In this blog, we will learn about the topology in computer network. We will learn about the types of topologies in computer networks and their advantages and disadvantages. So, let’s get started with the blog.
Table of Contents
- Introduction to Topology
- Types of Topology
- FAQ
- Articles on Computer Networks
- Related Articles on Cyber Security
Introduction to Topology
“Topology” in computer network refers to the physical or logical arrangement of the network. It describes how the different network nodes, devices, and links are connected to one another.
Types of Topology
There are several types of topology in computer networks, each with its own advantages and disadvantages. Some of the most common topologies used in computer networks include:
A) Bus Topology
A bus topology is a type of network topology in which all devices are connected to a single communication line or “bus.”
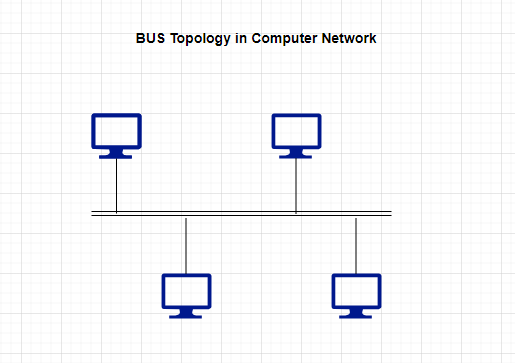
In a bus topology, all devices share the same communication medium, and messages are transmitted along the bus in both directions.
In a bus topology, each device is connected to the communication line via a drop line, which branches off from the main bus. Devices on the network listen for messages on the bus, and when a device wants to send a message, it broadcasts it to all other devices on the network.
Most 802.3 (ethernet) and 802.4 standard networks use the bus topology.
The most common access method is CSMA (Carrier Sense Multiple Access).
CSMA (Carrier Sense Multiple Access) is a media access control protocol used in computer networks to avoid packet collisions between multiple devices sharing the same communication channel.
In a CSMA-based bus topology, each device checks the communication channel for any activity before transmitting its own data. If the channel is idle, the device starts transmitting its data. However, if the channel is busy, the device waits for a random amount of time before retrying its transmission. This random delay is known as the backoff period, and it is intended to prevent devices from constantly retrying transmissions at the same time and causing another collision.
When two nodes send messages concurrently, there are two different solutions to the issues that arise:
CSMA CD (Collision detection):
The access method called CSMA CD (Collision detection) is utilized to find the collision. The sender will stop sending data once the collision has been identified. It focuses on “recovery after the collision” as a result.
CSMA CA (Collision Avoidance):
A collision can be avoided using the CSMA CA (Collision Avoidance) access method by determining if the transmission media is congested or not. If the medium is busy, the sender waits until it is free of activity. This method successfully lowers the likelihood of a collision. “Recovery after the collision” is not possible.
Advantages of Bus Topology
- Easy to set up: Bus topology is easy to set up and maintain since it requires less cable than other network topologies, such as a star topology.
- Low cost: Bus topology is relatively inexpensive since it requires only a single cable to connect all devices.
- Scalability: Bus topology is scalable, meaning that it can accommodate additional devices without affecting the performance of the network.
- Efficient use of bandwidth: In a bus topology, all devices share the same communication channel, which makes it an efficient use of bandwidth.
Disadvantages of Bus Topology
- Single Point of Failure: The bus topology’s central wire or backbone acts as a single point of failure. The network as a whole could malfunction if the cable or backbone breaks.
- Limited Cable Length: The length of the cable in bus topology is limited, which can cause problems in larger networks.
- A limited number of devices: Bus topology can only support a limited number of devices, and the performance of the network may suffer if too many devices are connected.
- Security: Bus topology is not very secure since all devices share the same communication channel, and any device can potentially eavesdrop on communication between other devices.
B) Ring Topology
Ring topology is a type of computer network topology in which each device is connected to two other devices, forming a closed loop. In this topology, data travels around the ring in one direction, and each device repeats the data until it reaches its intended destination.
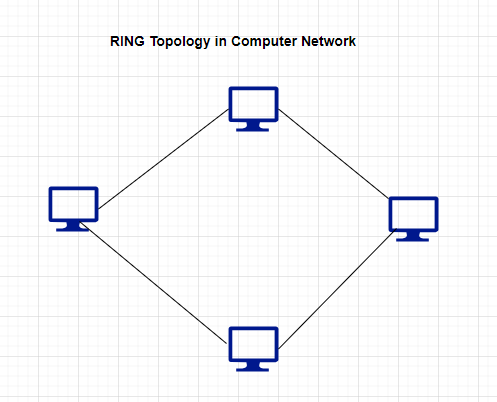
The flow of data in a ring topology is in a clockwise direction.
Token passing is one of the most common methods for accessing data.
Token passing is a method of controlling access to a shared communication channel in a ring topology network. In this method, a token, which is a small packet of data, is passed around the ring from device to device. Only the device holding the token is allowed to transmit data, while all other devices listen to the communication.
Here are the steps involved in token passing in a ring topology network:
- The token circulates around the ring continuously.
- When a device has data to send, it waits for the token to arrive.
- When the device receives the token, it takes possession of the token and sends its data.
- After the data transmission is complete, the device releases the token and sends it to the next device in the ring.
- If a device does not have any data to send, it simply passes the token to the next device.
- If a device fails or is removed from the network, the token will continue to circulate, but the network will be unable to transmit data until the failed device is repaired or replaced.
Advantages of Ring Topology
- Simple to install and configure: Ring topology is relatively easy to install and configure, requiring minimal cabling and hardware.
- Efficient use of bandwidth: In a ring topology, each device has equal access to the communication channel, making it an efficient use of bandwidth.
- High reliability: Ring topology has high reliability since data can flow in both directions, and the ring can quickly recover from a failure in any part of the network.
- Easy to manage: Ring topology is easy to manage since each device has a predefined role and can be quickly identified if it fails.
Disadvantages of Ring Topology
- Limited scalability: Ring topology can support only a limited number of devices, and the performance of the network may suffer if too many devices are connected.
- Single point of failure: Ring topology has a single point of failure, which is the cable that forms the loop. If the cable is cut, the entire network may fail.
- Slow performance: In a ring topology, data must pass through each device in the ring, which can cause delays and slow down the network.
- Difficult to reconfigure: Ring topology can be difficult to reconfigure since each device is dependent on its neighboring devices to maintain the network.
C) Star Topology
Star topology is a type of computer network topology in which each device is connected to a central hub or switch, forming a star-shaped network.
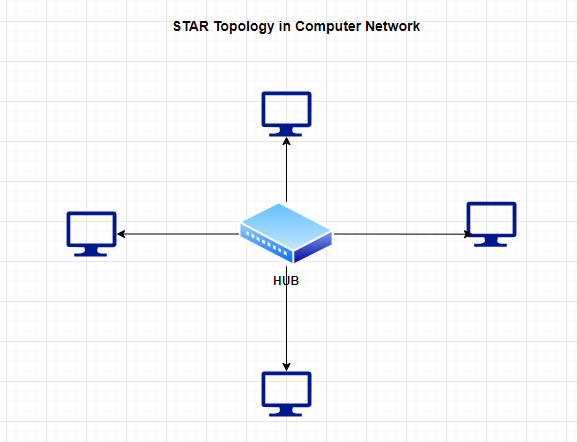
In this topology, all data transmissions are routed through the central hub, and each device has a dedicated communication channel to the hub.
Advantages of Star Topology
- Easy to install and maintain: Star topology is relatively easy to install and maintain since it requires minimal cabling and hardware.
- High reliability: Star topology has high reliability since the failure of one device does not affect the operation of the other devices on the network.
- Scalability: Star topology is highly scalable, meaning that it can accommodate additional devices without affecting the performance of the network.
- Efficient use of bandwidth: In a star topology, each device has a dedicated communication channel to the central hub, making it an efficient use of bandwidth.
Disadvantages of Star Topology
- Cost: Star topology can be more expensive than other network topologies since it requires a central hub or switches.
- Single point of failure: Star topology has a single point of failure, which is the central hub or switch. If the hub or switch fails, the entire network may fail.
- Limited cable length: The length of the cable in star topology is limited, which can cause problems in larger networks.
- Management complexity: Star topology can be complex to manage since each device is connected to the central hub or switch, and any changes to the network must be made at the central point.
In conclusion, star topology is a trustworthy and effective network topology for medium-sized to big networks. It is a popular option for many different types of networks due to its simplicity of installation, dependability, scalability, and effective use of bandwidth.
D) Tree Topology
A “tree topology” in a computer network refers to a type of network architecture where devices are connected in a hierarchical structure resembling a tree.
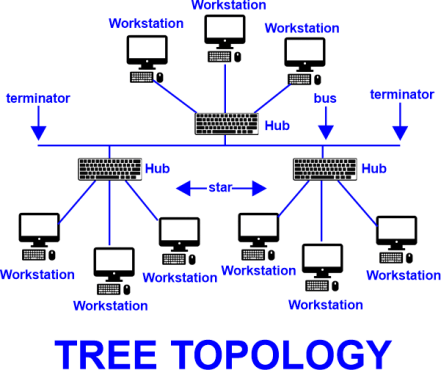
The network consists of a central node, known as the root, from which other nodes branch out. The root node is connected to one or more nodes, which in turn are connected to other nodes, forming a tree-like structure.
In a tree topology, the nodes that are directly connected to the root node are called level 1 nodes, and the nodes that are directly connected to level 1 nodes are called level 2 nodes, and so on. This hierarchy helps in managing and organizing the network traffic flow in a structured way
Advantages of Tree Topology
- Scalability: The tree topology is highly scalable, which means that additional nodes can be added to the network by simply connecting them to the appropriate level nodes.
- Centralized Management: The tree topology allows for centralized management of the network, as the root node can act as a central hub for monitoring and managing network traffic.
- Reduced Traffic: The hierarchical structure of the tree topology helps to reduce network traffic, as data is only sent to nodes that need it, instead of broadcasting to all nodes.
- Easy Troubleshooting: The hierarchical structure of the tree topology makes it easier to identify and troubleshoot problems within the network, as issues can be isolated to specific nodes or levels.
Disadvantages of Tree Topology
- Single Point of Failure: The tree topology is vulnerable to a single point of failure, as the entire network can be affected if the root node fails.
- Costly: The tree topology can be more costly to implement and maintain than other types of network topologies, as it requires a centralized hub and additional cabling.
- Network Performance: The network performance can be affected if there is a large number of nodes at the lower levels of the hierarchy, as the data has to pass through multiple levels before reaching its destination.
- Limited Flexibility: The tree topology can be less flexible than other types of network topologies, as nodes can only connect to specific level nodes and cannot connect to other nodes directly.
E) Mesh Topology
A mesh topology in a computer network refers to a type of network architecture where devices are connected to one another in a non-hierarchical, interconnected mesh. In a mesh topology, every node is connected to every other node, allowing for multiple paths for data to travel through the network.
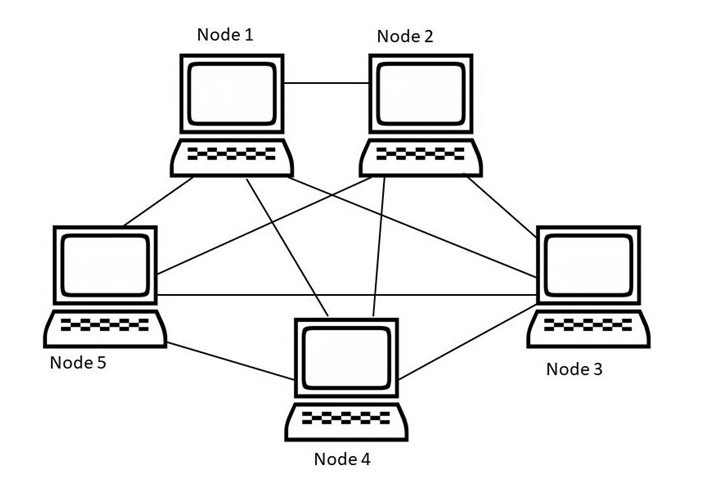
Mesh Technology can be formed by using the formula:
- Number of cables = (n*(n-1))/2;
Here, n is the number of nodes that represents the network.
Advantages of Mesh Topology
- High Reliability: Since every node is connected to every other node, mesh topologies offer high reliability and fault tolerance. If one node fails, data can still be transmitted through other nodes.
- High Scalability: Mesh topologies are highly scalable, as new nodes can be added to the network without affecting the performance of the existing nodes.
- High Bandwidth: Mesh topologies offer high bandwidth, as data can be transmitted through multiple paths simultaneously, allowing for efficient data transmission.
- Flexibility: Mesh topologies are flexible, as nodes can be added, removed, or relocated without affecting the rest of the network.
Disadvantages of Mesh Topology
- High Cost: Mesh topologies can be expensive to implement, as they require a large number of connections and cables.
- Complex Design: Mesh topologies can be difficult to design and maintain, as they require careful planning to ensure that all nodes are connected properly.
- High Redundancy: Mesh topologies can have high redundancy, as each node is connected to every other node, which can result in a waste of resources.
- Network Performance: As the number of nodes increases, the performance of the network can decrease, as the number of connections and cables required to connect each node can become overwhelming.
F) Hybrid Topology
A hybrid topology in a computer network is a combination of two or more basic topologies, such as star, bus, ring, or mesh, to form a more complex network architecture. In a hybrid topology, the resulting network may exhibit the characteristics of the individual topologies that make up the hybrid.
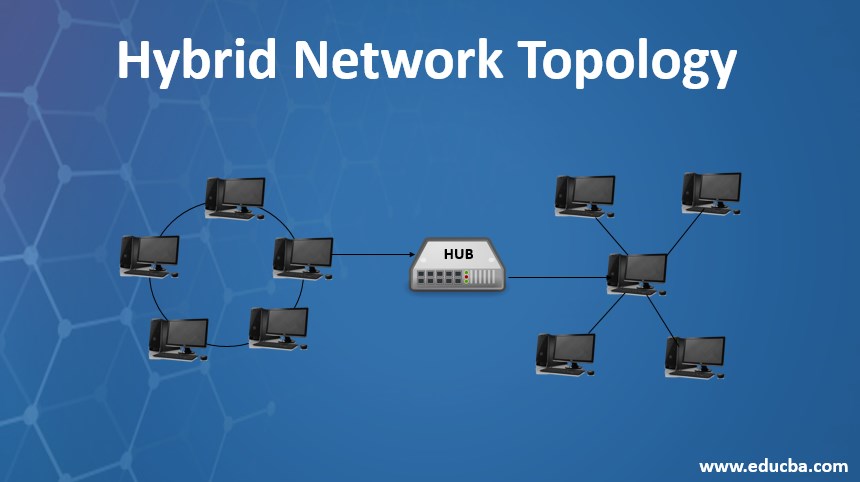
Advantages of Hybrid Technology
- Improved Reliability: A hybrid topology can provide improved reliability by combining the benefits of different topologies. For example, a star-bus hybrid topology can provide redundancy by using a bus topology for the backbone, and a star topology for the end devices.
- Increased Scalability: A hybrid topology can be more scalable than a single topology, as it can be designed to meet the specific needs of the organization. For example, a ring-mesh hybrid topology can provide high bandwidth and redundancy for a large number of devices.
- Improved Performance: A hybrid topology can provide improved performance by balancing the traffic load across different topologies. For example, a mesh-star hybrid topology can reduce congestion and improve performance by using a mesh topology for interconnecting backbone switches, and a star topology for connecting end devices.
- Enhanced Security: A hybrid topology can provide enhanced security by using different topologies for different functions. For example, a bus-ring hybrid topology can use a bus topology for low-security data, and a ring topology for high-security data.
Disadvantages of Hybrid Technology
- Increased Complexity: A hybrid topology can be more complex than a single topology, as it requires more design and configuration effort, and can be more difficult to troubleshoot.
- Higher Cost: A hybrid topology can be more expensive to implement than a single topology, as it requires additional hardware and cabling.
- Greater Maintenance: A hybrid topology can require more maintenance and management effort than a single topology, as it involves multiple topologies that may have different configurations and requirements.
Note: For more information about topology in computer networks, you should visit this website. Click Here
FAQ
What is a topology in computer networks?
“Topology” in computer networks refers to the physical or logical arrangement of the network. It describes how the different network nodes, devices, and links are connected to one another.
What are the types of topology in computer networks?
There are six types of topology in computer network:
1) Bus Topology
2) Ring Topology
3) Mesh Topology
4) Star Topology
5) Hybrid Topology
6) Tree Topology
Articles on Computer Networks
- Introduction to Computer Networking | What is Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and Its Advantages and Disadvantages
- What is a VPN? How does a VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and Different Types of Viruses in Computer
- What is TCP and its Types and What is TCP three-way Handshake
- What is the UDP Protocol? How does it work and what are its advantages?
- What is an IP and its Functions, What is IPv4 and IPv6 Address
- What is MAC Address and its Types and Difference MAC vs IP
- What is ARP and its Types? How Does it Work and ARP Format
- Sessions and Cookies and the Difference Between Them
- What is the ICMP Protocol and its Message Format?
- What is Big Data? Characteristics and Types of Big Data
- Disciplines of CyberSecurity | What are the goals of CyberSecurity?
- What is Firewall, Features, Types and How does the Firewall Work?
- Network Scanning, Types, and Stealth Scan in Computer Network
- Cryptography and its Types in Ethical Hacking
- Tor Browser and How Does It Work | Onion Router Tutorial
- Proxy Server, Advantages, Difference between Proxy Server & VPN
- DHCP Protocol and What Are the Pros and Cons of DHCP
- Intrusion Detection System(IDS) and What are the types of IDS
- Domain Name Server, How Does It Work, and its advantages
- Telnet: Introduction, How Does it Work, and Its Pros and Cons
- SOC: Introduction, Functions performed by SOC, and its Pros
- What is SIEM? | What is the Difference between SIEM and SOC?
- Application Layer in OSI Model | OSI Model Application Layer
- What is SSL Protocol or SSL/TLS and SSL Handshake, and Architecture of SSL
- What are Servers, how do they work, and its different Types
- Network Devices-Router, Switch, Hub, etc in Computer Network
- Connection Oriented and Connection-less Services in Network
- Physical Layer in OSI Model | OSI Model Physical Layer
- Presentation Layer in OSI Model | OSI Model Presentation Layer
- Session layer in OSI Model | OSI Model Session layer
- Transport Layer in OSI Model | Computer Network Transport Layer
- Network Layer in OSI Model | OSI Model Network Layer
- Data Link Layer in OSI Model | OSI Model Data Link Layer
- Block Diagram of Communication System with Detailed Explanation
- Transmission Mode, Types, Pros and Cons in Computer Networks
- LAN, MAN, WAN, PAN, CAN: Types of Computer Network
- Transmission Media | Guided and UnGuided Media in Networks
Related Articles on Cyber Security
- What is Ethical Hacking || Introduction to Ethical Hacking
- System Security and Protection in Cybersecurity
- HIPAA (Health Insurance Portability and Accountability Act) in Cyber Security Law
- PCI DSS (Physical Card Industry and Data Security Standard) in Cyber Security Law
- What is GLBA (Gramm-Leach-Bliley Act) in Cyber Security Law?
- What is NIST (National Institute of Standards and Technology)?
- What is GDPR (General Data Protection Regulation)?
- What are ISO 27001 and CIA in Cyber Security Law?
- What is HITRUST Framework in Cyber Security Law
- Ethical Hackers, Types, and Responsibilities of Ethical Hackers
- VAPT, Benefits, and What are the Roles of VAPT in Company
- What is Pen Testing, Requirement, Types, and Roles of PenTester




