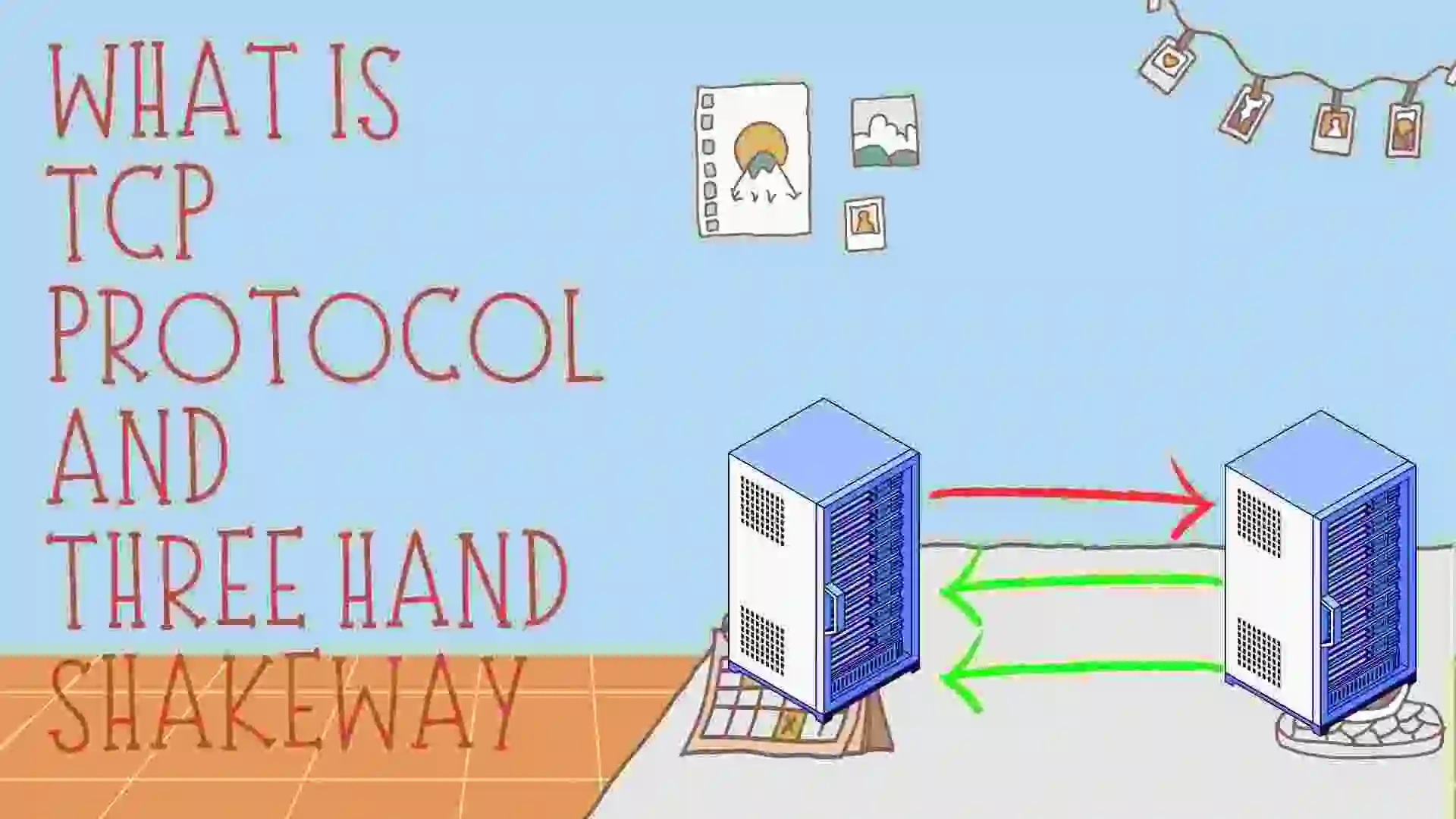
In this blog, we will go through minute details about TCP like what is TCP and why we used it, what are the advantages and disadvantages of TCP and lastly we see how the TCP three-way handshake works. So let’s get started with the blog.
Table of Contents
- Introduction
- Features of TCP Protocol
- Need for Transport Control Protocol
- Working of TCP / Introduction to 3-Way HandShake
- Advantages
- Disadvantages
- TCP Header Format
- FAQ
- Related Articles on Computer Networking
- Recent Articles on Cyber Security Tools
Introduction
TCP (Transmission Control Protocol) is one of the core protocols of the Internet Protocol Suite, which provides a reliable, connection-oriented, and end-to-end data transmission service between applications running on different hosts.
It is responsible for breaking down application data into smaller packets, transmitting them over a network, and ensuring that they are delivered to the intended destination in the correct order and without errors.
TCP was first standardized in 1981 in RFC 793 and has since undergone several revisions and improvements. Today, TCP is widely used by a vast range of applications, including web browsing, email, file transfer, online gaming, and many others.
TCP is a transport layer protocol, which means that it operates on top of the Internet Protocol (IP), which provides a best-effort packet delivery service. Together, TCP and IP form the TCP/IP protocol stack, which is the foundation of the Internet.
Together, they are referred to as a TCP/IP since they are utilized with an IP protocol. The TCP’s primary role is to retrieve data from the application layer.
The data is then divided into numerous packets, each of which is given a number, before being transmitted to the destination. The packets are reassembled by the TCP and sent to the application layer from the opposite side.
As TCP is a connection-oriented protocol, the connection will continue to exist as long as the sender and receiver are still in contact.
Features of TCP Protocol
TCP has several features that make it a reliable and efficient protocol for data transmission. In this article, we will discuss some of the key features of TCP.
Connection-oriented:
TCP is a connection-oriented protocol, which means that it establishes a connection between two hosts before data transmission can begin. The connection is established using a three-way handshake protocol, which involves three steps: SYN, SYN-ACK, and ACK. Once the connection is established, data can be transmitted in both directions.
Reliable:
TCP provides reliable data transmission by using error recovery mechanisms. When a segment is sent, the sending host starts a timer. If an ACK packet is not received before the timer expires, the sending host assumes that the segment was lost or damaged and retransmits it. It also implements a checksum mechanism to detect errors in the data.
Flow Control:
It implements flow control to prevent the receiving host from being overwhelmed with too much data too quickly. To achieve this, TCP uses a sliding window mechanism, which allows the receiving host to inform the sending host how much data it can accept at any given time.
Congestion Control:
TCP uses congestion control to prevent the network from becoming congested with too much traffic. Congestion can occur when too many hosts are transmitting data at the same time. To avoid congestion, TCP uses a variety of congestion control mechanisms, including slow start, congestion avoidance, and fast recovery.
Segmentation:
It breaks down the data into smaller packets, called segments, and adds a TCP header to each segment. The TCP header contains information such as the source and destination port numbers, sequence numbers, and acknowledgment numbers.
Full-duplex operation:
TCP provides full-duplex operation, which means that data can be transmitted in both directions simultaneously.
Windowing:
TCP uses a sliding window mechanism to implement flow control. The window size is negotiated during the connection establishment phase and can be adjusted dynamically during the data transmission phase.
Multiplexing:
It allows multiple applications to use the same connection. Each application is identified by a unique port number.
Header Compression:
It uses header compression to reduce the size of the TCP header. This reduces the overhead of transmitting data over the network and improves the overall performance of the protocol.
Need for Transport Control Protocol
Transport Control Protocol (TCP) is an essential protocol for reliable data transmission over the Internet. It provides reliable, ordered, and error-checked delivery of packets between applications running on hosts communicating through an IP network.
It ensures that packets are delivered in sequence and that errors are corrected or detected. It also provides flow control to prevent the sender from overwhelming the receiver with too much data at once.
TCP is important because it enables the Internet to function as a reliable communication network. Without TCP, packets could be lost, duplicated, or delivered out of order, which could cause significant problems for applications that require reliable data transfer.
It is used by a wide range of applications, including email, file transfer, and web browsing. It is one of the most widely used protocols on the Internet and is critical to the smooth functioning of many different types of services and applications.
[Image]
Working of TCP / Introduction to 3-Way HandShake
The 3-way handshake is a process used by the TCP (Transmission Control Protocol) to establish a reliable connection between two devices over a network. The process involves three steps:
Step 1: SYN
The first step of the handshake is initiated by the client (usually a web browser) sending an SYN (synchronize) packet to the server. This packet contains a random sequence number (SYN number) and a request to establish a connection.
Step 2: SYN-ACK
The server responds with an SYN-ACK (synchronize-acknowledge) packet, which includes its own random sequence number (ACK number) and an acknowledgment of the client’s SYN request. The server also sends its own SYN request to the client, indicating that it is ready to establish a connection.
Step 3: ACK
The client responds with an ACK (acknowledge) packet that acknowledges the server’s SYN request. The ACK packet contains the client’s original SYN number incremented by one, indicating that it has received the server’s SYN-ACK packet and is ready to communicate.
At this point, the connection is established and data can be exchanged between the client and server. The three-way handshake ensures that both devices are synchronized and ready to communicate, and helps to prevent data loss and corruption.
If any of the packets in the 3-way handshake are lost or corrupted, the connection cannot be established, and the process must be repeated.
Advantages
TCP (Transmission Control Protocol) is a reliable and connection-oriented protocol used for transmitting data over a network. Some of the advantages of using TCP include:
Reliable transmission:
TCP ensures that all data packets are delivered to the destination without loss or duplication. It uses acknowledgments and retransmissions to ensure the integrity of the data.
Ordered transmission:
TCP ensures that data packets are transmitted and received in the same order as they were sent. This is important for applications that require the data to be in a specific order.
Flow control:
TCP uses a window mechanism to control the flow of data between sender and receiver. This ensures that the sender does not overwhelm the receiver with too much data.
Congestion control:
TCP uses a congestion control mechanism to prevent network congestion. This ensures that the network is used efficiently and prevents the network from becoming overloaded.
Error checking:
TCP includes a checksum in each packet to detect errors in transmission. This ensures that data is transmitted accurately and reliably.
Interoperability:
TCP is a widely used protocol and is supported by almost all network devices and operating systems. This makes it an ideal choice for applications that need to communicate across different networks and systems.
Overall, TCP provides a reliable and efficient way of transmitting data over a network, making it a popular choice for many applications.
Disadvantages
While TCP (Transmission Control Protocol) has many advantages, there are also some disadvantages to using it:
Overhead:
TCP has a lot of overhead compared to other protocols. This is because it includes error checking, flow control, and congestion control mechanisms in every packet, which increases the size of the packets.
Latency:
TCP can introduce latency into the network. This is because it uses acknowledgments and retransmissions to ensure that all packets are delivered reliably. These extra steps can cause delays in the transmission of data.
Limited performance for certain applications:
TCP is not suitable for certain types of applications, such as real-time streaming applications, that require low latency and high throughput. These applications may benefit from using a protocol like UDP (User Datagram Protocol) instead.
TCP Header Format
The TCP (Transmission Control Protocol) header is a part of the TCP segment that provides information about the transmission of data between devices on a network.
The TCP header consists of several fields that are used to ensure the reliable delivery of data. The format of the TCP header is as follows:
[Image]
- Source Port: A 16-bit field that identifies the sender’s port number.
- Destination Port: A 16-bit field that identifies the receiver’s port number.
- Sequence Number: A 32-bit field that contains the sequence number of the first data byte in the segment.
- Acknowledgment Number: A 32-bit field that contains the next sequence number the receiver is expecting to receive. For example, if the receiver receives the segment number ‘x’, then it responds with ‘x+1’ as an acknowledgment number.
- Data Offset: A 4-bit field that specifies the number of 32-bit words in the TCP header.
- Reserved: A 4-bit field that is reserved for future use, and by default all are set to 0.
- Window Size: A 16-bit field that specifies the number of bytes the sender is willing to receive.
- Checksum: A 16-bit field that is used for error checking.
- Urgent Pointer: A 16-bit field that specifies the end of the urgent data.
- Options: An optional field that is used for various purposes, such as setting the maximum segment size (MSS). The length of this field is variable and depends on the value of the Data Offset field.
- Flags: A 6-bit field that contains various control flags such as URG, ACK, PSH, RST, SYN, and FIN.
- URG: It stands for Urgent Pointer. If it is set, then data will process urgently.
- ACK: If it is set to 0, then it means that the data packet does not contain an acknowledgment.
- PSH: If this field is set, then it requests the receiving device to push the data to the receiving application without buffering it.
- RST: It is set means that it requests to start a connection.
- SYN: It is used to establish a connection between the hosts.
- FIN: It is used to release a connection, and no further data exchange will happen.
FAQ
TCP (Transmission Control Protocol) is one of the core protocols of the Internet Protocol Suite, which provides a reliable, connection-oriented, and end-to-end data transmission service between applications running on different hosts.
It is responsible for breaking down application data into smaller packets, transmitting them over a network, and ensuring that they are delivered to the intended destination in the correct order and without errors.
TCP (Transmission Control Protocol) is a reliable and connection-oriented protocol used for transmitting data over a network. Some of the advantages of using TCP include:
Reliable transmission:
Ordered transmission:
Flow control
Congestion control
Error checking
Interoperability
Transport Control Protocol (TCP) is an essential protocol for reliable data transmission over the Internet. It provides reliable, ordered, and error-checked delivery of packets between applications running on hosts communicating through an IP network.
TCP ensures that packets are delivered in sequence and that errors are corrected or detected. It also provides flow control to prevent the sender from overwhelming the receiver with too much data at once.
TCP is important because it enables the Internet to function as a reliable communication network. Without TCP, packets could be lost, duplicated, or delivered out of order, which could cause significant problems for applications that require reliable data transfer.
Related Articles on Computer Networking
- Introduction to Computer Networking | What is Computer Network
- What are Topology & Types of Topology in Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and its advantages and Disadvantages
- What is VPN? How doe VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and different types of Viruses in Computer