In this blog, we will learn about SQL Injection and its Types. It is one of the most critical attacks in Cyber security; if it is not handled correctly, then the company’s server can fail. So let’s get started with the blog.
Table of Contents
- Introduction
- How to detect SQL injection vulnerabilities?
- How do SQL Injection Attacks work?
- SQL Query
- Malicious SQL Query
- Types of SQL Injection Attacks
- Mitigation for SQL Injection Attack
- Conclusion
- Cheat Sheet for SQL Injection
- FAQ
- Recent Articles on Computer Networks
- Related Articles on Linux
Introduction
SQL injection is a type of cybersecurity attack that targets a web application’s database layer.
It occurs when an attacker is able to insert malicious SQL code into a query, manipulating the application’s database and potentially gaining unauthorized access to or control over the data.
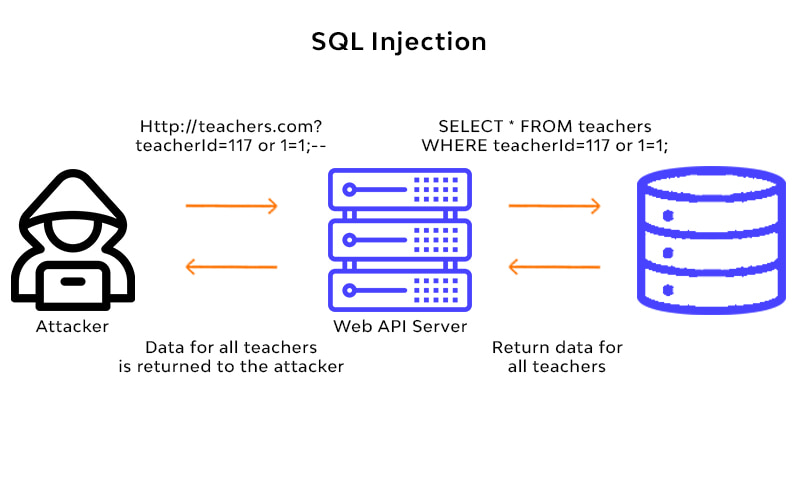
In most cases, it enables an attacker to view data that they would not typically be able to access. Other users’ data or any other data that the application itself has access to may fall under this category.
In many instances, an attacker can update or remove this data, permanently altering the application’s behavior or content.
In some instances, an attacker can escalate a SQL injection attack to compromise the underlying server or back-end structure.
How to detect SQL injection vulnerabilities?
Detecting SQL injection vulnerabilities is crucial for ensuring the security of web applications and databases. Here are steps and techniques to help you detect SQL injection vulnerabilities:
A) Input Validation and Sanitization:
Ensure that all user inputs (from forms, URLs, etc.) are properly validated and sanitized before being used in SQL queries. Use parameterized queries or prepared statements to prevent SQL injection.
B) Error Messages:
Analyze error messages generated by your application. If error messages reveal SQL syntax or database-related information, an attacker could exploit this to construct a SQL injection attack.
C) Testing with Special Characters:
Test inputs with special characters like single quotes (‘), double quotes (“), semicolons (;), and SQL keywords (e.g., OR, AND). If the application behaves unexpectedly or generates SQL-related errors, it might be vulnerable.
D) Union-Based Attacks:
Inject a UNION statement into input fields and observe if the application responds differently or displays additional data. For example, append “UNION SELECT 1,2,3--“ to an input to see if it alters the displayed data.
E) Boolean-Based Attacks:
Use Boolean logic to exploit SQL queries. For instance, append “' OR 1=1--“ to an input to check if it always returns true and reveals unintended data.
F) Time-Based Attacks:
Inject time-delayed SQL queries to test for potential vulnerabilities. For example, “' OR SLEEP(5)--“ might cause a delay in the application’s response.
G) Error-Based Attacks:
Attempt to trigger SQL errors by injecting incorrect or malformed queries into the application’s input fields. Analyze the error responses to identify potential SQL injection points.
How do SQL Injection Attacks work?
The attack takes advantage of improper handling or validation of user-supplied input, allowing an attacker to manipulate the SQL queries executed by the application.
Here’s a step-by-step explanation of how an SQL injection attack typically works:
A) Vulnerable web application:
The attacker identifies a web application that is vulnerable to SQL injection. This vulnerability may arise from improper input handling, a lack of input validation, or the direct concatenation of user input into SQL queries.
B) Identifying injection points:
The attacker analyzes the web application’s input fields, such as login forms, search boxes, or URL parameters, to identify potential injection points where they can manipulate the SQL queries.
C) Crafting malicious input:
The attacker constructs malicious input that includes SQL code as part of the user-supplied data. This input is designed to manipulate the structure or behavior of the SQL query being executed by the application.
D) Exploiting the vulnerability:
The attacker submits the malicious input through the vulnerable input field, which is then processed by the web application. The application fails to properly validate or sanitize the input, allowing the malicious SQL code to be executed within the query.
E) Altering the query logic:
By injecting specific SQL code, such as logical operators or comments, the attacker can modify the query’s logic. This may involve bypassing authentication, extracting sensitive data, modifying or deleting data, or executing arbitrary commands on the database server.
F) Retrieving results or performing actions:
Once the SQL injection payload is successfully injected and executed, the attacker can observe the application’s response. This may involve retrieving data that they are not authorized to access or performing unauthorized actions on the database.
SQL Query
The query is used to communicate with the application’s database. A query is constructed with user-supplied values, and upon execution, it displays the results of a database.
SQL queries are used to interact with databases and perform various operations such as retrieving data, inserting, updating, or deleting records, creating or modifying database structures, and more.
Example:
Select * from user where username="kali" and password="kali";Malicious SQL Query
A malicious SQL query refers to a type of structured query language (SQL) statement or command that is designed to exploit vulnerabilities in a database system or to cause unauthorized or harmful actions.
It is typically crafted by an attacker with the intention of gaining unauthorized access to sensitive data, manipulating data, or disrupting the normal operation of a database.
Example:
When the attacker enters, username: ‘ or ‘I’=’I — and the password is equal to random.
The pair of hyphens (–) designates the beginning of a comment in SQL. Therefore, the query becomes.
Select * from users where username='' or 'I'='I'Since I=I is always true, the user is authenticated and redirected to the requested page.
Types of SQL Injection Attacks
In SQL Injection Attack, there are three types which are as follows:
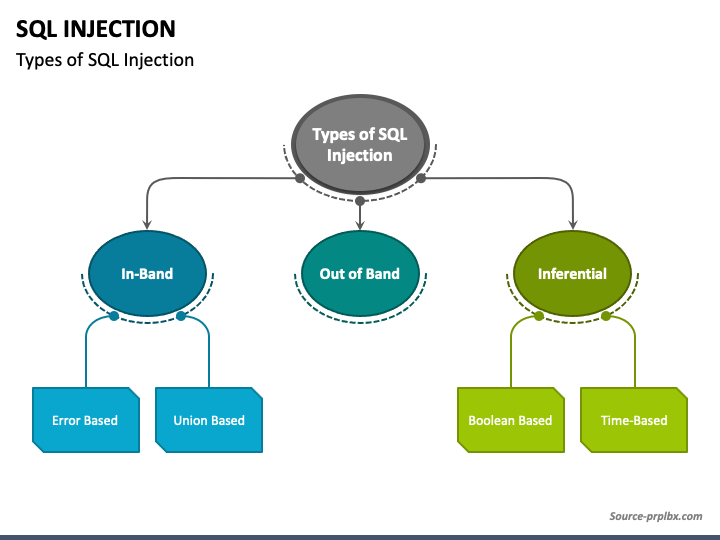
A) In-band SQL Injection
In-band SQL Injection is a category that incorporates injection techniques to launch the injection attack and gather data from the response using the same channel through which requests are being made to the server.
In in-band SQL injection, the attacker injects malicious SQL code into an application’s input fields or parameters. This injected code is then executed by the application’s database server, and the results or error messages are directly communicated back to the attacker. The attacker can obtain the output of the injected query through the application’s response, which can include sensitive information from the database.
In these there are other two types:
Error-based SQLi
In error-based SQL injection attacks, the attacker exploits error messages generated by the database server to extract information or gain unauthorized access.
Error-based SQL Injection relies on error messages from the database server to reveal information about the structure of the database. It is extremely effective for an attacker to enumerate the complete database.
By injecting malicious SQL code that triggers errors, the attacker can obtain valuable details about the database structure, data, or underlying system.
Union-based SQLi
Union-based SQL injection attacks take advantage of the UNION SQL operator, which allows combining the results of two or more SELECT statements.
By injecting malicious code into an input field or parameter and leveraging UNION statements, an attacker can retrieve data from different database tables, even if they are not directly accessible.
B) Inferential (Blind) SQL Injection
Inferential SQL Injection, also known as Blind SQL Injection, is a type of SQL injection attack that does not rely on direct feedback or visible error messages from the application’s response.
In this type of attack, the attacker injects malicious SQL code into an application’s input fields or parameters, just like in other SQL injection attacks. However, rather than receiving direct results or error messages, the attacker crafts queries that rely on conditional statements to determine if specific conditions are true or false.
Boolean-based SQLi
In this technique, the attacker injects SQL queries that include boolean conditions. The attacker observes the behavior of the application’s response to determine if the injected condition is true or false. For example, the attacker might inject a query that checks if a specific user account exists.
Based on the response (whether the application behaves differently when the condition is true or false), the attacker can infer information about the database.
Time-Based SQLi
This technique involves injecting SQL queries that cause a delay in the application’s response. By injecting time-delaying SQL statements, such as the SLEEP() function or busy-wait loops, the attacker can infer information based on the difference in response times.
For example, the attacker might inject a query that introduces a delay if a certain condition is true. By measuring the time it takes for the application to respond, the attacker can determine the truth or falsehood of the condition.
C) Out of band SQLi
Out-of-band SQL Injection is a type of SQL injection attack that relies on using a different communication channel than the one being used by the application to retrieve data or perform actions on the database. Unlike in-band SQL injection, which retrieves results through the same channel as the injected query, out-of-band SQL injection utilizes alternative methods for data extraction.
In out-of-band SQL injection attacks, the attacker injects malicious SQL code into an application’s input fields or parameters, just like in other types of SQL injection attacks. However, instead of directly retrieving the results through the application’s response, the attacker sets up a separate communication channel to retrieve the data or execute further actions.
Mitigation for SQL Injection Attack
To protect against SQL injection attacks, it’s important to implement a combination of preventive measures and best practices. Here are some effective countermeasures:
A) Input Validation and Sanitization:
Validate and sanitize all user input before using it in SQL queries. Use proper input validation techniques to ensure that the input adheres to expected formats, lengths, and types. Sanitize the input by escaping or removing characters that could be interpreted as SQL code.
B) Parameterized Queries or Prepared Statements:
Utilize parameterized queries or prepared statements with placeholders to separate the SQL code from the user input. This ensures that user input is treated as data rather than executable code, reducing the risk of SQL injection attacks.
C) Least Privilege Principle:
Apply the principle of least privilege to database accounts and limit their permissions to only what is necessary. Avoid using privileged accounts for routine application operations. By doing so, even if an attacker manages to inject malicious SQL code, the impact will be limited.
D) Regular Security Patching and Updates:
Keep the database management system (DBMS) and application frameworks up-to-date with the latest security patches and updates. Vulnerabilities in these systems are often discovered and patched, so staying current helps protect against known attack vectors.
E) Security Testing and Code Reviews:
Perform regular security testing, such as penetration testing and code reviews, to identify and remediate any vulnerabilities related to SQL injection. Automated vulnerability scanners and manual security assessments can help uncover potential weaknesses.
F) Web Application Firewalls (WAF):
Implement a web application firewall that can detect and block suspicious SQL injection attempts. WAFs use pattern matching and behavioral analysis to identify and prevent SQL injection attacks from reaching the application.
G) Secure Coding Practices:
Train developers on secure coding practices and educate them about the risks and consequences of SQL injection attacks. Encourage the use of safe coding techniques, such as prepared statements, secure input handling, and secure error handling.
H) Error Handling and Logging:
Implement proper error-handling mechanisms that do not reveal sensitive information to attackers. Additionally, implement logging mechanisms to capture and analyze any unusual or suspicious database activities, which can aid in identifying and responding to potential SQL injection attacks.
By implementing these countermeasures, organizations can significantly reduce the risk of SQL injection attacks and enhance the overall security posture of their applications and databases.
Conclusion
It’s important to note that the impact of an SQL injection attack can vary depending on the specific vulnerability and the privileges granted to the application’s database account.
In some cases, an attacker can gain complete control over the application’s database and potentially access or manipulate sensitive information.
To prevent SQL injection attacks, web developers should employ secure coding practices, such as parameterized queries or prepared statements, validating and sanitizing user input, and employing security mechanisms like input/output validation and web application firewalls.
Regular security testing and code reviews are also crucial to identifying and addressing potential vulnerabilities.
Cheat Sheet for SQL Injection
Click here to read SQL Injection Attack Cheat Sheet
FAQ
What is SQL Injection?
SQL injection is a type of cybersecurity attack that targets a web application’s database layer.
It occurs when an attacker is able to insert malicious SQL code into a query, manipulating the application’s database and potentially gaining unauthorized access to or control over the data.
What are the different types of SQL Injection?
There are three different types of SQL Injection which are as follows:
A) In-band SQL Injection
B) Out- Band SQL Injection
C) Inferential (Blind) SQL Injection
What are the mitigation for SQL Injection?
Mitigation for SQL Injection which are as:
A) Input Validation and Sanitization
B) Parameterized Queries or Prepared Statements
C) Least Privilege Principle
D) Regular Security Patching and Updates
E) Security Testing and Code Reviews
F) Web Application Firewalls (WAF)
Recent Articles on Computer Networks
- Introduction to Computer Networking | What is Computer Network
- What are Topology & Types of Topology in Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and Its Advantages and Disadvantages
- What is a VPN? How does a VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and Different Types of Viruses in Computer
- What is TCP and its Types and What is TCP three-way Handshake
- What is the UDP Protocol? How does it work and what are its advantages?
- What is an IP and its Functions, What is IPv4 and IPv6 Address
- What is MAC Address and its Types and Difference MAC vs IP
- What is ARP and its Types? How Does it Work and ARP Format
- Sessions and Cookies and the Difference Between Them
- What is the ICMP Protocol and its Message Format?
- What is Big Data? Characteristics and Types of Big Data
- Disciplines of CyberSecurity | What are the goals of CyberSecurity?
- What is Firewall, Features, Types and How does the Firewall Work?
- Network Scanning, Types, and Stealth Scan in Computer Network
- Cryptography and its Types in Ethical Hacking
- Tor Browser and How Does It Work | Onion Router Tutorial
- Proxy Server, Advantages, Difference between Proxy Server & VPN
- DHCP Protocol and What Are the Pros and Cons of DHCP
- Intrusion Detection System(IDS) and What are the types of IDS
- Domain Name Server, How Does It Work, and its advantages
- Telnet: Introduction, How Does it Work, and Its Pros and Cons
- SOC: Introduction, Functions performed by SOC, and its Pros
- What is SIEM? | What is the Difference between SIEM and SOC?
- Application Layer in OSI Model | OSI Model Application Layer
- What is SSL Protocol or SSL/TLS and SSL Handshake, and Architecture of SSL
- What are Servers, how do they work, and its different Types
- Network Devices-Router, Switch, Hub, etc in Computer Network
- Connection Oriented and Connection-less Services in Network
- Physical Layer in OSI Model | OSI Model Physical Layer
- Presentation Layer in OSI Model | OSI Model Presentation Layer
- Session layer in OSI Model | OSI Model Session layer
- Transport Layer in OSI Model | Computer Network Transport Layer
- Network Layer in OSI Model | OSI Model Network Layer
- Data Link Layer in OSI Model | OSI Model Data Link Layer
- Block Diagram of Communication System with Detailed Explanation
- Transmission Mode, Types, Pros and Cons in Computer Networks
- LAN, MAN, WAN, PAN, CAN: Types of Computer Network
- Transmission Media | Guided and UnGuided Media in Networks
- URL, Anatomy of a URL, and Difference between URI and URL
Related Articles on Linux
- 10 Tips for the User to Prevent from Being Hacked by Hackers
- Cookie Hijacking, How to Detect and Prevent It with Practicals
- Session Hijacking, and How to Detect and Prevent It with Practicals
- Social Engineering and its Different Types in CyberSecurity
- What is Privilege Escalation Attack, its Types, and Prevention
- KeyLogger Attack and How to Detect and Prevent It
- Eavesdropping Attack and How to Prevent it in Ethical Hacking
- Drive-By Attack and How to Prevent it in Ethical Hacking
- Steganography Attack and How to Hide and Send Data in Image
- What is SQL Injection, its Type, Prevention, and how to perform it
- Broken Access Control Full Guide OWASP 10 in Ethical Hacking
- Insecure Deserialization in Ethical Hacking OWASP 10
- Host Header Injection | How to Attack the Header of a Request
- Email Header Injection | How to Send an Email to an Unknown Person
- DOS Attack (Denial of Service) and Prevent or mitigate it
- Sensitive Data Exposure Vulnerability OWASP10 in Ethical Hacking
- LDAP Injection and What are the Impact and Mitigation of LDAP
- OS Command Injection Attack, Prevent and Detect with Examples
- Code Injection Attack | How to inject the code into the website
- XPath Injection and What are the Impact and Mitigation of XPath Injection
- CRLF Injection and What the Impact and Mitigation of CRLF Injection
- XML Attack or XML External Entities (XXE) and How to Detect and Prevent it
- Cross-Site Scripting or XSS Attack | How to Detect and Prevent from XSS Attack
- Using Components with Known Vulnerabilities Full Guide OWASP
- Insufficient Logging and Monitoring Full Guide OWASP Tutorial
- Phishing Attacks and Their Types | How to Prevent it
- What is Brute Force Attack, Impact and Mitigate it