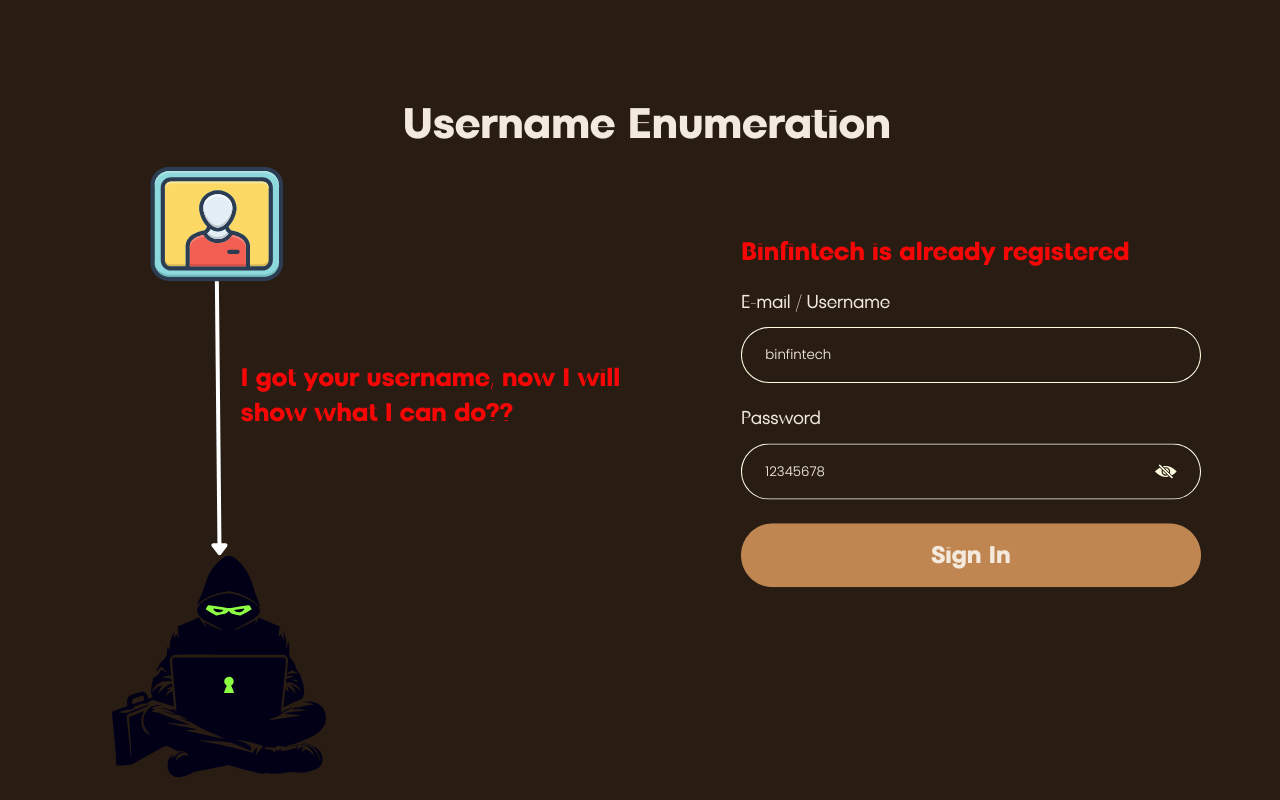
In this blog, we will learn about the Repeater in BurpSuite. We will see what are the other modules in that and how to use them. So let’s get started with the blog.
Table of Contents
- Introduction to Repeater in BurpSuite
- Advantages of Repeater in BurpSuite
- Components of Repeater
- Simple Guide For Repeater in BurpSuite
- Related Articles to Burp Suite
- Recent Articles on Computer Networks
- Recent Articles on CyberSecurity Tools
Introduction to Repeater in BurpSuite
Repeater is a tool within BurpSuite, a widely used web application security testing framework. Repeater provides an interactive interface that allows security testers to manually analyze and modify HTTP and HTTPS requests.
With Repeater, testers can capture requests sent by the web application and resend them multiple times, making it easier to analyze and test the application’s behavior.
It provides a user-friendly interface where testers can modify request parameters, headers, cookies, and other components to test different scenarios and identify vulnerabilities.
Overall, Repeater in BurpSuite provides security testers with a flexible and interactive environment to analyze and modify requests, helping them identify and validate vulnerabilities in web applications.
Advantages of Repeater in BurpSuite
The Repeater tool in Burp Suite offers several advantages that make it a valuable asset for web application security testing and analysis. Here are some key advantages of using Repeater:
A) Manual Request Modification:
Repeater allows security testers to manually modify captured HTTP and HTTPS requests. This gives testers full control over the request parameters, headers, and body, enabling them to test different input values and payloads. Manual request modification is essential for identifying vulnerabilities such as SQL injection, cross-site scripting (XSS), and other input validation issues.
B) Iterative Testing:
With Repeater, testers can easily resend modified requests multiple times. This iterative testing approach allows for fine-tuning and refining the modifications to further investigate the application’s response. Testers can gradually adjust the payload or input values to narrow down the scope of the vulnerability or to verify the impact of the vulnerability on the application.
C) Response Analysis:
Repeater provides a comprehensive view of the server’s response to the modified request. Testers can examine the response headers, status codes, and response bodies to understand how the application handles and processes the modified request. This analysis helps in identifying security flaws, abnormal behaviors, or vulnerabilities in the application.
D) Parameterization:
The repeater supports parameterization, allowing testers to define placeholders for specific values within the request. This feature simplifies the testing process by enabling testers to easily test different variations of input data without manually modifying each occurrence. It enhances efficiency and saves time during testing.
E) Session Preservation:
Repeater preserves session information, such as cookies, which ensures consistent testing within a specific user session. This capability is crucial for maintaining the context of the application and accurately assessing how security controls, such as authentication and session management, are implemented and enforced.
F) Integration with Burp Suite Tools:
Repeater seamlessly integrates with other tools within Burp Suite, such as the Proxy, Scanner, and Intruder. This integration allows testers to leverage the capabilities of these tools in combination with Repeater, enabling comprehensive and efficient security testing.
G) Collaboration and Note-Taking:
The repeater supports collaboration features within Burp Suite, facilitating teamwork among testers. Testers can share captured requests, findings, and notes with other team members, promoting effective communication and knowledge sharing during security testing engagements.
Overall, Repeater in Burp Suite provides testers with a flexible and interactive environment to analyze, modify, and test requests, aiding in the discovery and validation of vulnerabilities in web applications.
Components of Repeater
The Repeater tool in Burp Suite consists of several components that work together to provide a powerful interface for manual request modification and analysis. Here are the main components of Repeater:
A) Request Editor:
The Request Editor is where you can view and modify the captured request. It displays the request line, headers, parameters, and body. You can make changes to any part of the request, including adding or removing headers, modifying parameter values, or adjusting the request body.
B) Response Viewer:
The Response Viewer displays the server’s response to the modified request. It shows the response headers, status code, and response body. You can analyze the response to understand how the application handles and processes the modified request and identify any vulnerabilities or issues.
C) History:
The History section keeps a record of the requests sent and received in Repeater. It allows you to navigate through the request history, review previous requests and responses, and easily revisit and retest specific scenarios.
D) Session Handling:
The repeater supports session-handling capabilities, allowing you to manage and manipulate session-related data. You can capture and modify session tokens, cookies, and other session parameters to simulate different user scenarios and test the application’s security controls.
E) Parameterization:
Repeater includes the ability to parameterize specific values within the request. This allows you to define placeholders for values that you want to test with different variations. Parameterization helps streamline the testing process by enabling you to easily test multiple inputs without manually modifying each occurrence.
F) Collaborative Features:
Repeater supports collaboration features within Burp Suite. You can share captured requests, findings, and notes with other team members, facilitating effective communication and teamwork during security testing engagements.
G) Integration with Other Burp Suite Tools:
Repeater seamlessly integrates with other tools within Burp Suite, such as the Proxy, Scanner, and Intruder. This integration allows you to leverage the capabilities of these tools in combination with Repeater, enhancing the efficiency and effectiveness of your security testing.
These components work together to provide a comprehensive and flexible environment for manually modifying requests, analyzing responses, managing sessions, and collaborating with team members, making Repeater a powerful tool in the Burp Suite arsenal for web application security testing.
Simple Guide For Repeater in BurpSuite
Step 1: Open the Burp Suite Application.
Step 2: Click on the “Intercept is On” and Click on the “Open in Browser”.
Related Articles to Burp Suite
- Proxy Tab in Burp Suite and What Features of it with Sub Modules
- Introduction to Burp Suite | How to Download Burp Suite in Linux
Recent Articles on Computer Networks
- Introduction to Computer Networking | What is Computer Network
- What are Topology & Types of Topology in Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and its advantages and Disadvantages
- What is VPN? How doe VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and different types of Viruses in Computer
- What is TCP and its Types and What is TCP three-way Handshake
- What is UDP Protocol? How does it work and what are its advantages?
- What is an IP and its Functions, What is IPv4 and IPv6 Address
- What is MAC Address and its Types and Difference MAC vs IP
- What is ARP and its Types? How Does it Work and ARP Format
- Sessions and Cookies and the Difference Between Them
- What is ICMP Protocol and its Message Format?
- What is Big Data? Characteristics and Types of Big Data
- Disciplines of CyberSecurity | What are the goals of CyberSecurity?
- What is Firewall, Features, Types and How does the Firewall Work?
- Network Scanning, Types, and Stealth Scan in Computer Network
- Cryptography and its Types in Ethical Hacking
- Tor Browser and How does it Work | Onion Router Tutorial
- Proxy Server, Advantages, Difference between Proxy Server & VPN
Recent Articles on CyberSecurity Tools
- Dirb Command Kali Linux | Dirb: A Web-Content Scanner
- What is Tmux? | Introduction to Tmux
- Introduction to Termux | Termux Introduction
- EyeZy: How to log in to other Emails without receiving a Notification.
- Nmap Scanning Tool in Cyber Security with Nmap Cheatsheet
- WPScan Full Tutorial in 10 minutes| How to scan with WPScan
- Modules and Components of Metasploit Framework
- Data Packet Capture and Filters in WireShark
- Tshark: An Alternative for WireShark and How to use it
- SqlMap command in CyberSecurity | SQL Injection Attack Tool
- Hydra Tool Full Guide | Learn Hydra Command Tutorial
- John the Ripper Tool | How to crack the Password of Files
- Nikto Tool Web Vulnerability Scanner That Every Hacker Uses