Table of Contents
- Introduction to Computer Networking
- History of Computer Networking
- Features of Computer Networking
- Types of Connections in Computer Networking
- The architecture of Computer Networking
- Components of Computer Networking
- FAQ
- Related Articles on Computer Networks
- Related Articles on Linux
Introduction to Computer Networking
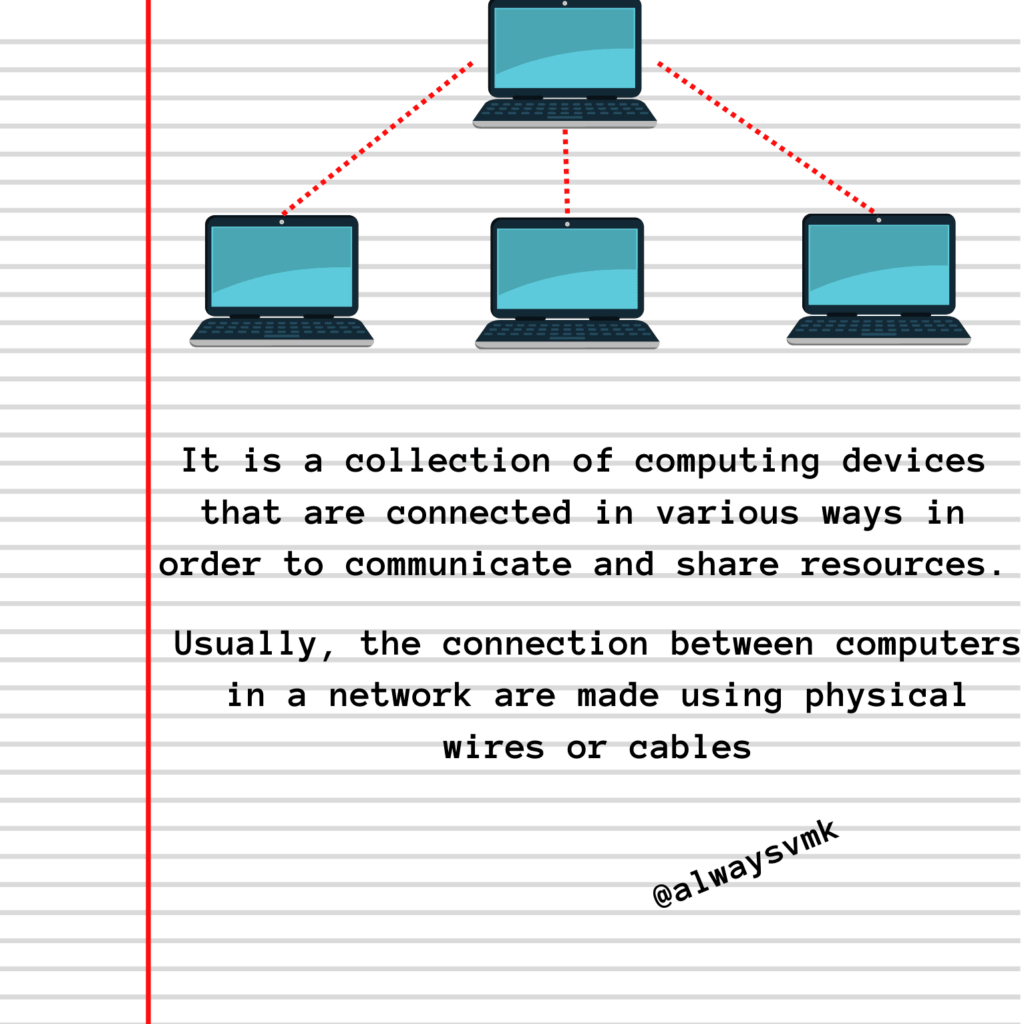
Computer networking is the process of connecting various computing systems and devices so they may communicate with one another.
Hardware, software, and protocols are all part of this process, and they all work together to enable dependable and effective communication between devices. We can now connect and share information in real-time with one another from anywhere in the world because of computer networking, which has completely changed the way we engage with one another.
History of Computer Networking
The history of computer networking dates back to the early 1960s, when the US Department of Defense began developing a computer network that could survive a nuclear attack.
The project, known as ARPANET, was the first successful packet-switching network and formed the basis for developing the modern-day Internet.
In the 1980s and 1990s, the Internet began to take shape, and computer networking became more widespread as businesses and individuals began to connect to the Internet.
With the rise of the World Wide Web in the mid-1990s, the Internet became the primary means of accessing and sharing information, leading to a proliferation of online services and applications.
Today, computer networking is an essential part of our daily lives, with billions of devices connected to the Internet and an endless stream of data flowing between them.
Features of Computer Networking
Computer networking is the process of connecting multiple computers, devices, and other components to enable them to share data, resources, and services. Some of the key features of computer networking are:
A) Connectivity
Computer networking enables devices to connect and communicate with each other, allowing for the sharing of resources and data.
B) Scalability
Computer networks can be easily scaled up or down, depending on the size of the network and the number of users.
C) Reliability
A reliable computer network is crucial for businesses and organizations to ensure that data is available and accessible when it is needed.
D) Security
Computer networks must be secure to protect against unauthorized access and data breaches. Security measures include firewalls, encryption, and access control.
E) Flexibility
Peer-to-peer networks and client-server networks are two examples of how computer networks can be set up to cater to the unique requirements of various users.
F) Management
In order for computer networks to function properly and efficiently, they must be managed and monitored continuously. This includes keeping track of network performance, locating problems, fixing them, and putting new features in place.
Types of Connections in Computer Networking
For more detailed information about connections in computer networks. Click here
There are two types of connections in Computer networking, which are as follows:
A) Connection-Oriented Network
In a connection-oriented network, communication between devices follows a structured and organized process, which involves establishing a dedicated connection before data transmission begins. This connection is maintained throughout the entire data exchange, and it is only released when the communication is complete.
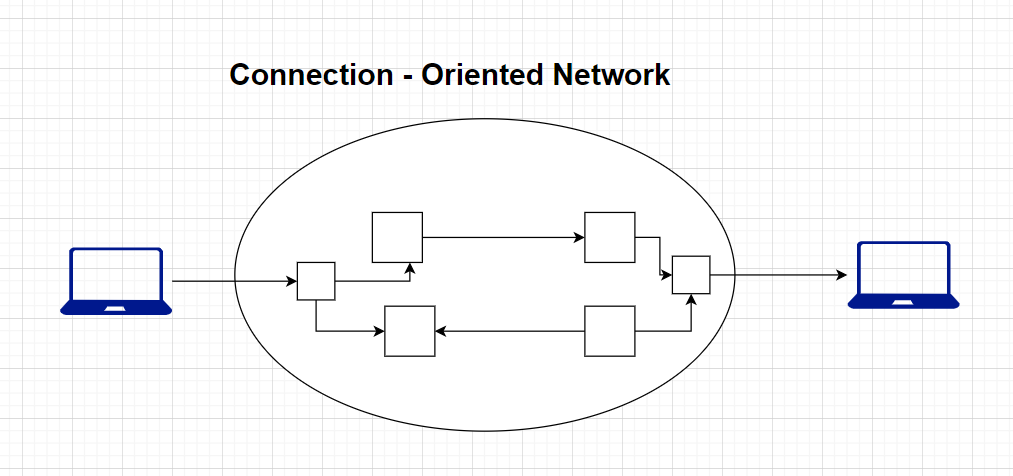
- Examples: TCP (Transmission Control Protocol) is a prime example of a connection-oriented protocol used on the Internet. TCP establishes a connection, guarantees the delivery of data, and ensures data integrity.
- Use Cases: Connection-oriented networks are suitable for applications where data integrity and reliability are critical, such as web browsing, email, file transfer, and most internet-based services.
b) Connection-less Network
In a connectionless network, communication between devices is more decentralized and less structured. Devices send data packets independently, without establishing a dedicated connection or maintaining a continuous relationship with the recipient.
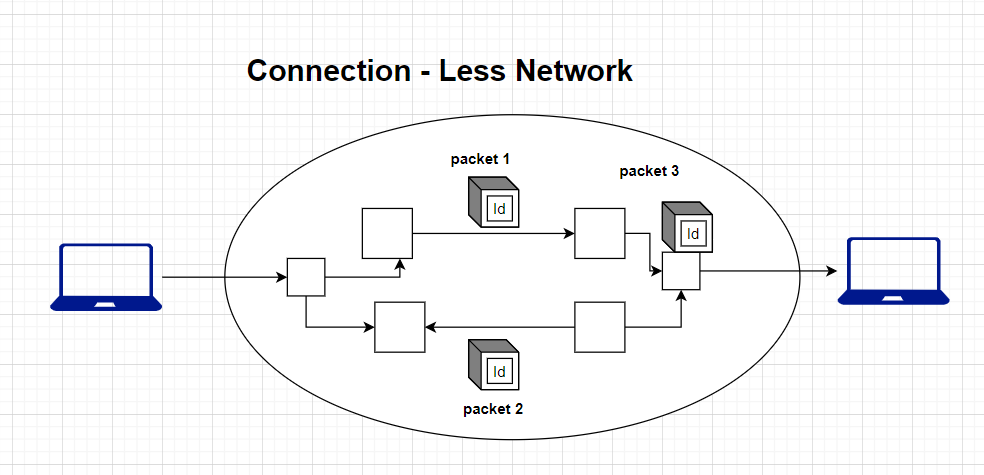
- Examples: UDP (User Datagram Protocol) is a widely used connectionless protocol in networking. It does not establish a connection, and it does not guarantee the delivery or order of data packets.
- Use Cases: Connectionless networks are suitable for applications where real-time or low-latency communication is essential, such as video streaming, online gaming, VoIP (Voice over IP), and situations where minor data loss is acceptable.
The architecture of Computer Networking
The physical and logical architecture of the software, hardware, protocols, and data transmission media is referred to as the computer network architecture. That is, how tasks are assigned to computers and how computers are organized.
There are two types of computer networks used, which are:
- Peer-to-Peer Network
- Client-Server Network.
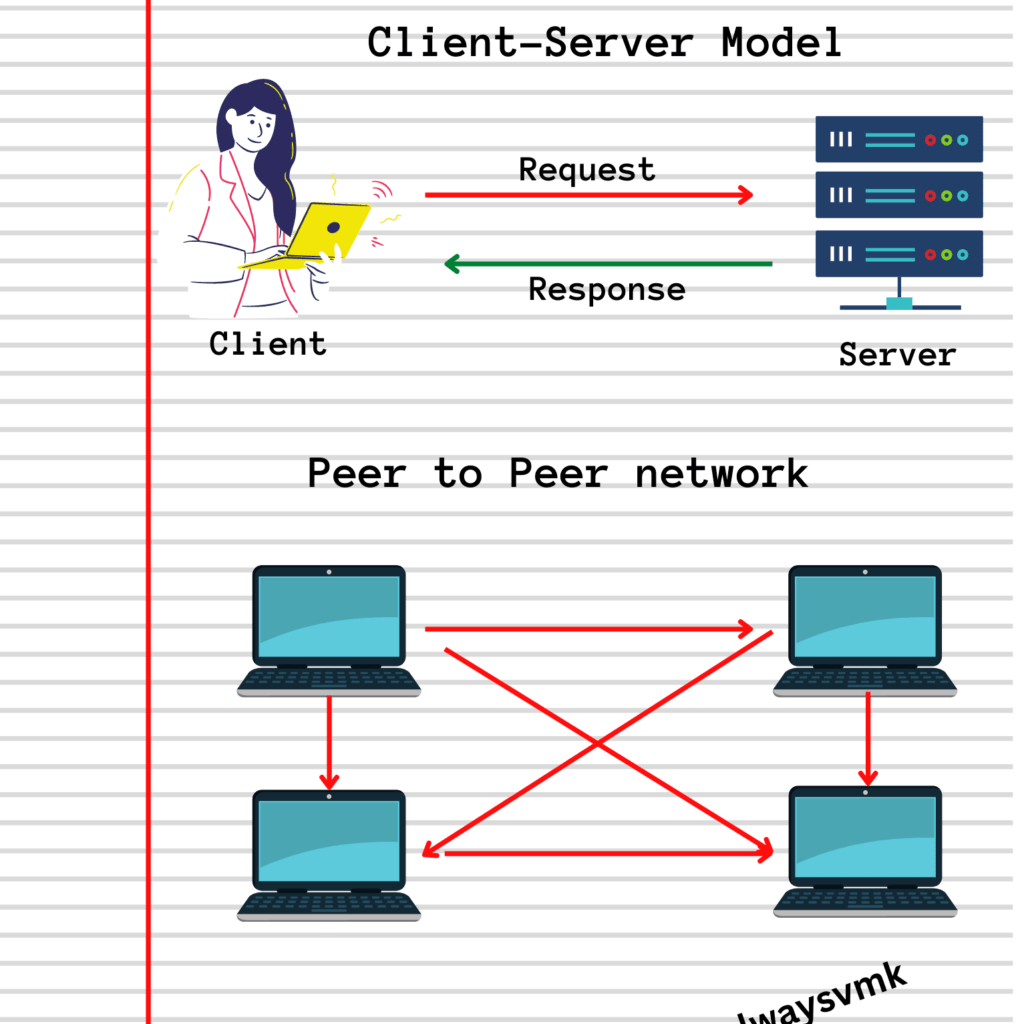
A) Peer-to-Peer Network (P2P)
A peer-to-peer network is a decentralized network where all devices in the network have equal status and communicate with each other directly, without the need for a central server. Each device in the network can act as both a client and a server, meaning that it can request resources from other devices in the network and provide resources to other devices as well.
Examples of P2P networks include file-sharing networks like BitTorrent and cryptocurrency networks like Bitcoin.
Advantages of Peer-to-Peer Network
- Decentralized: P2P networks are decentralized, which means there is no central point of failure. If one node goes down, the other nodes can continue to operate and share resources.
- Cost-effective: P2P networks are cost-effective because there is no need for a centralized server, which means lower infrastructure costs.
- Faster downloads: P2P networks can provide faster downloads for large files because they allow multiple sources for the same file, enabling parallel downloads.
- Scalability: P2P networks can be easily scaled by adding more nodes to the network.
Disadvantages of Peer-to-Peer Network
- Security: P2P networks can be vulnerable to security threats, such as malware and hacking because they rely on untrusted peers to share resources.
- Reliability: The reliability of P2P networks depends on the number of nodes in the network. If there are not enough nodes, the network may be slow or not work at all.
- Bandwidth usage: P2P networks consume a lot of bandwidth because they rely on each peer to share data with other peers. This can result in slow internet speeds for other users.
- Legal issues: P2P networks have been associated with illegal file sharing, which can lead to legal issues for users who participate in such activities.
B) Client-Server Network
A client-server network is a centralized network where a server provides services to clients. Clients in a client-server network are typically end-user devices, like computers or mobile phones, that request services or resources from a central server. The server manages and delivers these resources, and clients do not communicate with each other directly.
Examples of client-server networks include web servers and email servers.
Advantages of Client-Server Network
- Centralized control: A client-server network provides centralized control over network resources, which allows for easier management and maintenance of the network.
- Scalability: Client-server networks can be easily scaled by adding more clients or servers as needed.
- Security: Client-server networks are more secure than P2P networks because they provide centralized control over network resources, which makes it easier to monitor and manage access to those resources.
- Reliability: Client-server networks are more reliable than P2P networks because they rely on a central server that can provide redundancy and backup services.
Disadvantages of Client-Server Network
- Cost: Client-server networks can be expensive to set up and maintain because they require a central server and dedicated network infrastructure.
- Dependence on the central server: Client-server networks depend on the central server to provide services and resources. If the server goes down, the entire network can be affected.
- Performance: Client-server networks can be slower than P2P networks because they rely on a central server to provide services and resources, which can create network bottlenecks.
- Limited scalability: Client-server networks can be limited in their scalability because they rely on a central server, which can become a bottleneck if the network grows too large.
Components of Computer Networking
There are several key components in the architecture of computer networking:
Network topology:
The topology of a network refers to the way the devices are connected to each other. There are several different topologies, including bus, star, mesh, and ring.
Network protocols:
Protocols are the rules that govern how devices communicate with each other. There are many different protocols used in computer networking, such as TCP/IP, HTTP, FTP, and SSH.
Network hardware:
The hardware components of a network include routers, switches, hubs, and other devices that are used to connect the various devices in the network.
Network software:
The software components of a network include operating systems, drivers, applications, and other programs that are used to manage and control the network.
Network services:
Services are programs or processes that provide specific functionality to the network, such as file sharing, email, or remote access.
Network security:
Security is an important aspect of computer networking architecture. There are many different security measures that can be implemented to protect a network from unauthorized access, such as firewalls, intrusion detection systems, and encryption.
Note: This blog is mainly based on Wikipedia.
FAQ
What is meant by computer networking?
Computer networking is the process of connecting various computing systems and devices so they may communicate with one another.
Hardware, software, and protocols are all part of this process, and they all work together to enable dependable and effective communication between devices. We can now connect and share information in real time with one another from anywhere in the world because of computer networking, which has completely changed the way we engage with one another.
What are the advantages of computer networking?
The advantages of computer networking are:
A) Connectivity
Computer networking enables devices to connect and communicate with each other, allowing for the sharing of resources and data.
B) Scalability
Computer networks can be easily scaled up or down, depending on the size of the network and the number of users.
C) Reliability
A reliable computer network is crucial for businesses and organizations to ensure that data is available and accessible when it is needed.
What are the different types of connections in computer networks?
There are two types of connections in Computer networking, which are as follows:
A) Connection-Oriented Network
In a connection-oriented network, communication between devices follows a structured and organized process, which involves establishing a dedicated connection before data transmission begins. This connection is maintained throughout the entire data exchange, and it is only released when the communication is complete.
Examples: TCP (Transmission Control Protocol) is a prime example of a connection-oriented protocol used on the Internet.
b) Connection-less Network
In a connectionless network, communication between devices is more decentralized and less structured. Devices send data packets independently, without establishing a dedicated connection or maintaining a continuous relationship with the recipient.
Examples: UDP (User Datagram Protocol) is a widely used connectionless protocol in networking. It does not establish a connection, and it does not guarantee the delivery or order of data packets.
Related Articles on Computer Networks
- What are Topology & Types of Topology in Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and Its Advantages and Disadvantages
- What is VPN? How doe VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and different types of Viruses in Computer
- What is TCP and its Types and What is TCP three-way Handshake
- What is UDP Protocol? How does it work and what are its advantages?
- What is an IP and its Functions, What is IPv4 and IPv6 Address
- What is MAC Address and its Types and Difference MAC vs IP
- What is ARP and its Types? How Does it Work and ARP Format
- Sessions and Cookies and the Difference Between Them
- What is ICMP Protocol and its Message Format?
- What is Big Data? Characteristics and Types of Big Data
- Disciplines of CyberSecurity | What are the goals of CyberSecurity?
- What is Firewall, Features, Types and How does the Firewall Work?
- Network Scanning, Types, and Stealth Scan in Computer Network
- Cryptography and its Types in Ethical Hacking
- Tor Browser and How does it Work | Onion Router Tutorial
- Proxy Server, Advantages, Difference between Proxy Server & VPN
- DHCP Protocol and What Are the Pros and Cons of DHCP
- Intrusion Detection System(IDS) and What are the types of IDS
- Domain Name Server, How Does It Work, and its advantages
- Telnet: Introduction, How Does it Work, and Its Pros and Cons
- SOC: Introduction, Functions performed by SOC, and its Pros
- What is SIEM? | What is the Difference between SIEM and SOC?
- Application Layer in OSI Model | OSI Model Application Layer
- What is SSL Protocol or SSL/TLS and SSL Handshake, and Architecture of SSL
Related Articles on Linux
- What is Linux Operating System | Introduction to Linux
- Directory in Linux Define | Linux Directory & its Commands
- Explain the chmod command in Linux | Linux chmod command
- Linux User Management || User Management in Linux
- Linux Computer Network Advanced Command | Network Command
- Redirection in Linux I/O| Linux I/O Redirection
- CronTab and Job Scheduling in Linux | Make CronTab Project
- Linux Firewall Unlock Rules with Firewall-cmd Tutorial
- netstat command in Linux | Linux netstat command
- SSH Command Full Guide with Practical | Linux SSH Service
- awk command Guide | How to arrange the output of the file in Linux
- sed command Full Guide Tutorial | Linux sed Command
- Iptables commands Full Guide: How to make our own Firewall