In this blog, we will learn about NIST (National Institute of Standards and Technology), which is one of the most important Cyber Security Laws. We will see the main purpose of this law and its reasons. So let’s get started with the blog.
Table of Contents
- Introduction to NIST
- Functions of NIST
- NIST Framework Resources
- Why should I use the NIST Cybersecurity Framework?
- References
- FAQ
- Recent Articles on Computer Networks
- Blogs Related to Cyber Security
Introduction to NIST
The National Institute of Standards and Technology, commonly known as NIST, is a physical sciences laboratory and a non-regulatory agency of the United States Department of Commerce. It was founded in 1901 and is headquartered in Gaithersburg, Maryland, with additional campuses in Boulder, Colorado.
NIST’s primary mission is to promote and maintain measurement standards, technological innovation, and industrial competitiveness in the United States. It plays a crucial role in advancing science, technology, and economic growth by developing and disseminating measurement standards, conducting research, and providing technical support to various industries.
Functions of NIST
Key functions and activities of NIST include:
A) Metrology and Standards Development:
NIST is responsible for developing and maintaining a wide range of measurement standards, ensuring accuracy and consistency in measurements across various fields such as physics, engineering, chemistry, and biology. These standards provide a foundation for industries, research, and technology development.
B) Research and Innovation:
NIST conducts research in various areas, including materials science, information technology, cybersecurity, nanotechnology, and more. This research aims to address scientific and technological challenges, leading to advancements that benefit both industry and society.
C) Calibration Services:
NIST provides calibration services that help ensure the accuracy of measuring instruments used in research, manufacturing, and commerce. These services contribute to the reliability and quality of measurements made by various instruments.
D) Technology Transfer:
NIST collaborates with industries, academia, and government agencies to transfer technology and knowledge generated through its research activities. This helps foster innovation and supports the development of new products, processes, and services.
E) Cybersecurity and Information Technology:
NIST is well-known for its role in developing cybersecurity guidelines, frameworks, and best practices. The NIST Cybersecurity Framework, for example, guides organizations to manage and reduce cybersecurity risks.
F) Disaster Resilience:
NIST is involved in research related to disaster resilience, including building codes, standards, and practices that enhance the ability of communities to withstand and recover from natural and man-made disasters.
G) Publications and Resources:
NIST produces a wide range of publications, reports, guidelines, and databases that contribute to scientific and technical knowledge. These resources are available to the public and various industries.
NIST’s work has a significant impact on various sectors, including manufacturing, healthcare, telecommunications, energy, and more. Its standards and research help ensure the reliability of products and services, promote technological innovation, and contribute to the overall economic growth and well-being of the United States.
NIST Framework Resources
Here are the five fundamental areas or functions that organizations should adhere to according to the NIST Cybersecurity Framework:
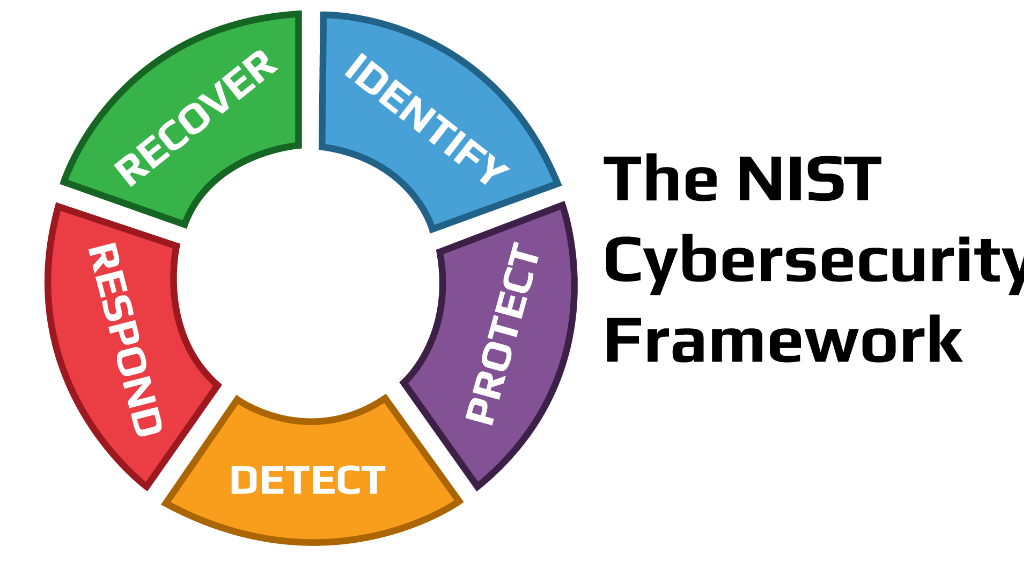
- Identify: This function involves understanding and managing cybersecurity risks to systems, assets, data, and capabilities. Key activities include:
- Identifying and documenting assets and systems to be protected.
- Understanding the organization’s risk tolerance and priorities.
- Assessing and understanding the potential impact of cybersecurity events.
- Identifying and documenting external dependencies and connections.
- Protect: The Protect function focuses on implementing safeguards to prevent or limit the impact of cybersecurity incidents. Key activities include:
- Implementing access controls and data security measures.
- Conducting training and awareness programs for employees.
- Establishing secure software development practices.
- Implementing secure configurations for systems and devices.
- Detect: This function involves actively monitoring systems to identify cybersecurity incidents promptly. Key activities include:
- Implementing continuous monitoring and anomaly detection.
- Establishing incident detection and response processes.
- Regularly reviewing and analyzing logs and security alerts.
- Conducting penetration testing and vulnerability assessments.
- Respond: The Respond function is about taking action when a cybersecurity incident occurs. Key activities include:
- Developing an incident response plan and procedures.
- Establishing communication protocols for reporting incidents.
- Containing the impact of incidents and preventing their spread.
- Coordinating with external entities, such as law enforcement or regulatory bodies.
- Recover: This function focuses on restoring services and operations after a cybersecurity incident and improving resilience. Key activities include:
- Developing and implementing recovery plans and procedures
- Analyzing the incident to identify lessons learned and areas for improvement.
- Improving incident response plans based on post-incident assessments
- Ensuring data integrity and restoring normal operations.
These five functions of the NIST Cybersecurity Framework are designed to be adaptable to various organizations and industries. Organizations can customize their cybersecurity strategies by using these functions as a foundation and tailoring them to their specific needs, risk profile, and technological environment. By following these functions, organizations can create a comprehensive and effective approach to managing cybersecurity risks and ensuring the security and resilience of their systems and data.
Why should I use the NIST Cybersecurity Framework?
There are several compelling reasons why you should consider using the NIST Cybersecurity Framework:
A) Comprehensive Framework:
The NIST Cybersecurity Framework offers a comprehensive and structured approach to cybersecurity risk management. It covers various aspects of cybersecurity, including risk assessment, threat mitigation, incident response, and continuous improvement.
B) Risk-Based Approach:
The framework is designed around the concept of risk management. It helps organizations identify, assess, and prioritize cybersecurity risks based on their specific business context and objectives. This risk-based approach ensures that cybersecurity efforts are focused on the most critical areas.
C) Adaptability and Flexibility:
The framework is adaptable to organizations of all sizes, industries, and levels of cybersecurity maturity. It provides a flexible structure that allows you to customize cybersecurity practices to fit your unique needs and constraints.
D) Common Language:
The NIST Cybersecurity Framework helps establish a common language for discussing cybersecurity within your organization and with external partners. This promotes better communication and collaboration among stakeholders.
E) Alignment with Industry Standards:
The framework aligns with various cybersecurity standards, regulations, and best practices, making it easier for organizations to comply with legal and regulatory requirements. It can serve as a foundation for achieving compliance with regulations like HIPAA, GDPR, or industry-specific standards.
F) Improve Cybersecurity Posture:
By implementing the framework’s guidelines and recommendations, organizations can systematically improve their cybersecurity posture over time. This includes enhancing cybersecurity policies, practices, and controls.
G) Risk Management Integration:
The NIST Cybersecurity Framework aligns well with broader risk management practices. It allows organizations to integrate cybersecurity risk management into their overall enterprise risk management (ERM) strategy.
H) Enhanced Incident Response:
The framework provides guidance on incident response planning and execution, helping organizations be better prepared to detect, respond to, and recover from cybersecurity incidents.
I) Vendor and Third-Party Management:
It can be used to assess the cybersecurity practices of third-party vendors and contractors, helping you manage the risks associated with outsourcing or partnerships.
J) Continuous Improvement:
The NIST Cybersecurity Framework promotes a culture of continuous improvement in cybersecurity. It emphasizes the importance of regularly reviewing and updating your cybersecurity practices to adapt to evolving threats and technologies.
L) Community Support:
The framework is widely recognized and supported by cybersecurity experts, government agencies, and industry organizations. This means that you can find a wealth of resources, tools, and training to support your implementation efforts.
In summary, the NIST Cybersecurity Framework offers a structured, risk-based approach to improving cybersecurity practices. Whether you are looking to enhance your organization’s security, achieve regulatory compliance, or strengthen your overall risk management strategy, the framework can be a valuable resource to guide your efforts.
References
This blog is referenced or taken from this NIST Original Website.
FAQ
The National Institute of Standards and Technology, commonly known as NIST, is a physical sciences laboratory and a non-regulatory agency of the United States Department of Commerce. It was founded in 1901 and is headquartered in Gaithersburg, Maryland, with additional campuses in Boulder, Colorado.
A) Identify: This function involves understanding and managing cybersecurity risks to systems, assets, data, and capabilities.
B) Protect: The Protect function focuses on implementing safeguards to prevent or limit the impact of cybersecurity incidents.
C) Detect: This function involves actively monitoring systems to identify cybersecurity incidents promptly.
D) Respond: The Respond function is about taking action when a cybersecurity incident occurs.
E) Recover: This function focuses on restoring services and operations after a cybersecurity incident and improving resilience.
Recent Articles on Computer Networks
- Introduction to Computer Networking | What is Computer Network
- What are Topology & Types of Topology in Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and its advantages and Disadvantages
- What is VPN? How doe VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and different types of Viruses in Computer
- What is TCP and its Types and What is TCP three-way Handshake
- What is UDP Protocol? How does it work and what are its advantages?
- What is an IP and its Functions, What is IPv4 and IPv6 Address
- What is MAC Address and its Types and Difference MAC vs IP
- What is ARP and its Types? How Does it Work and ARP Format
- Sessions and Cookies and the Difference Between Them
- What is ICMP Protocol and its Message Format?
- What is Big Data? Characteristics and Types of Big Data
- Disciplines of CyberSecurity | What are the goals of CyberSecurity?
- What is Firewall, Features, Types and How does the Firewall Work?
- Network Scanning, Types, and Stealth Scan in Computer Network
- Cryptography and its Types in Ethical Hacking
- Tor Browser and How does it Work | Onion Router Tutorial
- Proxy Server, Advantages, Difference between Proxy Server & VPN
- DHCP Protocol and What Are the Pros and Cons of DHCP
- Intrusion Detection System(IDS) and What are the types of IDS
- Domain Name Server, How Does It Work, and its advantages
- Telnet: Introduction, How Does it Work, and Its Pros and Cons
- SOC: Introduction, Functions performed by SOC, and its Pros
- What is SIEM? | What is the Difference between SIEM and SOC?
- Application Layer in OSI Model | OSI Model Application Layer
- What is SSL Protocol or SSL/TLS and SSL Handshake, and Architecture of SSL
Blogs Related to Cyber Security
- What is Ethical Hacking || Introduction to Ethical Hacking
- System Security and Protection in Cybersecurity
- HIPAA (Health Insurance Portability and Accountability Act) in Cyber Security Law
- PCI DSS (Physical Card Industry and Data Security Standard) in Cyber Security Law
- What is GLBA (Gramm-Leach-Bliley Act) in Cyber Security Law?