In this blog, we will learn about the Nessus Vulnerability Scanner. We will see how to use it in the application with practical examples. So let’s get started with the blog.
Table of Contents
- Introduction to Nessus
- Key Features of Nessus
- Practicals with Nessus
- Advantages of Nessus
- Disadvantages of Nessus
- Conclusion
- Related Articles on Computer Networks
- Related Articles on Linux
Introduction to Nessus
Nessus is a widely used vulnerability scanner developed by Tenable Network Security. It is designed to help organizations identify and assess vulnerabilities within their network, systems, and applications.
The scanner is a crucial tool in maintaining the security and integrity of IT environments by identifying potential weaknesses that could be exploited by attackers.
Key Features of Nessus
Here’s an introduction to Nessus and its key features:
1. Vulnerability Scanning:
Nessus performs automated vulnerability scans across a wide range of systems, devices, and applications. It scans for known security vulnerabilities, misconfigurations, and weaknesses in operating systems, software, services, and network protocols.
2. Remote Scanning:
Nessus is capable of conducting remote scanning, allowing it to assess systems and devices over a network without requiring direct physical access. This makes it a valuable tool for assessing the security posture of distributed and complex network environments.
3. Plugin Database:
Nessus uses a vast and regularly updated plugin database to identify vulnerabilities. These plugins contain checks for specific security issues, covering various operating systems, applications, and services. The database includes checks for known vulnerabilities, compliance requirements, and best practices.
4. Customizable Scans:
Users can customize scans based on their specific needs. They can choose scan targets, configure scanning policies, and select the types of vulnerabilities they want to prioritize. This flexibility allows organizations to tailor scans to their unique requirements.
5. Reporting:
After completing a scan, Nessus generates detailed reports that provide information about discovered vulnerabilities, their severity levels, and potential impacts. Reports can be exported in various formats, making it easier to communicate findings to different stakeholders.
6. Compliance Auditing:
Nessus can be used for compliance auditing by checking systems against specific security standards and regulatory requirements, such as CIS benchmarks, HIPAA, PCI DSS, and more. This helps organizations ensure that their systems meet industry-specific security guidelines.
7. Integration with Remediation:
Nessus provides guidance on how to remediate discovered vulnerabilities. It offers recommendations and steps to address the identified weaknesses, enabling organizations to prioritize and take appropriate actions to mitigate risks.
8. Scanning Frequency:
Regular scanning is essential for maintaining security. Nessus can be scheduled to perform scans on a recurring basis, ensuring that new vulnerabilities are promptly identified and addressed.
9. Agent-Based Scanning:
In addition to traditional network scanning, Nessus offers agent-based scanning. Agents are lightweight software components that can be installed on endpoints, allowing for continuous monitoring and scanning even when devices are off the network.
10. User Management:
Nessus supports user roles and permissions, allowing organizations to control access to the scanner and its features. This ensures that only authorized individuals can initiate and manage scans.
Practicals with Nessus
Note: My target system on the IP address is: 127.0.0.1
1) Host Discovery with Nessus
Host discovery is a critical initial step in vulnerability scanning with Nessus. Before conducting vulnerability assessments, you need to identify the active hosts (devices and systems) on your network. Host discovery helps ensure that you’re targeting the right systems for vulnerability scanning and not wasting resources on inactive or offline hosts.
Let’s see an example of host discovery:
Step 1: Click on the “Create a new Scan” Link
Step 2: After clicking on “Create a new Scan”, you will see the option “Host Discovery” Scan.
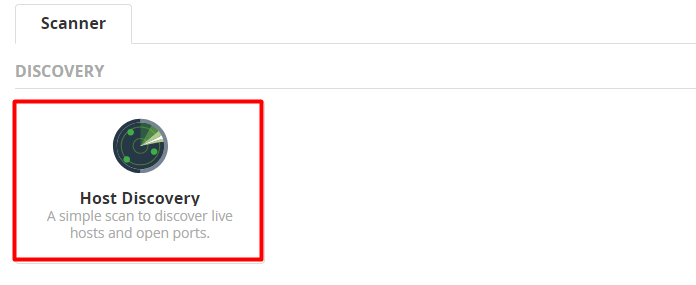
Step 3: Click on the “Host Discovery” Scan Options.
Now you will find some options.
Give any name to your scan. eg: My_First_Discovery_Scan. Also, give a description of the scanning so that even after two or three days, you will remember the purpose of the scan.
In Target option, give your IP address of the other machine i.e, target system. Afterwards click on the save Button.
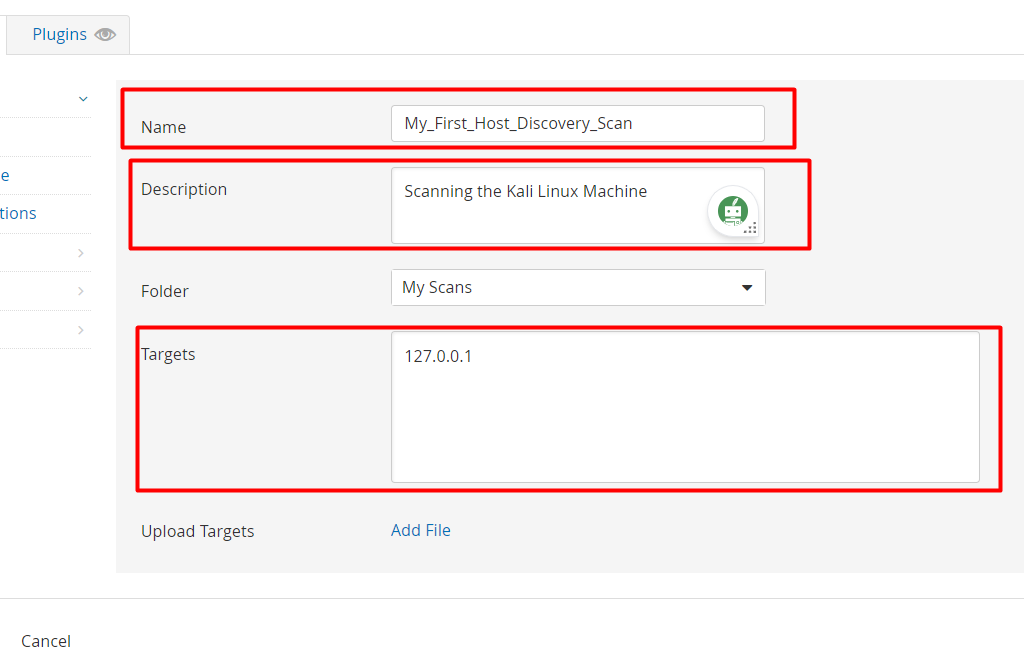
Step 4: After clicking on the Save button, you will redirect to scanning dashboard.
Now, you will see your scan name present in the table.
To scan the target, click on the checkbox button, and click on the “Launch” button which is present on the right side of the row.
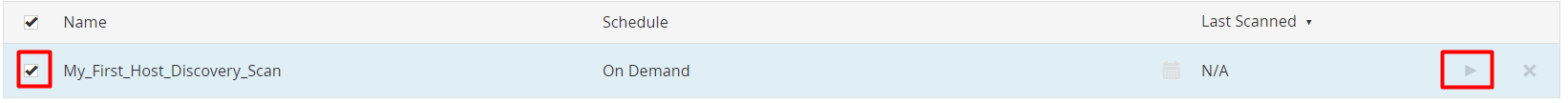
Now, let’s see the result of the Scanning.
Results:
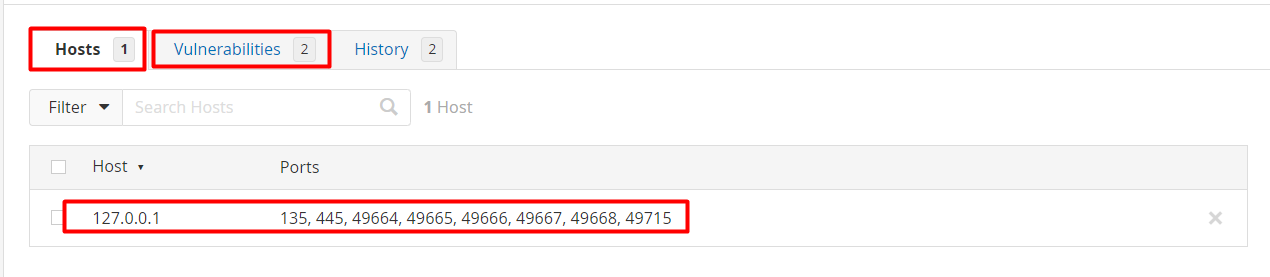
So, here you can see that Hosts have 1 result, while Vulnerabilities have 2 results in the table.
Advantages of Nessus
Nessus offers several advantages that make it a popular choice for vulnerability assessment and management. Here are some of the key advantages of using Nessus:
A) Comprehensive Vulnerability Scanning:
Nessus provides extensive coverage of vulnerabilities, misconfigurations, and security issues across a wide range of operating systems, applications, and network devices. Its plugin database includes checks for known vulnerabilities, compliance standards, and best practices.
B) Accurate Detection:
The accuracy of Nessus scans is generally high due to its regularly updated plugin database and its ability to combine multiple detection techniques such as ICMP ping, TCP ping, and more.
C) Customizable Scans:
Nessus allows users to customize scans based on their specific needs. You can define scan policies, configure targets, choose vulnerability categories to focus on, and set scan schedules according to your organization’s requirements.
D) Compliance Auditing:
Nessus supports compliance scanning against various regulatory standards and security benchmarks. This helps organizations ensure that their systems adhere to industry-specific security requirements and standards.
E) Scalability:
Nessus can be used in both small and large-scale environments. Its ability to handle a large number of scans and targets makes it suitable for enterprises with diverse and extensive network infrastructures.
F) Reporting and Analysis:
Nessus generates detailed and customizable scan reports that provide insights into vulnerabilities, their severity, potential impacts, and suggested remediation steps. These reports are valuable for both technical and non-technical stakeholders.
G) Community and Commercial Versions:
Nessus offers both a free community version and a commercial version with advanced features and support. The community version allows smaller organizations or individuals to benefit from vulnerability scanning without a financial commitment.
In summary, Nessus is a versatile and powerful vulnerability scanner that helps organizations identify and address security weaknesses within their IT infrastructure. Its accuracy, flexibility, and extensive feature set make it a valuable tool for maintaining the security of networks and systems.
Disadvantages of Nessus
. Here are some disadvantages of Nessus:
1) Cost for Commercial Versions:
While there is a free community version of Nessus available, the commercial versions with advanced features, support, and scalability can be relatively expensive. This might be a barrier for smaller organizations with limited budgets.
2) Resource Intensive:
Nessus scans can be resource-intensive, especially when scanning large networks or conducting in-depth assessments. This can lead to increased network traffic, potential performance impacts on scanned systems, and longer scan times.
3) False Positives:
Like any automated vulnerability scanner, Nessus can generate false positive results. It might identify vulnerabilities that don’t actually exist due to its reliance on automated detection techniques. This can lead to wasted time and effort investigating non-existent issues.
4) Limited Application Layer Scanning:
While Nessus excels at identifying vulnerabilities in network services and operating systems, its application layer scanning capabilities might be more limited compared to specialized web application scanners.
5) Limited Network Segmentation Visibility:
Nessus might not be able to fully assess network segments that are isolated from the scanning network. This could result in gaps in vulnerability coverage.
Conclusion
In summary, Nessus is a powerful vulnerability scanner that helps organizations identify and manage security risks within their IT infrastructure. By using Nessus, businesses can proactively address vulnerabilities, reduce the attack surface, and enhance their overall cybersecurity posture.
Related Articles on Computer Networks
- Introduction to Computer Networking | What is Computer Network
- What are Topology & Types of Topology in Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and its advantages and Disadvantages
- What is VPN? How doe VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and different types of Viruses in Computer
- What is TCP and its Types and What is TCP three-way Handshake
- What is UDP Protocol? How does it work and what are its advantages?
- What is an IP and its Functions, What is IPv4 and IPv6 Address
- What is MAC Address and its Types and Difference MAC vs IP
- What is ARP and its Types? How Does it Work and ARP Format
- Sessions and Cookies and the Difference Between Them
- What is ICMP Protocol and its Message Format?
- What is Big Data? Characteristics and Types of Big Data
- Disciplines of CyberSecurity | What are the goals of CyberSecurity?
- What is Firewall, Features, Types and How does the Firewall Work?
- Network Scanning, Types, and Stealth Scan in Computer Network
- Cryptography and its Types in Ethical Hacking
- Tor Browser and How does it Work | Onion Router Tutorial
- Proxy Server, Advantages, Difference between Proxy Server & VPN
- DHCP Protocol and What Are the Pros and Cons of DHCP
- Intrusion Detection System(IDS) and What are the types of IDS
- Domain Name Server, How Does It Work, and its advantages
- Telnet: Introduction, How Does it Work, and Its Pros and Cons
- SOC: Introduction, Functions performed by SOC, and its Pros
- What is SIEM? | What is the Difference between SIEM and SOC?
- Application Layer in OSI Model | OSI Model Application Layer
- What is SSL Protocol or SSL/TLS and SSL Handshake, and Architecture of SSL
- Network Devices-Router, Switch, Hub, etc in Computer Network
- What are Servers, how does it Work, and its different Types
Related Articles on Linux
- What is Linux Operating System | Introduction to Linux
- Directory in Linux Define | Linux Directory & its Commands
- Explain the chmod command in Linux | Linux chmod command
- Linux User Management || User Management in Linux
- Linux Computer Network Advanced Command | Network Command
- Redirection in Linux I/O| Linux I/O Redirection
- CronTab and Job Scheduling in Linux | Make CronTab Project
- Linux Firewall Unlock Rules with Firewall-cmd Tutorial
- netstat command in Linux | Linux netstat command
- SSH Command Full Guide with Practical | Linux SSH Service
- awk command Guide | How to arrange the output of the file in Linux
- sed command Full Guide Tutorial | Linux sed Command
- Iptables commands Full Guide: How to make our own Firewall


