In this blog, we will learn about the Proxy Chain and Proxy Server in Computer Networking. We will see the working of Proxy Servers and their advantages and disadvantages. So let’s get started with this blog.
Table of Contents
- Introduction to Proxy Server
- Working and Mechanism of Proxy Server
- Purpose of Proxy Server
- Disadvantages of Proxy Server
- Reverse Proxy
- Working of Reverse Proxy
- Advantages of Proxy Server
- Recent Articles on Computer Networks
- Recent Articles on CyberSecurity Tools
Introduction to Proxy Server
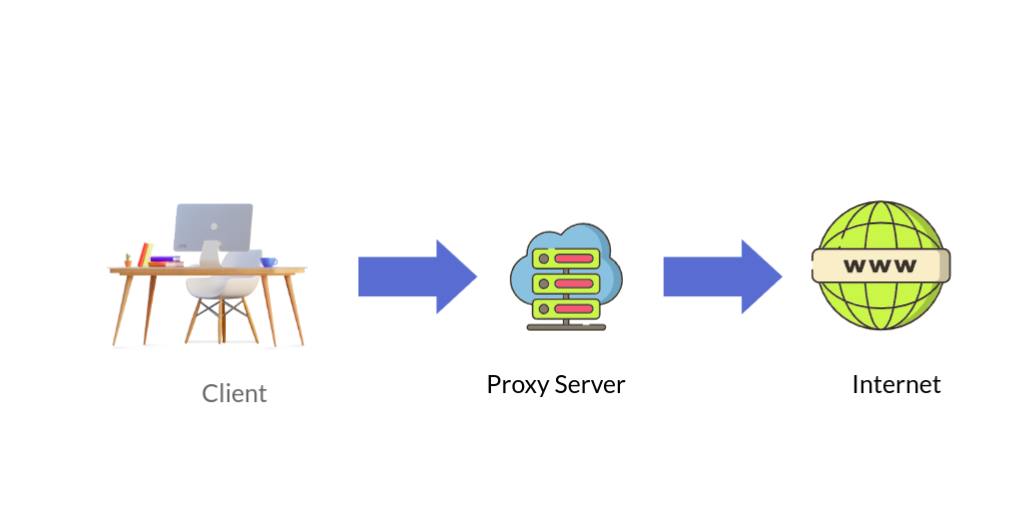
Proxy server acts as an intermediary between a client device, such as a computer, and the destination server it wants to access on the internet. When a client device sends a request for a particular resource, such as a web page, the request first goes to the proxy server.
The proxy server then evaluates the request, retrieves the requested resource on behalf of the client, and forwards it back to the client. Proxy Server has its own IP address.
Proxy servers can be configured at different levels, including application level (e.g., HTTP proxy), transport level (e.g., SOCKS proxy), or network level (e.g., transparent proxy). They are widely used in various environments, such as corporate networks, educational institutions, and for personal privacy purposes.
Working and Mechanism of Proxy Server
The working and mechanism of a proxy server involve the following steps:
Step 1: Client Request
A client device initiates a request to access a resource (e.g., a web page) on the internet. The client’s request is configured to use a proxy server.
Step 2: Proxy Server Configuration
The client device is configured to send its requests to a specific proxy server. This configuration can be set at the application level, system level, or network level.
Step 3: Proxy Server Connection
The client device connects with the proxy server instead of directly connecting to the destination server. The connection can be made using various protocols, such as HTTP, HTTPS, SOCKS, or FTP, depending on the type of proxy server.
Step 4: Proxy Server Evaluation
The proxy server receives the client’s request and evaluates it based on its configured rules and functionalities. This evaluation can include filtering requests, checking for cached resources, or applying security measures.
Step 5: Proxy Server Actions
Condition 1: Caching
If the requested resource is available in the proxy server’s cache and is still valid (not expired), the proxy server retrieves it from the cache and sends it back to the client. This caching mechanism improves performance by reducing the need to fetch resources from the destination server.
Condition 2: Network Communication
If the requested resource is not available in the cache or is expired, the proxy server establishes a connection with the destination server on behalf of the client.
Condition 3: Request Forwarding
The proxy server forwards the client’s request to the destination server, acting as an intermediary. The destination server receives the request as if it originated from the proxy server itself, not the client.
Step 6: Proxy Server Response
The proxy server receives the response from the destination server and evaluates it based on its configured rules. It may modify the response if necessary, for example, by filtering or blocking certain content.
Throughout this process, the proxy server can perform additional functions such as load balancing, content filtering, access control, or encryption/decryption of traffic, depending on its configuration and capabilities.
Purpose of Proxy Server
The primary purpose of a proxy server is to provide various functionalities, including:
A) Anonymity:
Proxy servers can help protect the privacy and identity of clients by masking their IP addresses. When the client communicates with the destination server through a proxy, the server only sees the proxy’s IP address, not the client’s.
B) Caching:
Proxy servers can store copies of frequently accessed resources locally. When a client requests a cached resource, the proxy server can deliver it directly without needing to retrieve it from the destination server. This caching mechanism improves performance and reduces bandwidth usage.
C) Filtering and Content Control:
Proxy servers can be used to filter and control the content that clients can access. Organizations often use proxy servers to enforce policies regarding web browsing, block certain websites, or limit access to specific content categories.
D) Load Balancing:
Proxy servers can distribute incoming requests across multiple servers to balance the load. This helps optimize resource utilization and ensures better performance and availability of services.
E) Security:
Proxy servers can enhance security by acting as a barrier between clients and the internet. They can provide additional layers of protection by inspecting incoming and outgoing traffic, blocking malicious requests, and preventing direct connections to sensitive servers.
Disadvantages of Proxy Server
Here are some common disadvantages of proxy servers:
A) Single Point of Failure:
If the proxy server fails or experiences issues, it can disrupt or completely block clients’ access to the internet or specific resources. Proper redundancy and failover mechanisms should be in place to mitigate this risk.
B) Increased Latency:
The use of a proxy server can introduce additional latency, as the request and response need to go through an intermediary. The impact on latency can vary depending on the distance between the client, proxy server, and destination server.
C) Limited Access to Real IP Information:
Since the destination server only sees the proxy server’s IP address, it can make tracking and identifying individual clients challenging, which can be a disadvantage in certain scenarios, such as troubleshooting or security investigations.
D) Configuration and Maintenance:
Proxy servers require configuration and ongoing maintenance. Administrators need to manage and update proxy server settings, implement security measures, and handle potential compatibility issues with certain applications or protocols.
E) Performance Bottlenecks:
In some cases, if the proxy server is not properly sized or configured, it can become a performance bottleneck, especially when handling high-traffic or resource-intensive requests.
Reverse Proxy
A reverse proxy is a server or service that sits between client devices and web servers. It acts as an intermediary, receiving requests from clients and forwarding them to the appropriate backend server.
Unlike a forward proxy, which is typically used to protect client devices and control access to the internet, a reverse proxy is primarily employed to enhance the performance, security, and scalability of web applications.
Working of Reverse Proxy
Here’s how a reverse proxy typically works:
Step 1:Web Server sends a request
Here, a web browser sends a request for a web resource (e.g., a webpage) to the reverse proxy server.
Step 2: Reverse proxy receives the request
The reverse proxy server receives the web server request.
Step 3: Forwarding the request:
The reverse proxy analyzes the request and determines which backend server should handle it. This decision may be based on various factors such as load-balancing algorithms, caching rules, or content-based routing.
Step 4: Forwarding the request to the Computer User
The reverse proxy forwards the client’s request to the appropriate backend server.
Step 5: The backend server processes the request
The backend server receives the request from the reverse proxy and processes it, generating a response. Once the backend server generates a response, it sends it back to the reverse proxy. The reverse proxy server receives the response and forwards it back to the web server that initially made the request.
Advantages of Proxy Server
By utilizing a reverse proxy, organizations can achieve several benefits:
Load balancing:
Reverse proxies distribute client requests across multiple backend servers to balance the workload and optimize resource utilization.
Caching:
Reverse proxies can cache static content or frequently accessed resources, reducing the load on backend servers and improving response times for subsequent requests.
Security:
Reverse proxies can act as a security layer by inspecting and filtering incoming requests, protecting backend servers from malicious traffic, and implementing security protocols like SSL/TLS encryption.
Scalability:
Reverse proxies enable horizontal scaling by allowing organizations to add or remove backend servers without impacting clients. They abstract the complexity of server infrastructure from clients.
Content manipulation:
Reverse proxies can modify or enhance the content of responses before forwarding them to clients. This enables features like content compression, content filtering, or injecting headers for authentication or tracking purposes.
Recent Articles on Computer Networks
- Introduction to Computer Networking | What is Computer Network
- What are Topology & Types of Topology in Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and its advantages and Disadvantages
- What is VPN? How doe VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and different types of Viruses in Computer
- What is TCP and its Types and What is TCP three-way Handshake
- What is UDP Protocol? How does it work and what are its advantages?
- What is an IP and its Functions, What is IPv4 and IPv6 Address
- What is MAC Address and its Types and Difference MAC vs IP
- What is ARP and its Types? How Does it Work and ARP Format
- Sessions and Cookies and the Difference Between Them
- What is ICMP Protocol and its Message Format?
- What is Big Data? Characteristics and Types of Big Data
- Disciplines of CyberSecurity | What are the goals of CyberSecurity?
- What is Firewall, Features, Types and How does the Firewall Work?
- Network Scanning, Types, and Stealth Scan in Computer Network
- Cryptography and its Types in Ethical Hacking
- Tor Browser and How does it Work | Onion Router Tutorial
Recent Articles on CyberSecurity Tools
- Dirb Command Kali Linux | Dirb: A Web-Content Scanner
- Introduction to Burp Suite | How to Download Burp Suite in Linux
- What is Tmux? | Introduction to Tmux
- Introduction to Termux | Termux Introduction
- EyeZy: How to log in to other Emails without receiving a Notification.
- Nmap Scanning Tool in Cyber Security with Nmap Cheatsheet
- WPScan Full Tutorial in 10 minutes| How to scan with WPScan
- Modules and Components of Metasploit Framework
- Data Packet Capture and Filters in WireShark
- Tshark: An Alternative for WireShark and How to use it
- SqlMap command in CyberSecurity | SQL Injection Attack Tool
- Hydra Tool Full Guide | Learn Hydra Command Tutorial
- John the Ripper Tool | How to crack the Password of Files
- Nikto Tool Web Vulnerability Scanner That Every Hacker Uses