, first we will see What Is Authentication?
Authentication is the process of verifying the identity of a user, system, or entity. It is a fundamental concept in computer security and is used to ensure that only authorized individuals or systems are granted access to specific resources, data, or services.
Authentication is a critical component of security measures, helping to prevent unauthorized access, protect sensitive information, and ensure the integrity of systems and data. It is often used in conjunction with other security measures, such as authorization and encryption, to create a comprehensive security strategy.
Now, we have seen the definition of Authentication, let’s start with the Lab solution.
Check the Functionality of Username Enumeration lab
When you click on the Access Lab button, you will be redirected to the Home Page of the Lab.
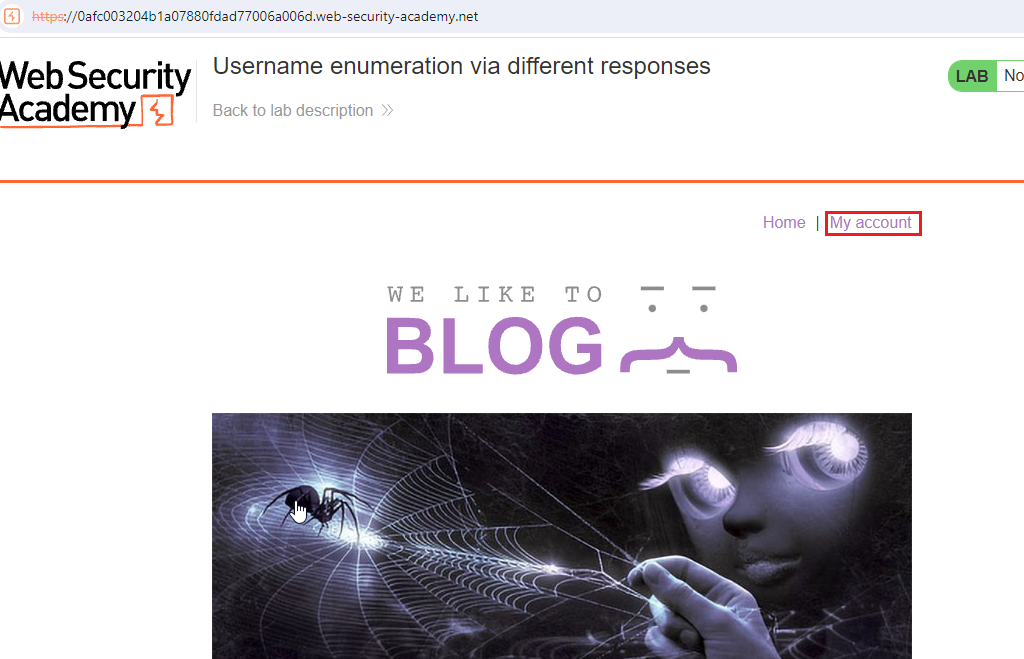
After redirecting to the Home Page, Click on the My Account Button.
On the Username Input Field, put any random name and same with the password input field.
For Example, above username and password input field have the value of demo and 1234, and Click on the Login button.
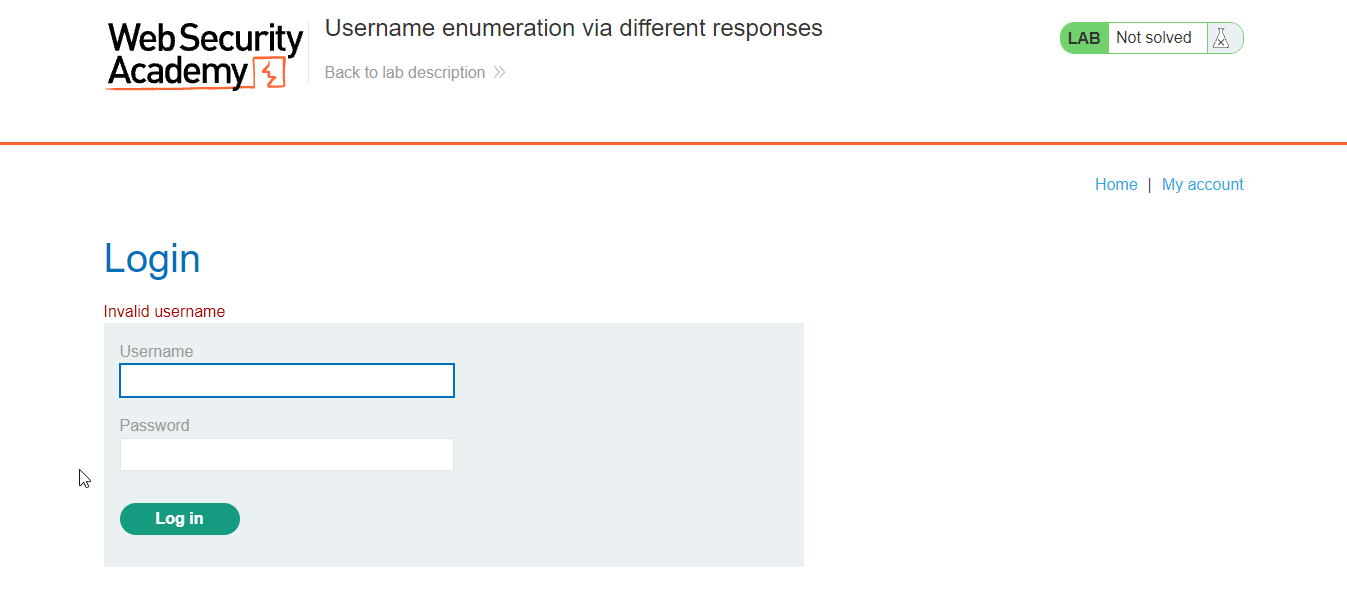
So, in the above image we get the error of the Invalid Username. So, now we have to find correct username. And after that the password.
Conclusion
Above lab first validating the username and after that password.
Solution
Step 1: Brute Force Attack on the Username Field
Username enumeration is a process in ethical hacking where an attacker attempts to identify valid usernames associated with a particular system or application. This information can be valuable for subsequent attacks, such as brute-force attacks or targeted phishing attempts.
As we know the error comes when the username is not correct.
So, let’s first get the correct username.
Enter the value of username and password in the input field of the web page.
Before clicking on the login button, Click on the intercept button.
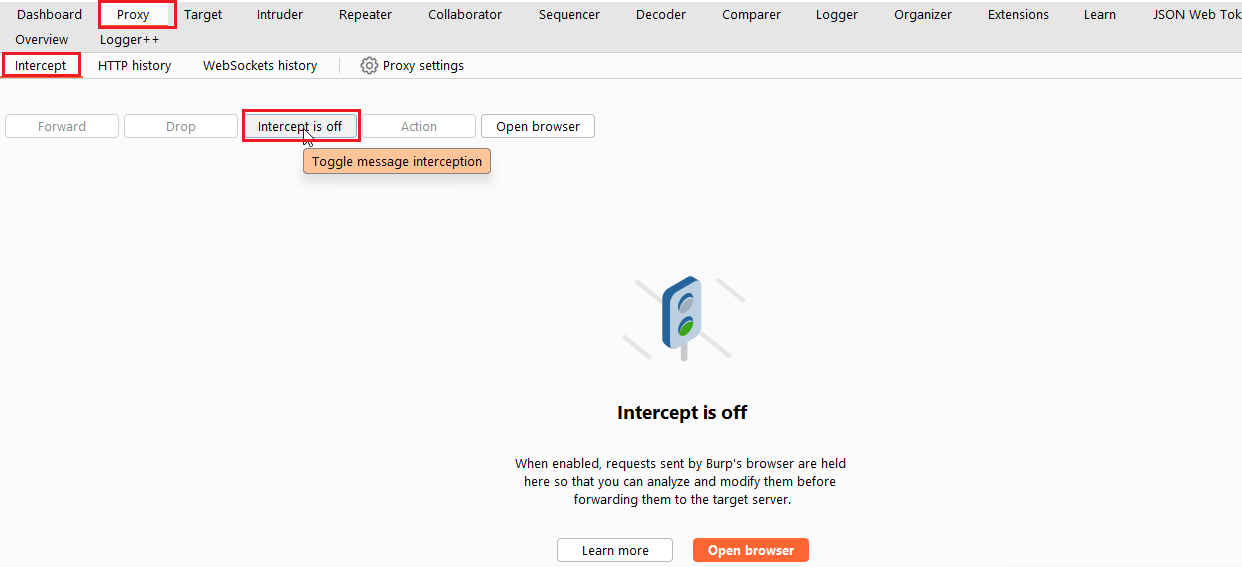
Now, go to web page and click on the Login button, now your request is intercepted in the Burp suite.
Now, your intercepted request looks like with the body.
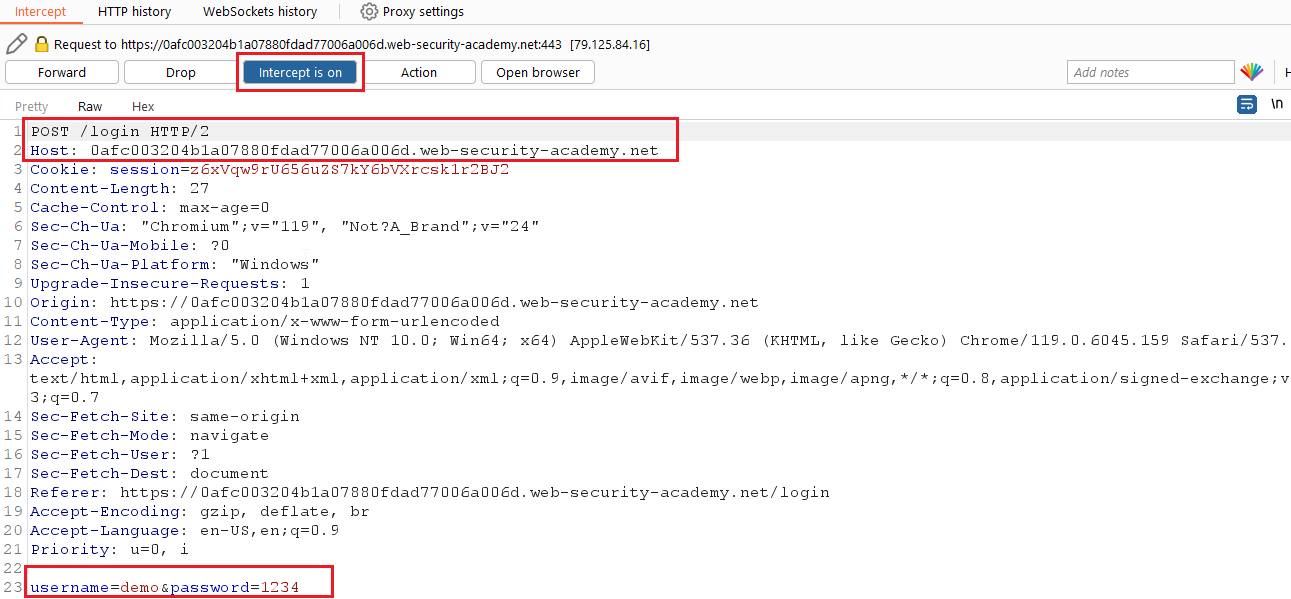
Press Ctrl + I, for Intruder. Now, your request is sent to Intruder.
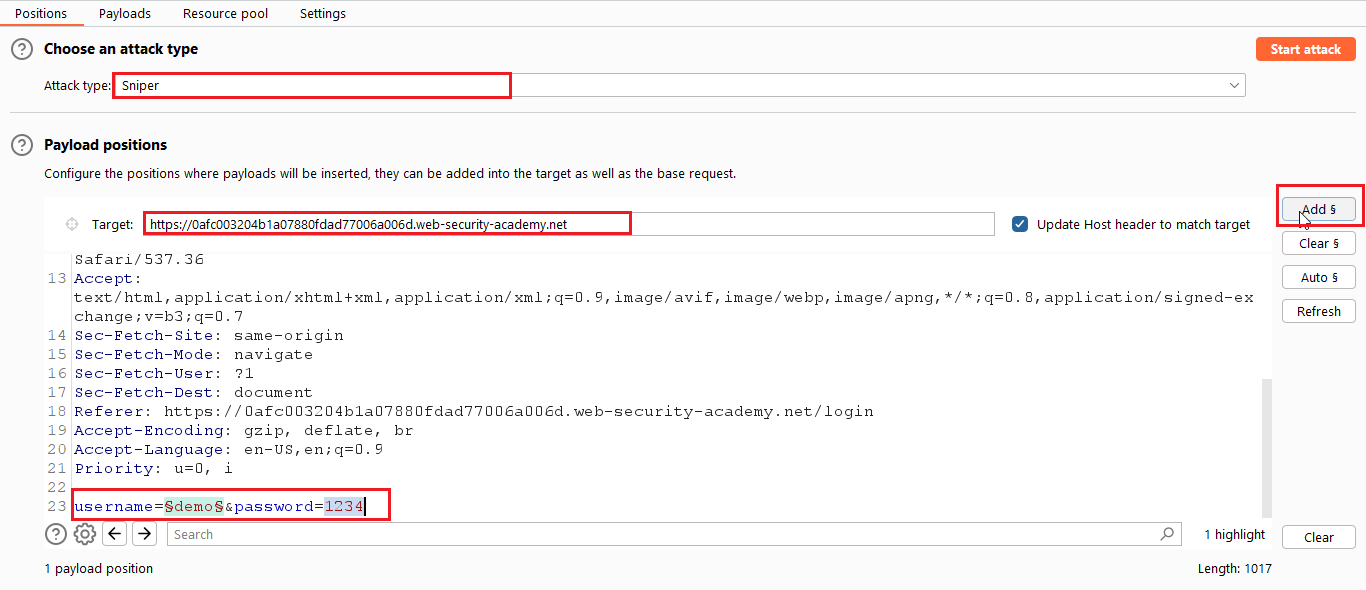
From the above image, you have to do following things. Select the Sniper attack. Select the value of username and click on the “Add” Button.
Now, go to payload section and add the wordlist for the username. Copy the wordlist given below link:
For wordlist of username, https://portswigger.net/web-security/authentication/auth-lab-usernames
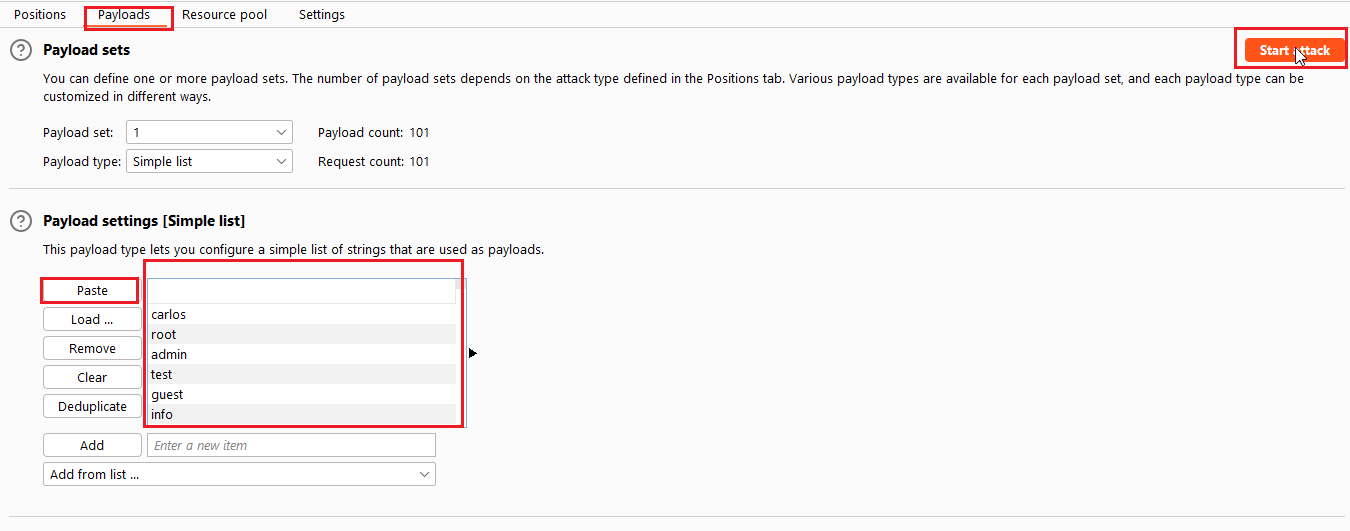
Select the username from the payload list and paste in the container. Now start the attack by clicking on the “Start Attack” button.
You will get the new pop-up screen.
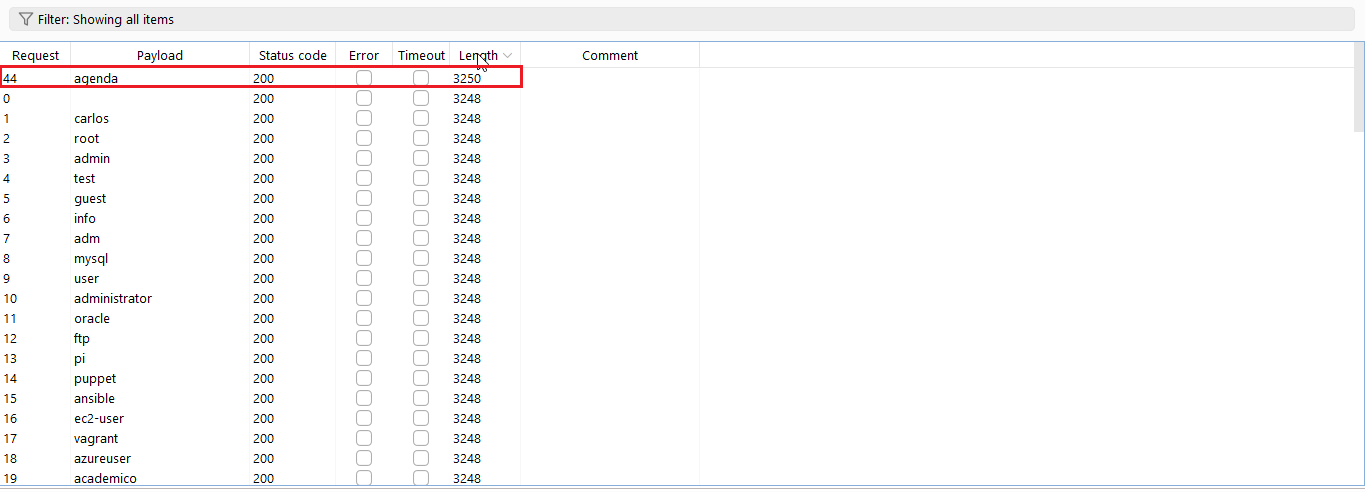
You will get the status 200 for every request but check the length of each request. Or click on the length you will get the highest length.
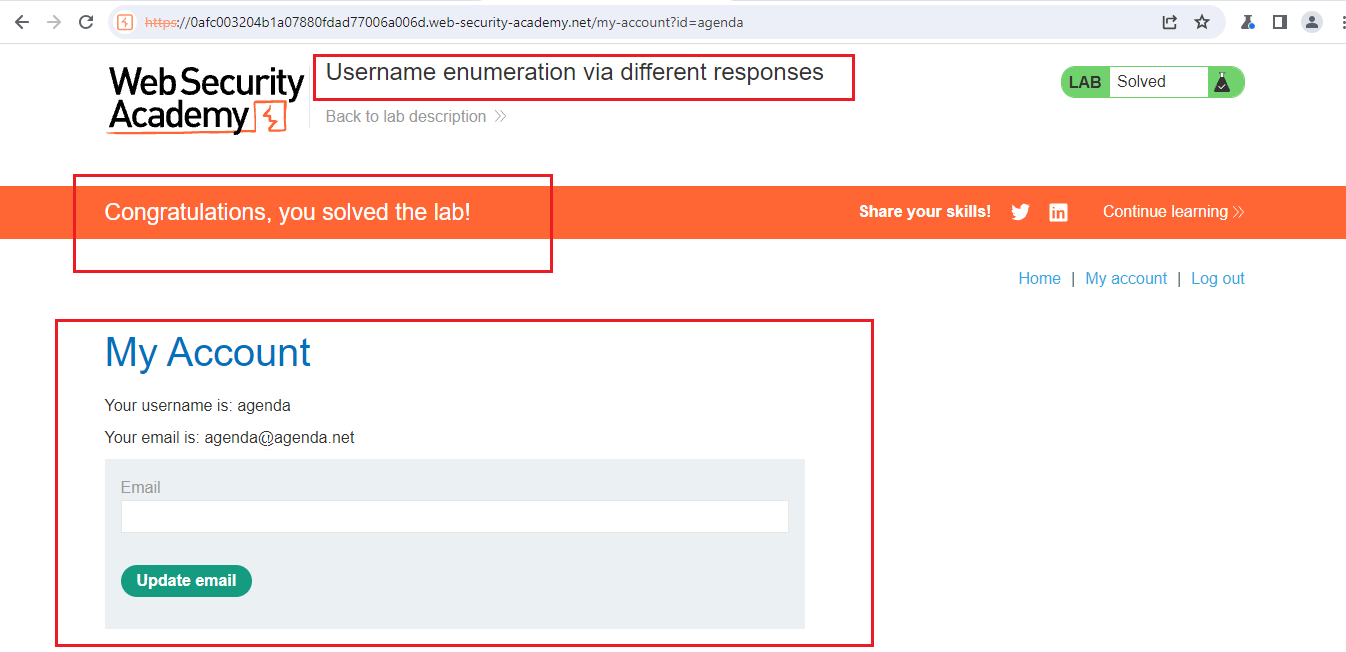
So, now the correct username is agenda.
Now we have to do same with the password also. Go to with intruder and this time we get the correct username so put that in the username key.
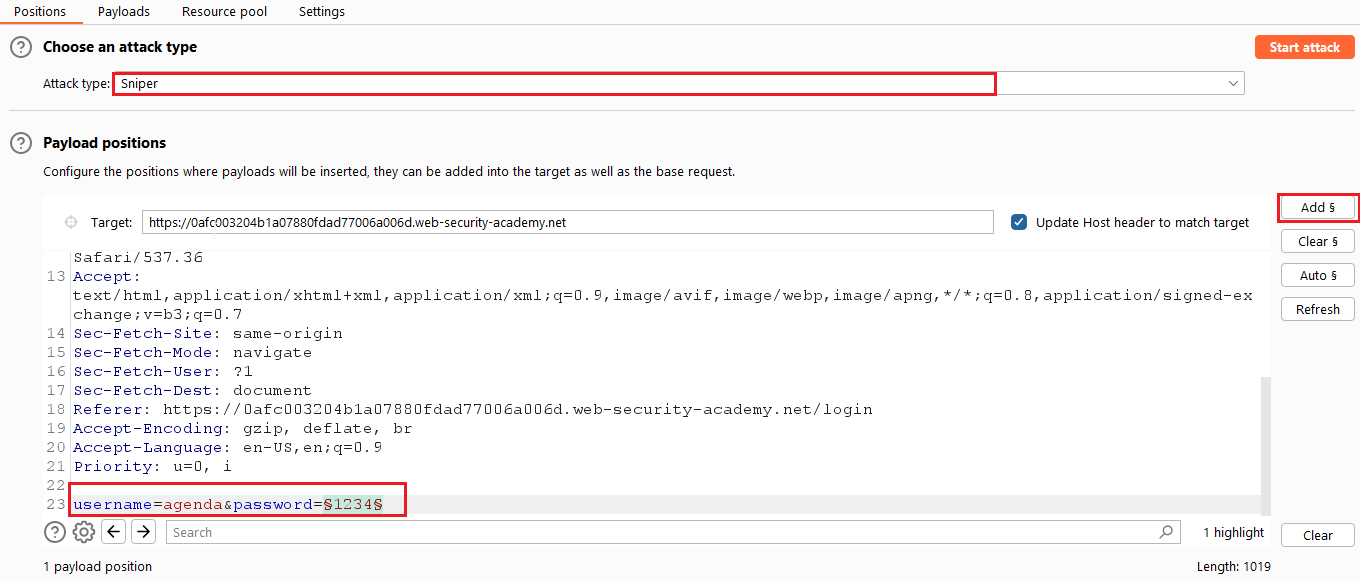
Now, select the password value and click on the Add button. Now copy the payload for the password wordlist below the link:
Now, check the wordlist for password, https://portswigger.net/web-security/authentication/auth-lab-passwords
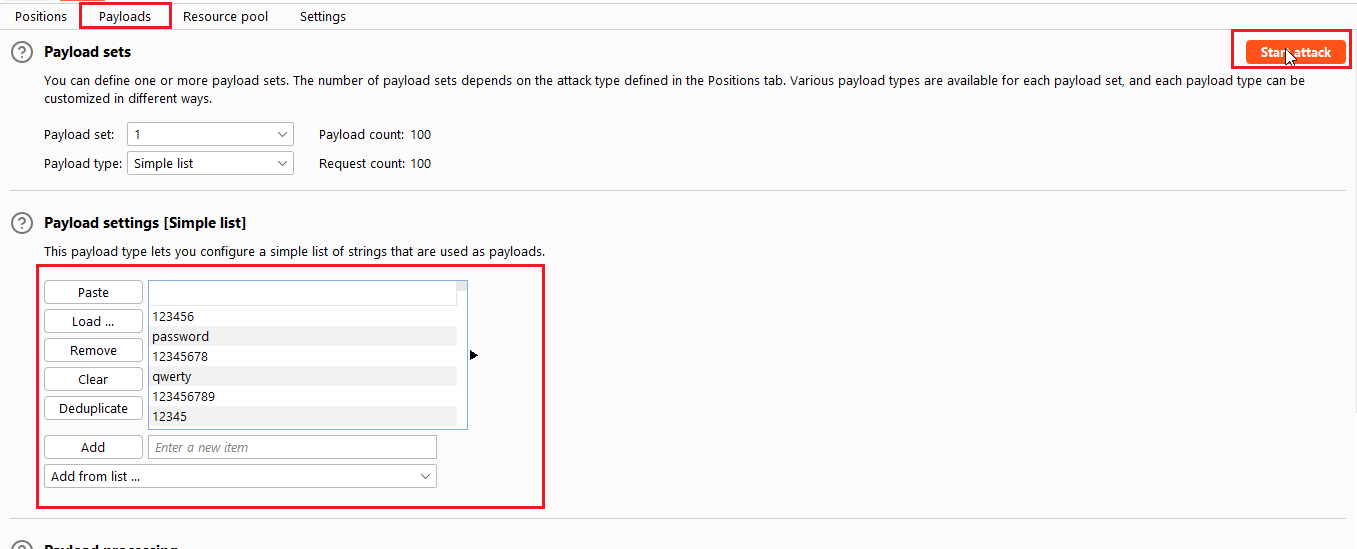
Paste the content of password wordlist and put into the container and click on the Start Attack Button.
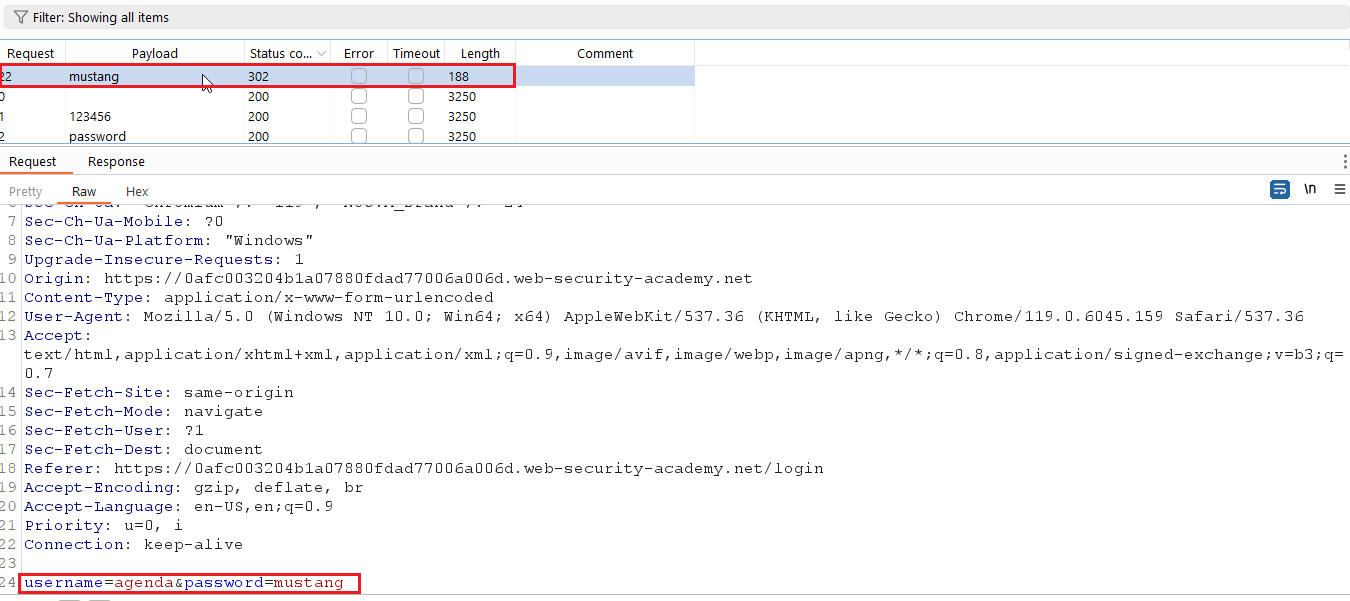
Check the status of each HTTP request who have HTTP Status code of 302.
Here, the correct the username is agenda and mustang.
Now, put these two credentials in the application and check the response of it.
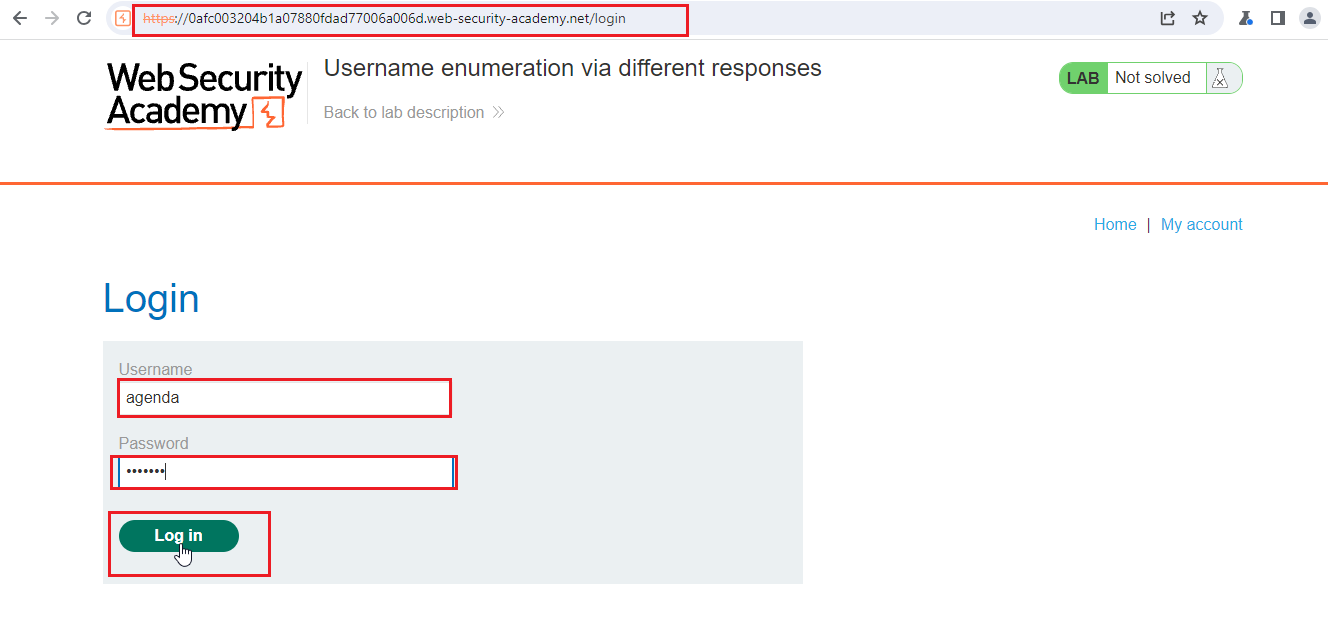
Congrats, if you followed all the steps. You had solved the lab.