In this blog, we will see all the important network devices present in the Computer Network. So we will see routers, switches, hubs, bridges, repeaters, and NICs (Network Interface cards) with their advantages and disadvantages in Computer Networks. So let’s get started with the blog.
Table of Contents
- Introduction to Network Devices
- List of Network Devices in Computer Network
- Difference between Hub, Switch, and Router
- FAQ
- Articles on Computer Networks
- Related Articles on Linux
Introduction to Network Devices
Network devices are essential components within a computer network that facilitate communication, data exchange, and efficient network management.
These devices play crucial roles in ensuring seamless connectivity, secure data transmission, and the overall functionality of modern computer networks.
List of Network Devices in Computer Network
A) Router
A router is a vital networking device that serves as a connection point between different networks, enabling data to travel between them. It plays a pivotal role in directing data traffic efficiently and ensuring that information reaches its intended destination accurately.
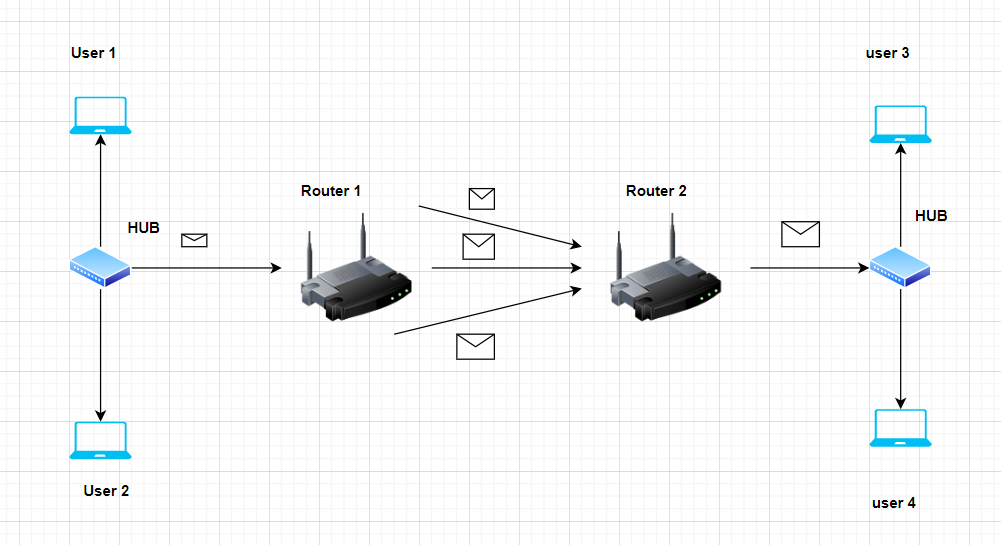
Let’s see the workings of the Router in the Computer Network:
A) Packet Reception:
Routers receive data packets from various devices connected to the local network or from external networks, such as the Internet, or the HUB. Each data packet contains source and destination IP addresses, among other information.
B) IP Address Inspection:
The router examines the destination IP address within the packet’s header to determine the next hop or destination network for the packet. This process involves checking the router’s routing table, which contains information about how to reach different networks.
C) Routing Decision:
Based on the destination IP address and the information in its routing table, the router makes a routing decision. This decision determines which interface the packet should be sent out of or which next-hop router it should be forwarded to.
And this way, it reaches Router 2, and from that it reaches its destination.
For more information learn the Routing in Computer Network.
Advantages of Routers:
- Efficient Data Routing: Routers make intelligent decisions about how to route data packets, ensuring that they take the most efficient path to reach their destination. This optimization helps prevent network congestion and ensures timely data delivery..
- Network Segmentation: Routers enable network segmentation through the use of subnets or virtual LANs (VLANs). This enhances security and simplifies network management by separating devices into distinct segments.
- Dynamic Routing: Routers support dynamic routing protocols that allow them to adapt to changes in the network’s topology. This ensures that data continues to flow efficiently even when network conditions change.
- Load Balancing: Advanced routers can distribute traffic across multiple paths or connections, optimizing resource usage and preventing overloading on a single path.
- Redundancy and Failover: Routers can be set up in redundant configurations, ensuring network availability even if one router fails. This improves network reliability.
Disadvantages of Routers:
- Complexity: Routers can be complex to set up and configure properly, especially in larger networks. Proper configuration requires understanding routing protocols, IP addressing, and network topology.
- Cost: Routers can be expensive, especially advanced models with features like QoS, load balancing, and security. This can be a significant investment for small businesses or individuals.
- Maintenance: Routers require regular maintenance and updates to ensure optimal performance and security. This can be time-consuming and may require skilled IT personnel.
- Potential Single Point of Failure: In some network setups, a router could become a single point of failure. If the router goes down, all connected networks might lose connectivity.
B) Hub
A hub is a simple networking device that was historically used to connect multiple devices within a local area network (LAN). Its primary function is to provide a central point for device connectivity by allowing multiple devices, such as computers, printers, and servers, to be linked together.
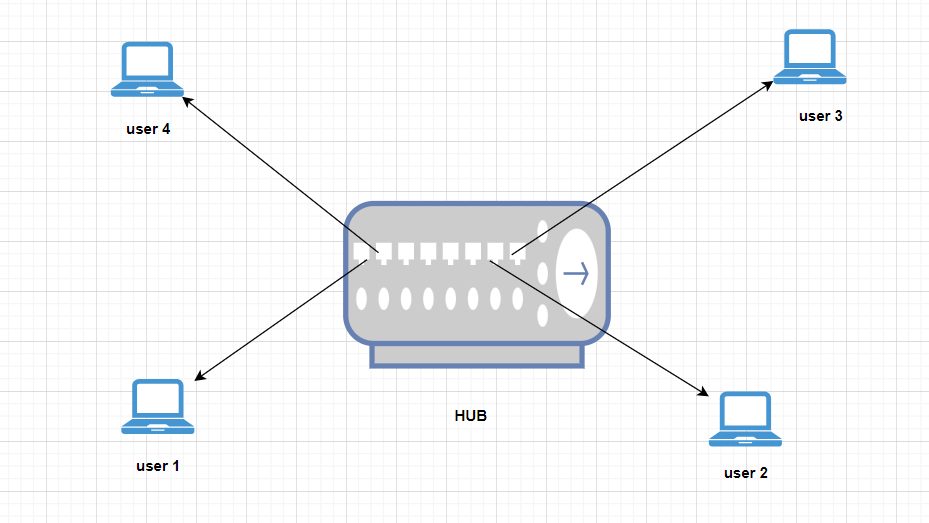
Let’s see how the HUB works in Computer Networks:
Physical Connectivity: A hub typically has multiple ports (e.g., 4, 8, 16 ports) where network cables from various devices, such as computers, printers, or switches, can be connected. Hubs are often used in small, simple networks.
Broadcasting to All Ports: The hub broadcasts the incoming data packet to all of its connected ports, regardless of the intended recipient. This means that all devices connected to the hub will receive and process the data packet.
Note: If one of the systems fails, it does not affect other Users, if a Central HUB is failed then all of the users also fail.
Advantages of Hubs:
- Simplicity: Hubs are straightforward to set up and require minimal configuration. They can be a simple solution for small, basic networks.
- Low Cost: Hubs are generally less expensive than more advanced networking devices like switches or routers.
- Basic Connectivity: Hubs can serve as a basic means of connecting devices within a network, especially in environments with limited networking needs.
- Passive Device: Hubs are passive devices, meaning they do not require power or active management. They are less likely to fail due to power issues.
Disadvantages of Hubs:
- Data Broadcasting: Hubs broadcast data to all connected devices, regardless of whether the data is intended for a specific device. This results in inefficient use of bandwidth.
- Shared Bandwidth: Since all devices connected to a hub share the same bandwidth, network performance can be severely impacted as more devices communicate simultaneously.
- Collision Domain: Hubs create a single collision domain, leading to more collisions in network traffic and potentially degrading network performance.
- Limited Network Management: Hubs lack the intelligence and features needed for effective network management, making them unsuitable for networks that require proper segmentation and control.
C) Switch
A switch is a crucial networking device that plays a fundamental role in connecting devices within a local area network (LAN). Unlike hubs, which are considered outdated, switches operate at a higher level of intelligence, making data transmission more efficient and enhancing network performance.
It is generally used to send private data, and there is no waste of data.
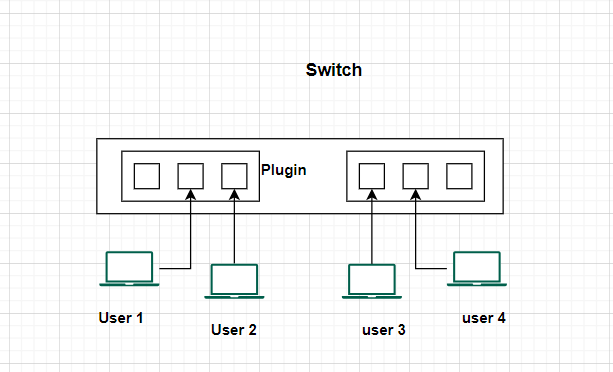
Let’s see how the switch works in a computer network:
- Physical Connectivity: A switch typically has multiple ports (e.g., 8, 16, 24, 48 ports) where network cables from various devices, such as computers, printers, servers, and other switches, can be connected. These devices can be part of the same LAN.
- Learning MAC Addresses: When a device is connected to a switch, the switch learns about the MAC addresses of the devices connected to its ports. This learning process is automatic and dynamic. As devices send data packets, the switch examines the source MAC address in each packet and records it in its MAC address table (also known as a MAC address forwarding table or CAM table). This table helps the switch make informed forwarding decisions.
Advantages of Switches:
- Efficient Data Forwarding: Switches make intelligent decisions about where to forward data based on MAC addresses, resulting in efficient data transmission and reduced network congestion.
- Reduced Collisions: Each port on a switch creates its own collision domain, minimizing the chances of data collisions that can lead to performance degradation.
- Unicast Communication: Switches enable unicast communication, sending data only to the specific device for which it is intended. This eliminates the unnecessary broadcast traffic associated with hubs.
- Improved Bandwidth Utilization: Switches allow simultaneous data transmission among devices without collisions, optimizing available bandwidth and improving overall network performance.
Disadvantages of Switches:
- Cost: Managed switches with advanced features can be expensive, particularly for smaller networks or environments with budget constraints.
- Complexity: Managed switches require proper configuration and management. For less experienced users, the complexity of these devices can lead to misconfigurations or potential security vulnerabilities.
- Device Dependence: Switches rely on devices to provide MAC addresses, and if a device’s MAC address is incorrect or changes, it can lead to network issues.
- Single Point of Failure: While switches can improve network availability, a single switch failure can still disrupt network connectivity.
D) Bridge
A bridge is a networking device that operates at the data link layer (Layer 2) of the OSI model and is used to connect and filter traffic between two or more network segments. Bridges are designed to enhance network performance, manage traffic, and improve overall efficiency.
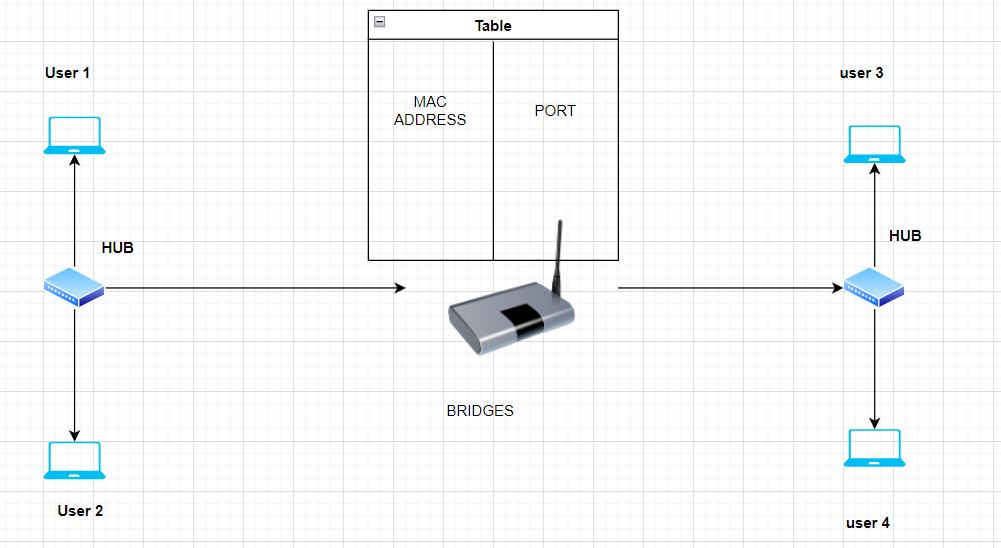
Let us see how Bridges works in Computer Network:
- Physical Connectivity: A bridge has two or more network interfaces, each connected to a different network segment. These network segments can be separate LANs or distinct segments within the same LAN.
- Learning MAC Addresses: When a bridge is initially powered on or connected to the network, it starts with an empty MAC address table. As data frames pass through the bridge, it examines the source MAC addresses of these frames. The bridge records these MAC addresses in its MAC address table, associating each address with the port on which it was received. This process allows the bridge to learn the MAC addresses of devices on both sides of the bridge.
- Forwarding Decisions: When a device connected to one segment of the bridge wants to send data to a device on another segment, it sends the data as a frame. The bridge examines the destination MAC address in the frame’s header.
Advantages of Bridges:
- Segment Isolation: Bridges help isolate network segments, reducing the size of collision domains and preventing collisions from affecting the entire network. This leads to improved network performance.
- Broadcast Control: Bridges filter and control broadcast traffic, preventing unnecessary broadcasts from propagating across segments and reducing network congestion.
- Network Segmentation: Bridges allow network administrators to segment larger networks into smaller, more manageable segments, improving network organization and management.
- Collision Reduction: Bridges reduce collisions by separating segments. Devices within each segment can communicate without the risk of collisions caused by devices in other segments.
- Scalability: Bridges facilitate network expansion by connecting multiple segments together, allowing for the growth of network infrastructure without a complete overhaul.
Disadvantages of Bridges:
- Limited Intelligence: Bridges operate at a lower level of intelligence compared to modern switches. They make forwarding decisions based solely on MAC addresses, lacking the more advanced features of switches.
- Broadcast Propagation: While bridges control broadcast traffic within segments, broadcasts can still propagate within a segment and potentially cause network congestion.
- Reduced Efficiency: While bridges improve network performance compared to having a single large collision domain, they still don’t offer the efficiency and performance capabilities of switches.
- Obsolete Technology: Like hubs, bridges are considered outdated in modern network environments. Switches have largely replaced bridges due to their more advanced features and capabilities.
- Limited Management: Bridges lack the comprehensive management capabilities of managed switches. They do not offer the same level of monitoring, control, and configuration.
E) Repeater
A repeater is a networking device used to extend the distance of a network’s physical transmission medium, such as a coaxial cable or twisted-pair cable. Its primary purpose is to regenerate and amplify signals to overcome signal degradation and maintain the integrity of data as it travels over longer distances.
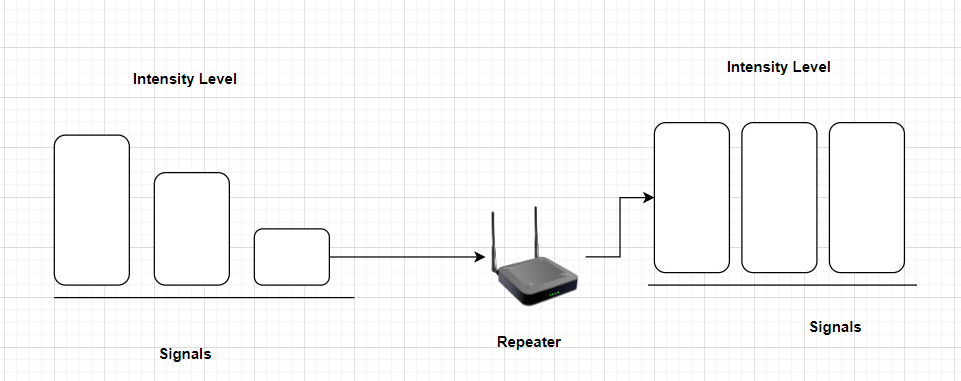
How does Repeater work in computer networks?
- Signal Reception: The repeater receives data signals from one network segment. This could be a wired connection (e.g., Ethernet cable) or a wireless connection (e.g., Wi-Fi).
- Signal Amplification: The primary function of a repeater is to amplify the received signal. Over long distances, data signals can weaken due to factors like cable attenuation, electromagnetic interference, and signal loss in wireless communication. The repeater boosts the signal strength to overcome these losses.
- Signal Regeneration: In addition to amplifying the signal, the repeater may also regenerate the signal. This process involves cleaning up the signal by removing noise and other distortions that may have been introduced during transmission.
Advantages of Repeaters:
- Signal Extension: Repeaters extend the reach of a network by regenerating and amplifying signals. They allow data to travel longer distances without significant signal degradation.
- Simple Implementation: Repeaters are simple devices that require minimal configuration. They are relatively easy to install and use.
- Cost-Effective: Repeaters are generally less expensive than more advanced networking devices like switches or routers.
Disadvantages of Repeaters:
- Limited Functionality: Repeaters operate only at the physical layer of the OSI model, focusing solely on signal regeneration. They lack the intelligence to handle higher-layer network functions like filtering or routing.
- No Collisions Handling: Repeaters do not address issues related to data collisions. In modern Ethernet networks, collisions are better managed by switches.
- Obsolete Technology: With the transition to newer networking technologies like fiber optics and twisted-pair Ethernet, the need for repeaters has greatly diminished. These newer technologies offer longer transmission distances and better signal quality.
- No Error Handling: Repeaters don’t have error detection or correction mechanisms. Data errors that occur before the repeater are simply amplified and passed along.
- Single Point of Failure: In networks with multiple repeaters, a failure in one repeater can disrupt the entire network segment beyond that point.
F) NIC (Network Interface Card)
A Network Interface Card (NIC), also known as a network adapter or network interface controller, is a hardware component that connects a computer or device to a network.
It serves as the bridge between the computer’s internal data processing and external network data communication. A NIC is an essential component for enabling communication between devices within a network, whether it’s a local area network (LAN), a wide area network (WAN), or even a wireless network.
Advantages of NICs:
- Network Connectivity: NICs provide the essential hardware connection that allows computers to communicate with each other within a network, enabling data exchange and resource sharing.
- Flexible Media Support: NICs come in various types to support different network media, including Ethernet cables, fiber optics, and wireless signals. This flexibility allows devices to connect via the most suitable medium for their environment.
- Speed and Performance: Modern NICs support different data transfer rates, enabling networks to achieve higher speeds for data transmission.
- Hardware Identification: NICs have unique MAC addresses, which help identify devices on the network and prevent address conflicts.
- Easy Installation: NICs are relatively easy to install. They can be installed as internal expansion cards or external devices via USB or other ports.
Disadvantages of NICs:
- Compatibility Issues: NICs must be compatible with the network medium and protocols in use. Mismatched NICs can lead to connectivity problems.
- Driver Dependency: NICs require drivers to interface with the operating system. Outdated or incompatible drivers can cause connectivity issues or limit performance.
- Hardware Failures: Like any hardware component, NICs can fail over time. A faulty NIC can lead to network connectivity problems or complete network outages for the affected device.
- Limited Wireless Range: Wireless NICs are subject to signal limitations and interference, affecting their range and performance.
- Security Concerns: NICs have unique MAC addresses, which can be used for tracking and identification, potentially raising privacy concerns.
- Speed Limitations: The performance of a network is limited by the slowest NIC on it. Older or slower NICs can impact the overall network speed.
Difference between Hub, Switch, and Router
| Hub | Switch | Router |
|---|---|---|
| Operates at the physical layer (Layer 1) of the OSI model. | Operates at the data link layer (Layer 2) of the OSI model. | Operates at the network layer (Layer 3) of the OSI model. |
| Broadcasts data to all connected devices. | Makes intelligent decisions about data forwarding based on MAC addresses. | Routes data between different networks based on IP addresses. |
| Shared bandwidth among connected devices. | Each port has dedicated bandwidth. | Manages traffic between networks, providing logical separation and efficient data routing. |
| Creates a single collision domain. | Creates separate collision domains for each port, minimizing collisions and improving network performance. | Does not create collision domains as switches do. Prevents collisions by routing data between networks. |
| Outdated and not recommended for modern networks due to inefficiency and security issues. | Essential for modern networks, offering efficient data transmission, improved security, and network management. | Used to connect multiple networks, including LANs and WANs. Essential for internet connectivity and interconnecting networks. |
FAQ
What are routers in a computer network?
A router is a vital networking device that serves as a connection point between different networks, enabling data to travel between them. It plays a pivotal role in directing data traffic efficiently and ensuring that information reaches its intended destination accurately.
What are Switches in a Computer Network?
A switch is a crucial networking device that plays a fundamental role in connecting devices within a local area network (LAN). Unlike hubs, which are considered outdated, switches operate at a higher level of intelligence, making data transmission more efficient and enhancing network performance.
What are bridges in a computer network?
A bridge is a networking device that operates at the data link layer (Layer 2) of the OSI model and is used to connect and filter traffic between two or more network segments. Bridges are designed to enhance network performance, manage traffic, and improve overall efficiency.
What is a hub in a computer network?
A hub is a simple networking device that was historically used to connect multiple devices within a local area network (LAN). Its primary function is to provide a central point for device connectivity by allowing multiple devices, such as computers, printers, and servers, to be linked together.
What are Repeaters in Computer Networks?
A repeater is a networking device used to extend the distance of a network’s physical transmission medium, such as a coaxial cable or twisted-pair cable. Its primary purpose is to regenerate and amplify signals to overcome signal degradation and maintain the integrity of data as it travels over longer distances.
Articles on Computer Networks
- Introduction to Computer Networking | What is Computer Network
- What are Topology & Types of Topology in Computer Network
- What is FootPrinting in Cyber Security and its Types, Purpose
- Introduction to Cloud Computing | What is Cloud Computing
- Distributed Shared Memory and Its Advantages and Disadvantages
- What is a VPN? How does a VPN Work? What VPN should I use?
- What is an Internet and How the Internet Works
- What is a Website and How Does a Website or web work?
- Introduction to Virus and Different Types of Viruses in Computer
- What is TCP and its Types and What is TCP three-way Handshake
- What is the UDP Protocol? How does it work and what are its advantages?
- What is an IP and its Functions, What is IPv4 and IPv6 Address
- What is MAC Address and its Types and Difference MAC vs IP
- What is ARP and its Types? How Does it Work and ARP Format
- Sessions and Cookies and the Difference Between Them
- What is the ICMP Protocol and its Message Format?
- What is Big Data? Characteristics and Types of Big Data
- Disciplines of CyberSecurity | What are the goals of CyberSecurity?
- What is Firewall, Features, Types and How does the Firewall Work?
- Network Scanning, Types, and Stealth Scan in Computer Network
- Cryptography and its Types in Ethical Hacking
- Tor Browser and How Does It Work | Onion Router Tutorial
- Proxy Server, Advantages, Difference between Proxy Server & VPN
- DHCP Protocol and What Are the Pros and Cons of DHCP
- Intrusion Detection System(IDS) and What are the types of IDS
- Domain Name Server, How Does It Work, and its advantages
- Telnet: Introduction, How Does it Work, and Its Pros and Cons
- SOC: Introduction, Functions performed by SOC, and its Pros
- What is SIEM? | What is the Difference between SIEM and SOC?
- Application Layer in OSI Model | OSI Model Application Layer
- What is SSL Protocol or SSL/TLS and SSL Handshake, and Architecture of SSL
- What are Servers, how do they work, and its different Types
- Connection Oriented and Connection-less Services in Network
- Physical Layer in OSI Model | OSI Model Physical Layer
- Presentation Layer in OSI Model | OSI Model Presentation Layer
- Session layer in OSI Model | OSI Model Session layer
- Transport Layer in OSI Model | Computer Network Transport Layer
- Network Layer in OSI Model | OSI Model Network Layer
- Data Link Layer in OSI Model | OSI Model Data Link Layer
- Block Diagram of Communication System with Detailed Explanation
Related Articles on Linux
- What is Linux Operating System | Introduction to Linux
- Directory in Linux Define | Linux Directory & its Commands
- Explain the chmod command in Linux | Linux chmod command
- Linux User Management || User Management in Linux
- Linux Computer Network Advanced Command | Network Command
- Redirection in Linux I/O| Linux I/O Redirection
- CronTab and Job Scheduling in Linux | Make CronTab Project
- Linux Firewall Unlock Rules with Firewall-cmd Tutorial
- netstat command in Linux | Linux netstat command
- SSH Command Full Guide with Practical | Linux SSH Service
- awk command Guide | How to arrange the output of the file in Linux
- sed command Full Guide Tutorial | Linux sed Command
- Iptables commands Full Guide: How to make our own Firewall