In this blog, we will learn about connection oriented and connection-less networks. We will see its characteristics and disadvantages. So, let’s get started with the blog.
Table of Contents
- Introduction to Connection Oriented Networks
- Characteristics of Connection Oriented Network
- Examples of Connection Oriented Networks
- Disadvantages of Connection Oriented Network
- Introduction to Connection-less Network Service
- Characteristics of Connection-less Network Service
- Disadvantages of Connection-less Network Service
- Examples of Connection-less Network Services
- Difference between Connection-Oriented and Connection-less Network
- FAQ
- Articles on Computer Networks
- Related Articles on Linux
Introduction to Connection Oriented Networks
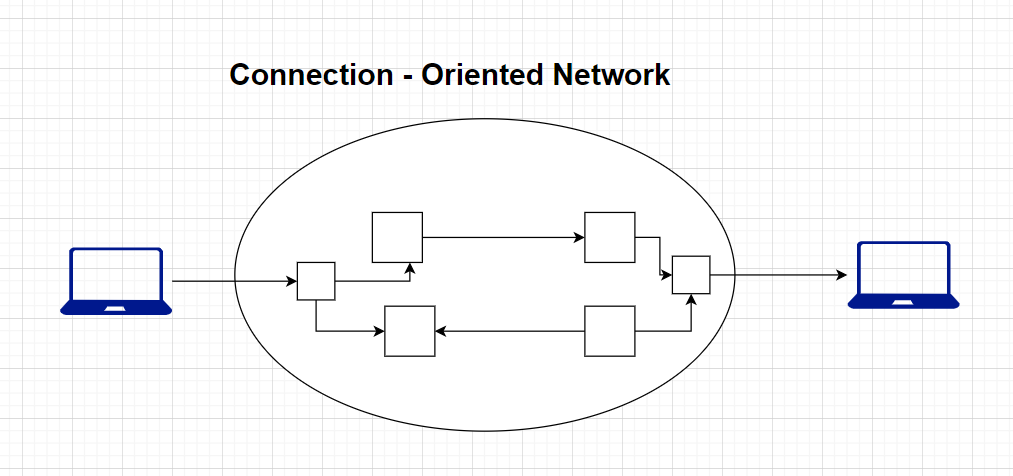
Connection oriented networking is a communication paradigm used in computer networks to establish reliable and predictable data transmission between two devices. In connection-oriented communication, a logical connection is established before data is exchanged, and this connection remains active until the data exchange is completed. This approach ensures data integrity, order, and efficient flow control.
Characteristics of Connection Oriented Network
A) Reliability:
Connection oriented networks provide a high level of reliability by ensuring that data is transmitted accurately and without errors. This is achieved through error detection, correction mechanisms, and acknowledgments.
B) Sequential Data Delivery:
Data packets are delivered in the same order they were sent. This is particularly important for applications that require data integrity and where the sequence matters, such as streaming media or file transfers.
C) Flow Control:
Connection oriented networking implements flow control mechanisms to prevent data overload on the receiving side. This helps avoid congestion and ensures that the receiver can handle the incoming data at a manageable pace.
D) Acknowledgments:
The receiving end of the connection acknowledges the successful receipt of data packets. If a packet is not acknowledged, it will be retransmitted, ensuring that no data is lost during transmission.
E) Virtual Circuit Establishment:
Connection oriented networks establish a virtual circuit between the sender and receiver before data transmission. This involves negotiating various parameters for the connection, such as quality of service, transmission rates, and other settings.
F) Resource Reservation:
The resources required for the data transmission, such as bandwidth, buffer space, and processing power, are reserved in advance to ensure a consistent quality of service.
Examples of Connection Oriented Networks
- Asynchronous Transfer Mode (ATM): ATM networks establish virtual circuits for data transmission, ensuring consistent data flow and low latency.
- Frame Relay: Frame Relay networks create logical connections called “permanent virtual circuits” for reliable data transmission.
- Integrated Services Digital Network (ISDN): ISDN uses circuit-switching technology to establish a dedicated connection between sender and receiver for digital communication.
Disadvantages of Connection Oriented Network
Here are some of the disadvantages of connection oriented networks:
A) Overhead:
Connection oriented networks involve more overhead compared to connectionless networks. The process of establishing, maintaining, and terminating connections requires additional communication and computational resources. This overhead can lead to slower data transmission and higher resource utilization.
B) Complexity:
The establishment and maintenance of connections involve more complex protocols and mechanisms. This complexity can result in increased chances of errors, configuration issues, and difficulties in troubleshooting and debugging network problems.
C) Scalability:
Connection oriented networks can face challenges in scaling to handle a large number of simultaneous connections. As the number of connections increases, the network infrastructure may struggle to manage the associated state information and control messages, potentially leading to performance bottlenecks.
D) Latency:
The process of establishing a connection before data transmission can introduce latency or delay. While this may not be a significant concern for applications that require a continuous data stream, it can be problematic for real-time or interactive applications where low latency is crucial.
E) Resource Consumption:
Connection oriented networks require resources to maintain the state of each connection. This can include memory for storing connection-related information and processing power for managing and updating this information. In scenarios with limited resources, such as IoT devices or embedded systems, this can be a drawback.
Introduction to Connection-less Network Service
A connectionless network service is a communication paradigm used in computer networks where data is transmitted between devices without the need for the prior establishment and maintenance of a dedicated connection.
In contrast to connection-oriented networks, where a virtual circuit is set up before data transfer, connectionless networks operate by sending individual packets of data independently, with each packet containing addressing information that allows it to reach its intended destination.
In a connectionless network, data packets are treated as independent entities. Each packet contains both the source and destination addresses, enabling routers and switches to forward the packet toward its destination.
As packets travel through the network, they can take different paths and arrive out of order. This requires mechanisms at the receiving end to reorder and reassemble the packets correctly.
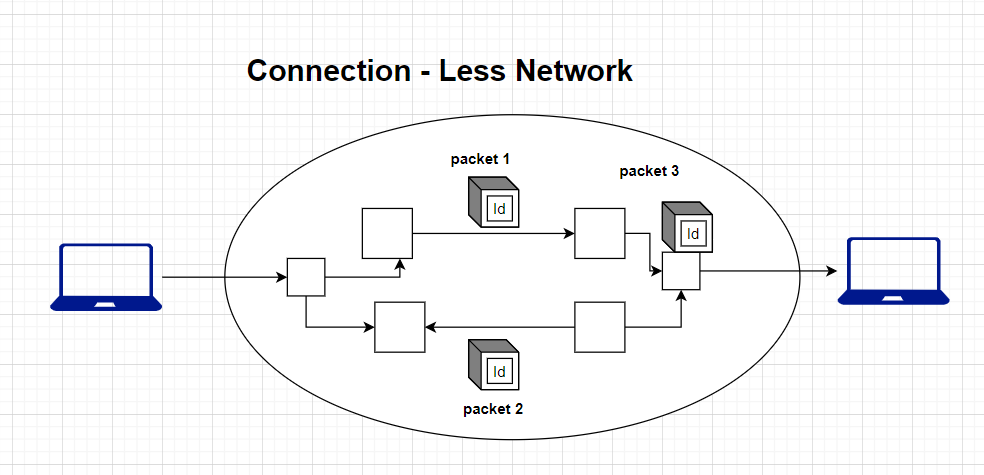
Characteristics of Connection-less Network Service
Here are the key characteristics of connectionless network services:
A) No dedicated connection:
Unlike connection-oriented services, connectionless services do not require the prior establishment and maintenance of a dedicated communication path between sender and receiver. Each data packet is treated independently and can take a different route to its destination.
B) Packet-Based Communication:
Connectionless services operate on a packet-by-packet basis. Data is broken into packets, each containing both the source and destination addresses as well as the actual data payload. These packets are transmitted individually across the network.
C) Independent Routing:
Each packet in a connectionless network contains enough information (source and destination addresses) for routers and switches to independently determine how to forward it toward its destination. This allows packets to take different paths through the network, optimizing routing based on current network conditions.
D) Scalability:
Connectionless networks are more scalable than connection-oriented networks. As each packet carries its own routing information, the network infrastructure can handle a larger number of devices and data flows simultaneously, without the need to allocate resources for connection setup and maintenance.
E) Flexibility in Data Size:
Connectionless services are well-suited for transmitting varying data sizes. They are adaptable to different types of applications and communication needs, from small data transfers to large multimedia streams.
F) Low Latency:
Connectionless networks typically offer lower latency compared to connection-oriented networks. Data packets can be sent immediately, without the delay introduced by connection establishment.
G) Broadcast and Multicast Support:
Connectionless networks are better equipped to handle broadcasting and multicasting, where data is sent to multiple recipients simultaneously. This makes them suitable for scenarios requiring efficient distribution of data to multiple recipients.
Disadvantages of Connection-less Network Service
Here are some of the disadvantages of connectionless network services:
A) Packet Loss and Delivery Issues:
In connectionless networks, there is no guarantee of packet delivery. Packets can be lost due to network congestion, errors, or other issues. This requires additional mechanisms at higher layers to handle retransmissions and ensure reliable data delivery.
B) No Guaranteed Order:
Packets in connectionless networks can take different paths through the network and may arrive at their destination out of order. Applications that require strict ordering of data packets need to implement mechanisms to reorder them correctly.
C) Higher Overhead for Addressing:
Each packet in a connectionless network carries its own source and destination addresses. This can lead to higher overhead compared to connection-oriented networks, where address information is established during connection setup.
D) Complex Error Handling:
Since there is no established connection, error handling becomes more complex in connectionless networks. Lost or corrupted packets require additional error detection and correction mechanisms to ensure data integrity.
E) Limited Support for Quality of Service (QoS):
Connectionless networks may have limitations in providing differentiated levels of Quality of Service (QoS) for different types of traffic. QoS mechanisms, such as prioritization and traffic shaping, are more challenging to implement in connectionless environments.
F) Congestion Management:
In connectionless networks, multiple devices can transmit packets simultaneously, leading to potential network congestion. Proper congestion management mechanisms are essential to prevent performance degradation and ensure fair access to network resources.
Examples of Connection-less Network Services
Here are some examples of connectionless network services:
A) Internet Protocol (IP):
The Internet Protocol is a fundamental example of a connectionless network service. IP packets are individually addressed and routed across the internet without the need for a dedicated connection. Each packet is treated independently, allowing data to traverse different routes to reach its destination.
B) User Datagram Protocol (UDP):
UDP is a connectionless transport protocol that operates on top of IP. It is often used for applications that prioritize low latency over reliable data delivery, such as streaming media, online gaming, and VoIP. UDP packets are sent without establishing a connection and offer minimal overhead compared to connection-oriented protocols.
C) Domain Name System (DNS):
DNS is a connectionless network service used to resolve human-readable domain names into IP addresses. DNS queries and responses are sent as individual packets, making the system scalable and adaptable to changing network conditions.
Difference between Connection-Oriented and Connection-less Network
| Connection Oriented Network | Connection-less Network |
|---|---|
| 1) Before transferring the data, a connection between two devices is mandatory. | 1) Before transferring the data, a connection between two devices is not mandatory. |
| 2) In this type of network, data follows the same path. | 2) In this type of network, packets do not follow the same route. |
| 3) Since it offers a direct connection between sender and receiver during data transfer, there is no congestion. | 3) Lack of an end-to-end link between the source and receiver for the transmission of data packets may cause congestion. |
| 4) It requires a higher bandwidth to transfer the data packets. | 4) It requires a lower bandwidth to transfer the data packets. |
| 5) It requires authentication before transmitting the data packets to the receiver. | 5) It does not require authentication before transmitting the data packets to the receiver. |
FAQ
What is a Connection Oriented network?
Connection oriented networking is a communication paradigm used in computer networks to establish reliable and predictable data transmission between two devices. In connection oriented communication, a logical connection is established before data is exchanged, and this connection remains active until the data exchange is completed. This approach ensures data integrity, order, and efficient flow control.
What is a Connection-Less network?
A connectionless network service is a communication paradigm used in computer networks where data is transmitted between devices without the need for the prior establishment and maintenance of a dedicated connection.
In contrast to connection-oriented networks, where a virtual circuit is set up before data transfer, connectionless networks operate by sending individual packets of data independently, with each packet containing addressing information that allows it to reach its intended destination.
What is the difference between a Connection Oriented and a connection-less network?
Connection Oriented Network:
1. Before transferring the data, a connection between two devices is mandatory.
2. In this type of network, data follows the same path.
3. It requires a higher bandwidth to transfer the data packets.
Connection-Less Network:
1. Before transferring the data, a connection between two devices is not mandatory.
2. In this type of network, packets do not follow the same route.
3. It requires a lower bandwidth to transfer the data packets.
Note:
This Blog has taken its references from this website:
Articles on Computer Networks
- Introduction to Computer Networking | What is Computer Network
- What are Topology & Types of Topology in Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and Its Advantages and Disadvantages
- What is a VPN? How does a VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and Different Types of Viruses in Computer
- What is TCP and its Types and What is TCP three-way Handshake
- What is the UDP Protocol? How does it work and what are its advantages?
- What is an IP and its Functions, What is IPv4 and IPv6 Address
- What is MAC Address and its Types and Difference MAC vs IP
- What is ARP and its Types? How Does it Work and ARP Format
- Sessions and Cookies and the Difference Between Them
- What is the ICMP Protocol and its Message Format?
- What is Big Data? Characteristics and Types of Big Data
- Disciplines of CyberSecurity | What are the goals of CyberSecurity?
- What is Firewall, Features, Types and How does the Firewall Work?
- Network Scanning, Types, and Stealth Scan in Computer Network
- Cryptography and its Types in Ethical Hacking
- Tor Browser and How Does It Work | Onion Router Tutorial
- Proxy Server, Advantages, Difference between Proxy Server & VPN
- DHCP Protocol and What Are the Pros and Cons of DHCP
- Intrusion Detection System(IDS) and What are the types of IDS
- Domain Name Server, How Does It Work, and its advantages
- Telnet: Introduction, How Does it Work, and Its Pros and Cons
- SOC: Introduction, Functions performed by SOC, and its Pros
- What is SIEM? | What is the Difference between SIEM and SOC?
- Application Layer in OSI Model | OSI Model Application Layer
- What is SSL Protocol or SSL/TLS and SSL Handshake, and Architecture of SSL
- What are Servers, how do they work, and its different Types
- Network Devices-Router, Switch, Hub, etc in Computer Network
- Physical Layer in OSI Model | OSI Model Physical Layer
- Presentation Layer in OSI Model | OSI Model Presentation Layer
- Session layer in OSI Model | OSI Model Session layer
- Transport Layer in OSI Model | Computer Network Transport Layer
- Network Layer in OSI Model | OSI Model Network Layer
- Data Link Layer in OSI Model | OSI Model Data Link Layer
Related Articles on Linux
- What is Linux Operating System | Introduction to Linux
- Directory in Linux Define | Linux Directory & its Commands
- Explain the chmod command in Linux | Linux chmod command
- Linux User Management || User Management in Linux
- Linux Computer Network Advanced Command | Network Command
- Redirection in Linux I/O| Linux I/O Redirection
- CronTab and Job Scheduling in Linux | Make CronTab Project
- Linux Firewall Unlock Rules with Firewall-cmd Tutorial
- netstat command in Linux | Linux netstat command
- SSH Command Full Guide with Practical | Linux SSH Service
- awk command Guide | How to arrange the output of the file in Linux
- sed command Full Guide Tutorial | Linux sed Command
- Iptables commands Full Guide: How to make our own Firewall