In this blog, we will learn about one of the most important tools in cybersecurity, which is Burp Suite. In this part, we will successfully install BurpSuite on our System and see its advantages and disadvantages. I hope you will like it. So let’s get started with the blog.
Table of Contents
- Introduction to Burp Suite
- Features of Burp Suite
- Capabilities of Burp Suite
- Advantages
- Disadvantages
- Installation
- FAQ
- Recent Articles on Computer Networks
- Recent Articles on CyberSecurity Tools
Introduction to Burp Suite
Burp Suite is a powerful web application security testing tool developed by PortSwigger, a leading cybersecurity software company. It is designed to help security professionals identify and mitigate potential security vulnerabilities in web applications. The tool is available in two editions: Burp Suite Professional and Burp Suite Community Editions.
Burp Suite Professional is the full-featured version of the tool that is primarily used by security professionals in large organizations. It includes a wide range of advanced features and capabilities, such as automated scanning, penetration testing, and advanced reporting. Burp Suite Community Edition, on the other hand, is a free and open-source version of the tool that is primarily used by students, hobbyists, and small businesses.
Burp Suite is a comprehensive web application security testing tool that can be used to perform a variety of security tests on web applications. It has many advanced features and capabilities that make it a popular choice among security professionals. In this article, we will discuss the various features and capabilities of Burp Suite and how they can be used to improve the security of web applications.
Burp Suite, to put it simply, is a Java framework designed to act as a one-stop shop for web application penetration testing. Burp is essentially the industry standard tool for performing hands-on web app security evaluations; therefore, in many respects, this objective is accomplished. The same characteristics that make Burp Suite so appealing for web app testing also make it highly popular for evaluating mobile applications, since it nearly flawlessly translates into testing the APIs (Application Programming Interfaces) that power most mobile apps.
Features of Burp Suite
The following are some of the key features of the BurpSuite:
A) Intercepting Proxy:
The Intercepting Proxy is one of the core features of Burp Suite. It allows users to intercept and modify HTTP and HTTPS traffic between the browser and the web server. This feature is particularly useful for identifying and analyzing potential security vulnerabilities in web applications.
B) Repeater:
The Repeater tool allows users to send and modify HTTP requests to the web server. It is particularly useful for testing input validation and authentication mechanisms in web applications.
C) Scanner:
The Scanner is an automated tool that can be used to scan web applications for potential security vulnerabilities. It can be used to identify vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF).
D) Intruder:
The Intruder tool can be used to automate attacks against web applications. It can be used to test input validation and authentication mechanisms, as well as to brute force passwords.
E) Sequencer:
The Sequencer tool can be used to test the randomness of tokens and session IDs used in web applications. It can be used to identify vulnerabilities, such as predictable session IDs.
F) Extensibility:
Burp Suite is highly extensible and can be customized to meet the specific needs of users. It includes an API that allows users to write their own plugins and extensions.
G) Advanced Reporting:
Burp Suite includes advanced reporting features that allow users to generate detailed reports on the security of web applications. Reports can be generated in various formats, including HTML, XML, and PDF.
Capabilities of Burp Suite
Burp Suite is a popular and powerful web application security testing tool. It is widely used by security professionals, developers, and penetration testers to test the security of web applications. The capabilities of Burp Suite include:
A) Intercepting HTTP/S traffic:
BurpSuite acts as a proxy between the client and server and can intercept and modify the HTTP/S requests and responses in real time. This feature is useful for identifying and exploiting vulnerabilities like XSS, CSRF, SQL injection, and more.
B) Scanning for vulnerabilities:
Burp Suite has an automated vulnerability scanner that can scan web applications for common vulnerabilities like SQL injection, XSS, and more. It can also be customized to perform more advanced scanning techniques.
C) Fuzzing:
BurpSuite can perform automated fuzzing by sending large amounts of randomized data to web applications to find vulnerabilities.
D) Spidering and mapping:
Burp Suite can spider web applications to identify all the pages and inputs and generate a site map that can be used for testing and analysis.
E) Repeater:
BurpSuite includes a tool called the Repeater that allows for manual testing and modification of individual requests.
F) Intruder:
Burp Suite’s Intruder tool can be used to automate the testing of multiple input fields with a large number of payloads. This tool is useful for finding vulnerabilities like SQL injection, XSS, and more.
G) Collaborator:
Burp Suite includes a Collaborator tool that can be used to test for blind vulnerabilities like SSRF and XXE.
H) Reporting:
Burp Suite can generate reports that detail the vulnerabilities found during testing. Reports can be customized to include specific details and can be exported in various formats like HTML, XML, and PDF.
Overall, Burp Suite is a comprehensive web application security testing tool that can be used for a wide range of testing and analysis purposes.
Advantages
Here are some of the advantages of Burpsuite are:
- Comprehensive functionality: BurpSuite provides a wide range of features such as scanning, proxy, spidering, and others that make it a comprehensive tool for web application security testing.
- User-friendly interface: The user interface of BurpSuite is user-friendly and easy to navigate, which makes it easy for both beginners and experienced security professionals to use.
- Customization: Burp Suite offers a high degree of customization, which allows users to tailor the tool to their specific needs.
- Integration: Burp Suite integrates with other popular tools used in the web application security industry, such as Nmap and Metasploit.
- Continuous development: Burp Suite is continuously updated with new features and security checks to ensure that it stays current with the latest security trends.
Disadvantages
Here are some of the disadvantages of Burpsuite are:
- Cost: Burp Suite is a commercial tool, which means that it is not free to use. While there is a free version available, the full feature set requires a paid license.
- Limited platform support: Burp Suite only runs on Windows, macOS, and Linux, which may limit its usefulness for some users.
- Resource-intensive: Burp Suite can be resource-intensive, which means that it may not run efficiently on older or less powerful computers.
- Learning curve: While the user interface of Burp Suite is user-friendly, it can take some time to become familiar with all of the tool’s features and capabilities.
- False positives: Like any security testing tool, Burp Suite can generate false positives, which can lead to wasted time and effort chasing down non-existent vulnerabilities.
Installation
In Kali Linux, there is already installation of Burp Suite is there, so we do not have to download it.
For people who are using Linux, follow the below steps to download it:
Step 1:
Install the JDK file in your system
$ sudo apt-get install openjdk-8-jre
This will install the Java JDK version in your system.
Step 2:
Download Burp Suite Community Edition
Click the below link and click on the Download Button.
Step 3:
After downloading the file, check where your download file is stored, and execute the .sh file.
Example: My download file is stored in a Download folder.
$ cd Downloads
$ chmod u+x burpsuite_community_linux_v2023_2_3.sh
Now run the file
$ ./burpsuite_community_linux_v2023_2_3.shAfter this, a popup will appear to click on the Next Button in all the slides, and at last click on the Finish Button.
After that press the Start Menu Button in Ubuntu and Search for BurpSuite Application
After this, Click on the BurpSuite Application on your Desktop. BurpSuite Dashboard will be shown in this way.
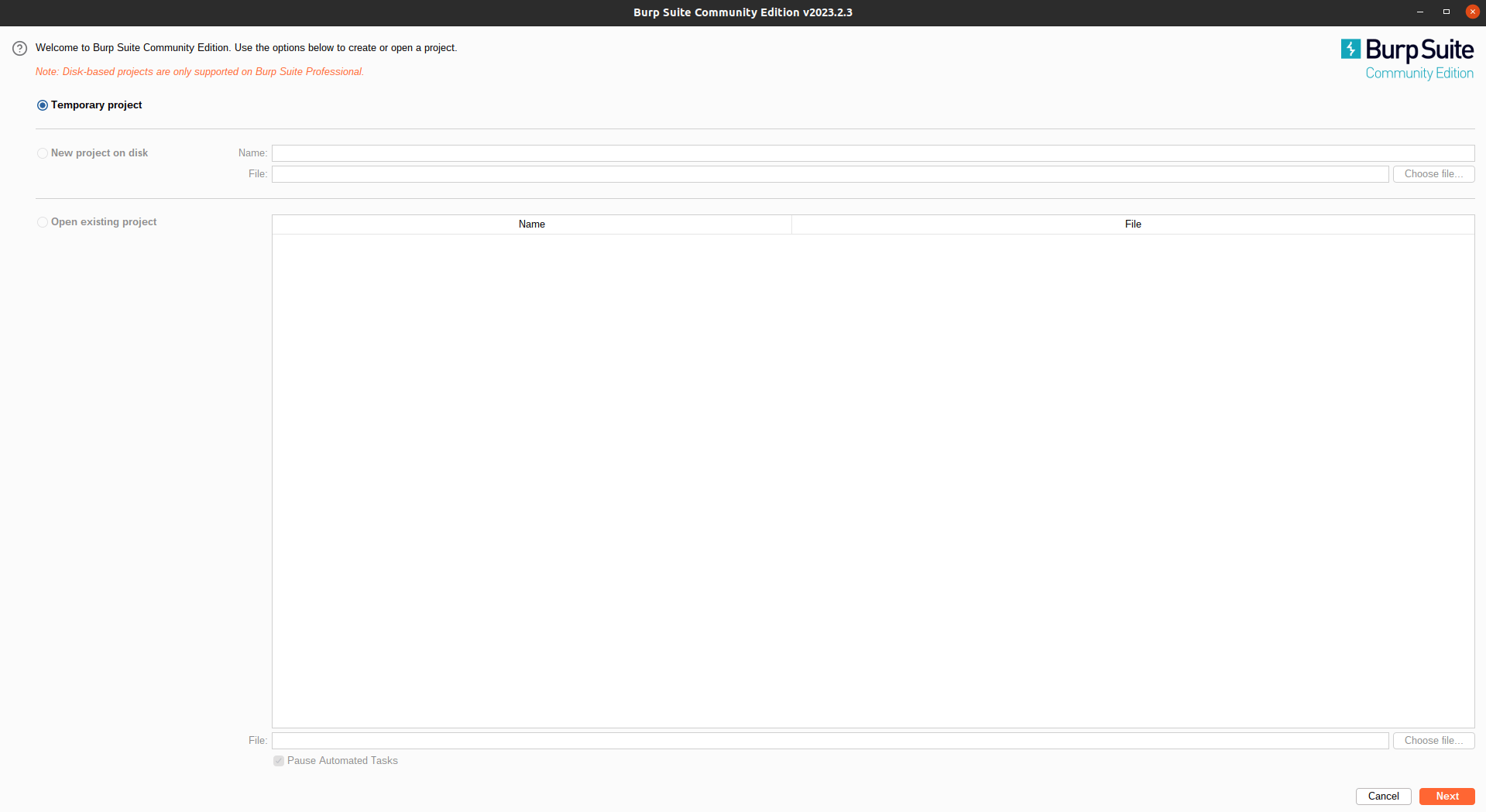
Hopefully, you have successfully installed the BurpSuite Application in your system.
FAQ
Burp Suite is a powerful web application security testing tool developed by PortSwigger, a leading cybersecurity software company. It is designed to help security professionals identify and mitigate potential security vulnerabilities in web applications. The tool is available in two editions: Burp Suite Professional and Burp Suite Community Edition.
Burp Suite, to put it simply, is a Java framework designed to act as a one-stop shop for web application penetration testing. Burp is essentially the industry standard tool for performing hands-on web app security evaluations, therefore in many respects, this objective is accomplished.
In Kali Linux, there is already installation of Burp Suite is there, so we do not have to download it.
For people who are using Linux, follow the below steps to download it:
Step 1:
Install the JDK file in your system$ sudo apt-get install openjdk-8-jre
This will install the Java JDK version in your system.
Step 2:
Download Burp Suite Community Edition
Click the below link and click on the Download Button.
Click Here to Download
Recent Articles on Computer Networks
- Introduction to Computer Networking | What is Computer Network
- What are Topology & Types of Topology in Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and its advantages and Disadvantages
- What is VPN? How doe VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and different types of Viruses in Computer
- What is TCP and its Types and What is TCP three-way Handshake
- What is UDP Protocol? How does it work and what are its advantages?
- What is an IP and its Functions, What is IPv4 and IPv6 Address
- What is MAC Address and its Types and Difference MAC vs IP
- What is ARP and its Types? How Does it Work and ARP Format
- Sessions and Cookies and the Difference Between Them
- What is ICMP Protocol and its Message Format?
- What is Big Data? Characteristics and Types of Big Data
- Disciplines of CyberSecurity | What are the goals of CyberSecurity?
- What is Firewall, Features, Types and How does the Firewall Work?
- Network Scanning, Types, and Stealth Scan in Computer Network
- Cryptography and its Types in Ethical Hacking
- Tor Browser and How does it Work | Onion Router Tutorial
- Proxy Server, Advantages, Difference between Proxy Server & VPN
Recent Articles on CyberSecurity Tools
- Dirb Command Kali Linux | Dirb: A Web-Content Scanner
- What is Tmux? | Introduction to Tmux
- Introduction to Termux | Termux Introduction
- EyeZy: How to log in to other Emails without receiving a Notification.
- Nmap Scanning Tool in Cyber Security with Nmap Cheatsheet
- WPScan Full Tutorial in 10 minutes| How to scan with WPScan
- Modules and Components of Metasploit Framework
- Data Packet Capture and Filters in WireShark
- Tshark: An Alternative for WireShark and How to use it
- SqlMap command in CyberSecurity | SQL Injection Attack Tool
- Hydra Tool Full Guide | Learn Hydra Command Tutorial
- John the Ripper Tool | How to crack the Password of Files
- Nikto Tool Web Vulnerability Scanner That Every Hacker Uses